Hi,
I thought I would document my experience setting Guest Network Pro up, so other folks at my (basic) level of technical expertise can see what it looks like and the various gotchas. I'm happy for feedback on what I should have done or changes (but please say why and what it is for)…
I was essentially trying to make an IoT Network for my Home Assistant (HA) setup and after reading (a LOT) whether to put the HA Server on the same LAN or not, I eventually did so, due to (inter-alia) 'Matter' and simply ease of device management. It's probably not as secure as it could be but for me this is less about security (not that it isn't important!) and more about being able to manage the growing system. So:
Part I: Guest Network Pro
Network
Part 2: LAN, VLAN Tab
I thought I would document my experience setting Guest Network Pro up, so other folks at my (basic) level of technical expertise can see what it looks like and the various gotchas. I'm happy for feedback on what I should have done or changes (but please say why and what it is for)…
I was essentially trying to make an IoT Network for my Home Assistant (HA) setup and after reading (a LOT) whether to put the HA Server on the same LAN or not, I eventually did so, due to (inter-alia) 'Matter' and simply ease of device management. It's probably not as secure as it could be but for me this is less about security (not that it isn't important!) and more about being able to manage the growing system. So:
Part I: Guest Network Pro
Network
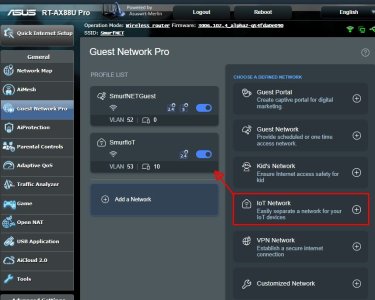
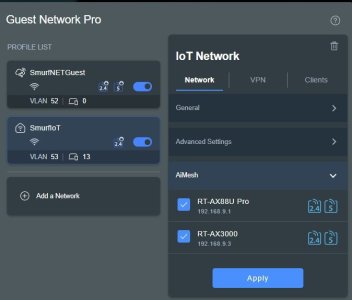
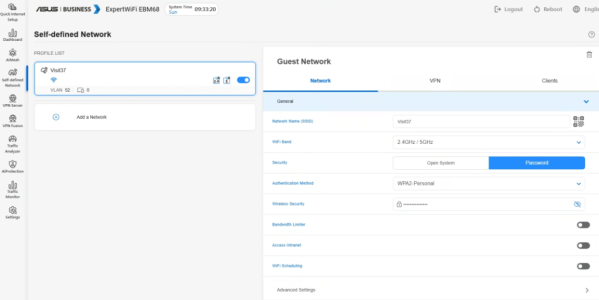
- I added an IoT network from the list of options under the Guest Network Pro Tab, because well, that what's most of the devices are; and HA runs it.
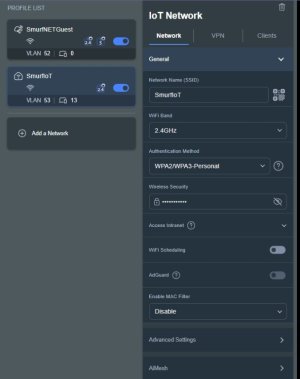
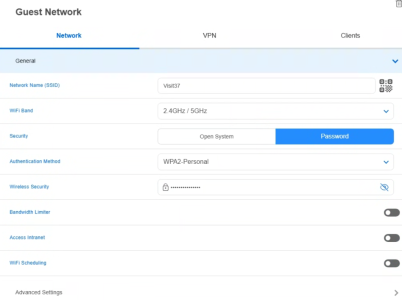
- The SSID, Band, Authentication are all self-explanatory.
- I selected the 2.4GHz band 'only' because 99% of IoT devices use that band; PLUS if (like me) you have a 3004-based AIMesh node (RT-AX3000) to a 3006 Primary Router, then ASUS have deemed to 'allow' you one Wi-Fi Interface per band (on top of the Primary network). I documented this elsewhere so I will not expand on it here, but by only using 2.4GHz on that I freed up the 5GHz for my Guest Wi-Fi, on that AIMesh Node.
- I selected 'WPA2/WPA3 Personal' but have read of a few folks with issues with that setting, that have dropped to just WPA2. YMMV.
- I left Access Intranet on MAIN only (the default) for IoT Networks.
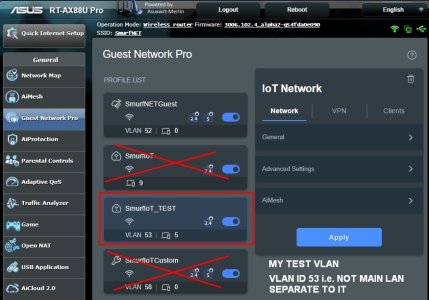
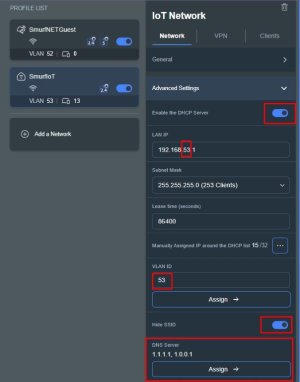
- In advanced settings I left the subnet at what GNP selected automatically (53, the first one selected after Guest took 52). You can change it to what you like later.
- I changed the DNS Server to Cloudflare (put in the DNS manually). Apparently Default does not (currently) work (I cannot find the post(s) on this sorry).
- I selected the AIMesh Node (as well as Main).
- I went into "Manually Assigned" and assigned all my IoT Device IPs and Names, including Ethernet Devices.
- When you add manual profiles, you can drop down from a list of names, but you need to add the IP address manually (use the VLAN subnet) and the Name. I did not fill in any DNS Server. Do not forget to click OK, then APPLY (or you will be putting them ALL in again...).
- One observation, a quirk of ASUS, is that after it was all set up, the ASUS Client List showed an IoT device (update, now a few devices) with the correctly assigned IP address, but it turned up in the table in the Primary Router SSID Section; very odd. A point to note these were all IoT devices connected to the AIMesh Node, not the main network, the latter which all displayed correctly. Odder still.
- My IoT Network does not need one.
- Only for viewing after it is working.
Part 2: LAN, VLAN Tab
- This section is for Ethernet-attached devices only, associated with your VLAN, no Wifi component here (that is in the Part I above).
- Note that when you create your VLAN in Part I, it automatically populates this Tab.
- In here I selected the Ethernet Port which goes to an 8 Port Unmanaged Switch in a Cabinet downstairs.
- It is a TP-Link (TL-SG1008P) 8 Port (4 PoE) UN-managed switch. @visortgw kindly gave us many, many, many, many pointers that you can use such an ainmal (from TP-link but not some others) that work as passthrough and I found evidence of that in various websites, for this model. See attachments in imgur.
- The Router (LAN Port 2) connects to the switch and the in turn feeds the HA Server (an RPi4), two Xiaomi Gateway Hubs and the TV.
- So, in LAN/VLAN I chose "Access" as I only have one VLAN (and read that was appropriate for that reason).
- The first time, I selected my newly-created IoT Network (SmurfIoT), clicked apply and ... nothing ... no Wired devices joined the IoT Network (wireless was fine).
- Well I tried All (Default) (NG), I tried Trunk (NG), I looked at the Profile Tab (don't need to and will not touch it), I pulled cables in and out of all the Ports thinking maybe the PoE ones were being nasty, but nothing.
- Eventually I simply powered off the switch and then back on again after a minute or so and lo and behold, success! So I strongly suggest this last step...

Attachments
Last edited: