Sebastienbo
Occasional Visitor
http://www.smallnetbuilder.com/lanw...ll-lan-using-tagged-vlans-part-2?limitstart=0
Concerning the article above I have question.
I've been buying the same switches as above but my config has become a complete mess, I don't understand what I'm doing wroing and I have tried so many combinations (tag/untagged/etc..) but I'm not able to achieve a trunk :-(
Therefore I've descided to swallow my pride and ask for help on this forum
The prupose of my setup is as follow:
I have a wall with just one cable from my living room (where the provider modem is + some internal network devices) to my office room (where I have the firewall/router/wlanap + Internal devices such as pc's/nas/etc..)
Both sides have the article described device : ZyXEL GS1900-8HP with the latest firmware 2.0
What I want to achieve:
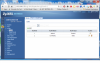
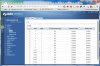
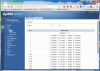
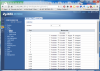
My modem (in the living room should connect to port 2 so I set PVID to vlan 2 and vlan 2 is part of port 1 and 2 untagged), so port 2 becomes my DMZ or external network (whatever you wanna call it)
Remaining Ports 1,3,5,6,7,8 are vlan 1 (internal lan for pc's)
Port 1 should handle traffic from vlan 1 and vlan 2 and sent it over that one cable over to the office, so I configurred port 1 as a trunk on both switches accepting tagged and untagged traffic.
So how should my traffic flow?
1) I have my provider modem sending data to port 2
2) port 2 should tag it and send it to it's other member ports (port 1)
3) Port 1 sends it over to the other switch port 1 where it should be detected as beeing part of vlan 2 ) therfore sent it to port 2
4) Port 2 sends that traffic to my WAN side of my router
5) The lan side of my router sends that traffic to port 3 of the switch, which is vlan 1
6) And if something happens in the office on vlan 1, it should be sent over that one cable again to the other 7) vlan 1 members in the living room (my tv,home enterainment,etc..)
Important: At no point the traffic of my provider and my internal traffic may see each other: It must go through the router first
As you see, this should not be a complicated confifuration at all...I feel so stupid not beeing able to solve it myself :-(
Can someone help me understand what I'm doing wrong?
Concerning the article above I have question.
I've been buying the same switches as above but my config has become a complete mess, I don't understand what I'm doing wroing and I have tried so many combinations (tag/untagged/etc..) but I'm not able to achieve a trunk :-(
Therefore I've descided to swallow my pride and ask for help on this forum
The prupose of my setup is as follow:
I have a wall with just one cable from my living room (where the provider modem is + some internal network devices) to my office room (where I have the firewall/router/wlanap + Internal devices such as pc's/nas/etc..)
Both sides have the article described device : ZyXEL GS1900-8HP with the latest firmware 2.0
What I want to achieve:
My modem (in the living room should connect to port 2 so I set PVID to vlan 2 and vlan 2 is part of port 1 and 2 untagged), so port 2 becomes my DMZ or external network (whatever you wanna call it)
Remaining Ports 1,3,5,6,7,8 are vlan 1 (internal lan for pc's)
Port 1 should handle traffic from vlan 1 and vlan 2 and sent it over that one cable over to the office, so I configurred port 1 as a trunk on both switches accepting tagged and untagged traffic.
So how should my traffic flow?
1) I have my provider modem sending data to port 2
2) port 2 should tag it and send it to it's other member ports (port 1)
3) Port 1 sends it over to the other switch port 1 where it should be detected as beeing part of vlan 2 ) therfore sent it to port 2
4) Port 2 sends that traffic to my WAN side of my router
5) The lan side of my router sends that traffic to port 3 of the switch, which is vlan 1
6) And if something happens in the office on vlan 1, it should be sent over that one cable again to the other 7) vlan 1 members in the living room (my tv,home enterainment,etc..)
Important: At no point the traffic of my provider and my internal traffic may see each other: It must go through the router first
As you see, this should not be a complicated confifuration at all...I feel so stupid not beeing able to solve it myself :-(
Can someone help me understand what I'm doing wrong?