SystemF
Regular Contributor
Hello guys! I have home pc connected to rt-ac88u (stock latest firmware) with lan subnet 192.168.199.0/24,
Set up an openvpn server in the router with subnet 10.222.33.0/24. When connect the client to rt-ac88u 172.16.100.112/24 with subnet 172.16.100.0/24 to i want to be able to reach the client from server side (home pc). I have tried numrios of things nothing seem to work. Read few topics here, in openvpn forum, i see its posibble wit Merlink Firmware, but with Asus stock?
Posting screenshots
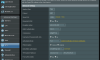
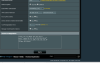
p.s. Also tried with clien-client option no luck either.
Update: I’m able to access the server’s LAN from a client but not vice versa.
Set up an openvpn server in the router with subnet 10.222.33.0/24. When connect the client to rt-ac88u 172.16.100.112/24 with subnet 172.16.100.0/24 to i want to be able to reach the client from server side (home pc). I have tried numrios of things nothing seem to work. Read few topics here, in openvpn forum, i see its posibble wit Merlink Firmware, but with Asus stock?
Posting screenshots


p.s. Also tried with clien-client option no luck either.
Update: I’m able to access the server’s LAN from a client but not vice versa.
Last edited:

