misses esterhouse
Occasional Visitor
I've read quite a few threads on running the OpenVPN server and client in parallel and understand that if I wish to do so and still be able to access my OpenVPN server from the WAN (away from home), I will need to setup policy based routing (aka split tunneling). That's fine with me however, I am having a little trouble wrapping my head around how to implement this ideally given my use case scenario. I have a moderate sized home network of 43 devices. Some of which I want to be able to access from the WAN went not at home using the OpenVPN server and my android device. I see that when enabling policy based routing within the OpenVPN client a box pops open allowing me to fill all the info in for setting the routing table for this. What I would like to know is, if setting the "Source IP" to my devices I want access to from my OpenVPN server, one by one for each and then setting the "Destination IP" to the OpenVPN servers IP pool in CIDR notation and their interfaces to "WAN", will this work as long as I set all other "Source IPs" in my network to interface any "Destination IP" to "VPN"?
Also, if this would work, will the policy based devices interfacing the WAN still be firewall protected from the internet?
I would rather just have everything in my private network accessible through my openVPN server as it was before I decided to run the OpenVPN client.
OpenVPN Server:
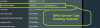
OpenVPN Client:
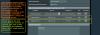
Also, if this would work, will the policy based devices interfacing the WAN still be firewall protected from the internet?
I would rather just have everything in my private network accessible through my openVPN server as it was before I decided to run the OpenVPN client.
OpenVPN Server:
OpenVPN Client:
Last edited:

