#Update2
Problem:
Outside and inside I can connect to the clients on the OpenVPN server running on the Asus router. But I can't get a usable internet connection.
This will only change if I deactivate the internal firewall of the Asus router. Now the internet works on all devices without problems. But I would still like to have the firewall enabled and a usable OpenVPN server.
A short description: Depending on the routing, the LAN devices are either pushed onto the wall or the VPN client (north VPN). From outside you should be able to log in to the VPN server and surf. I think it should be possible.
What I have already done, unfortunately only moderate success:
- Router reset and tried again.
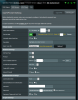
- WAN - Port Trigger "Activated": Trigger Port 1194 UDP, Incomming 1194 UDP
- WAN - Virtual Server / Port Forwarding "Enabled": 192.168.168.33 UDP on port 1194#
Important! Only when I configured these two options I could see the connected devices with IP under VPN Status. So I already blocked something here
- Various other port forwaring rules added
- VPN Client (North VPN) deleted and tried again. Force Internet traffic through "Policy Rules/ or Strict"
- With and without DNS settings
- Pixel server deactivated
- Adding IPtables Rules to /jffs/sripts/firewall-start
iptables -I INPUT -p udp --dport 1149 -j ACCEPT
iptables -I OUTPUT -p udp --dport 1149 -j ACCEPT
Short setting up:
RT-AC86U:
- Operating Mode:Wireless Router Firmware Version:384.17
- Internet > (ISP) Fritzbox > LAN cable to the WAN port of the Asus router > Asus Router integrated OpenVPN server and configured OpenVpn Cliebt (North VPN).
Fritzbox:
- IP address: 77.182.38.14 (Changes daily)
- Gateway 62.52.201.195
- DNS servers 37,235,1,174; 37,235,1,177
- DynDNS activated, axxxxx7.ddnss.de
- Port release for 192.167.178.33 Port 1194
- IPv4 routing table: Network Subnet Mask Gateway 10.8.0.0; 255.255.0.0; 192.168.178.33
- Asus router always assigned to the same IP.
Asus router:
- Wireless router mode / AiMesh Router mode (default)
- WAN IP: 192.168.178.33
- subnet mask 255.255.255.0
- Lan IP: 192.168.1.1
- IP pool start address : 192.168.1.3
- Pixel server : 192.168.1.2
- IP pool end address : 192.168.1.254
- VPN Subnet / Netmask 10.8.0.0 255.255.255.0
- DNS server: 37.235.1.174 and 37.235.1.177
- LAN - DHCP Server "On". Manual Assignment "On"
- LAN Static routes "Disabled"
- Default gateway "None"
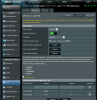
- VPN Client (NordVPN) active; 10.8.3.8 Here certain clients are assigned to the VPN via rules.
Problem:
Outside and inside I can connect to the clients on the OpenVPN server running on the Asus router. But I can't get a usable internet connection.
This will only change if I deactivate the internal firewall of the Asus router. Now the internet works on all devices without problems. But I would still like to have the firewall enabled and a usable OpenVPN server.
A short description: Depending on the routing, the LAN devices are either pushed onto the wall or the VPN client (north VPN). From outside you should be able to log in to the VPN server and surf. I think it should be possible.
What I have already done, unfortunately only moderate success:
- Router reset and tried again.
- WAN - Port Trigger "Activated": Trigger Port 1194 UDP, Incomming 1194 UDP
- WAN - Virtual Server / Port Forwarding "Enabled": 192.168.168.33 UDP on port 1194#
Important! Only when I configured these two options I could see the connected devices with IP under VPN Status. So I already blocked something here
- Various other port forwaring rules added
- VPN Client (North VPN) deleted and tried again. Force Internet traffic through "Policy Rules/ or Strict"
- With and without DNS settings
- Pixel server deactivated
- Adding IPtables Rules to /jffs/sripts/firewall-start
iptables -I INPUT -p udp --dport 1149 -j ACCEPT
iptables -I OUTPUT -p udp --dport 1149 -j ACCEPT
Short setting up:
RT-AC86U:
- Operating Mode:Wireless Router Firmware Version:384.17
- Internet > (ISP) Fritzbox > LAN cable to the WAN port of the Asus router > Asus Router integrated OpenVPN server and configured OpenVpn Cliebt (North VPN).
Fritzbox:
- IP address: 77.182.38.14 (Changes daily)
- Gateway 62.52.201.195
- DNS servers 37,235,1,174; 37,235,1,177
- DynDNS activated, axxxxx7.ddnss.de
- Port release for 192.167.178.33 Port 1194
- IPv4 routing table: Network Subnet Mask Gateway 10.8.0.0; 255.255.0.0; 192.168.178.33
- Asus router always assigned to the same IP.
Asus router:
- Wireless router mode / AiMesh Router mode (default)
- WAN IP: 192.168.178.33
- subnet mask 255.255.255.0
- Lan IP: 192.168.1.1
- IP pool start address : 192.168.1.3
- Pixel server : 192.168.1.2
- IP pool end address : 192.168.1.254
- VPN Subnet / Netmask 10.8.0.0 255.255.255.0
- DNS server: 37.235.1.174 and 37.235.1.177
- LAN - DHCP Server "On". Manual Assignment "On"
- LAN Static routes "Disabled"
- Default gateway "None"
- VPN Client (NordVPN) active; 10.8.3.8 Here certain clients are assigned to the VPN via rules.
Attachments
Last edited: