sveinan
Occasional Visitor
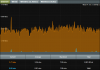
I like to understand who is doing what through my WAN/internet traffic (equipment in my signature). Was doing a review of connections/traffic in my network. Elimination and so on. But after removing all cables from my RT-AC66U, factory default, and turning off wireless. Only leaving WAN and my PC or laptop physically connected (alternating between them). I still get a constant 3KB/s traffic indicated through Traffic Monitor:
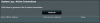
At the same point in time, no active connections indicated (have pressed 'Refresh'):
Was about to give up. Then tried to turn on 'Logged packets type:' to 'Both' (under Firewall / General). That gave me a continuous stream of following entries in System Log:
Not an expert on this. But I am guessing this indicates some type of broadcast packets, about 3 per second, from/through my Cabel Modem against my WAN port on RT-AC66U. Looks to match the 3KB/s traffic indicated.
Soo, does this look logical ? Anybody more experienced that could clue me inn to what kind of situation/traffic I am looking at ?

At the same point in time, no active connections indicated (have pressed 'Refresh'):
Was about to give up. Then tried to turn on 'Logged packets type:' to 'Both' (under Firewall / General). That gave me a continuous stream of following entries in System Log:
Code:
Apr 2 12:49:45 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50059 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:46 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50082 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:46 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50091 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:47 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2yy.1.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50163 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:47 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50182 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:48 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50202 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:48 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50210 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:48 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50215 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:48 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50240 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:49 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2yy.1.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50260 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:49 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50282 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:49 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2yy.1.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50289 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:51 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50345 PROTO=UDP <1>SPT=67 DPT=68 LEN=308
Apr 2 12:49:51 kernel: ACCEPT <4>ACCEPT IN=eth0 OUT= MAC=ff:ff:ff:ff:ff:ff:00:19:2f:xx:xx:xx:xx:00 <1>SRC=10.2xx.0.1 DST=255.255.255.255 <1>LEN=328 TOS=0x00 PREC=0x00 TTL=255 ID=50356 PROTO=UDP <1>SPT=67 DPT=68 LEN=308Not an expert on this. But I am guessing this indicates some type of broadcast packets, about 3 per second, from/through my Cabel Modem against my WAN port on RT-AC66U. Looks to match the 3KB/s traffic indicated.
Soo, does this look logical ? Anybody more experienced that could clue me inn to what kind of situation/traffic I am looking at ?

