Hi, new user here. I wanted to ask if anyone can give me some guidance on a problem:
I set up an ASUS AC-68U with Merlin software for full-time VPN connection, using NordVPN. It basically works, but the problem is an intermittent loss of connectivity, always coincident with one of the cipher renegotiations that occurs every 60 minutes. It happens maybe once every day or two.
Log file below. At 09:45 I lose connection. I was streaming TV and noted loss of connection at that time. At 09:55 the inactivity timeout kicks in and restores the connection. I'll also attach screen shots of my OVPN client config. Appreciate any tips. Thanks!
also attaching images of the client config
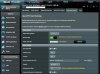
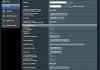
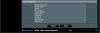
I set up an ASUS AC-68U with Merlin software for full-time VPN connection, using NordVPN. It basically works, but the problem is an intermittent loss of connectivity, always coincident with one of the cipher renegotiations that occurs every 60 minutes. It happens maybe once every day or two.
Log file below. At 09:45 I lose connection. I was streaming TV and noted loss of connection at that time. At 09:55 the inactivity timeout kicks in and restores the connection. I'll also attach screen shots of my OVPN client config. Appreciate any tips. Thanks!
HTML:
Jul 10 09:45:25 openvpn[14026]: VERIFY OK: depth=1, C=PA, ST=PA, L=Panama, O=NordVPN, OU=NordVPN, CN=us415.nordvpn.com, name=NordVPN, emailAddress=cert@nordvpn.com
Jul 10 09:45:25 openvpn[14026]: VERIFY KU OK
Jul 10 09:45:25 openvpn[14026]: Validating certificate extended key usage
Jul 10 09:45:25 openvpn[14026]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Jul 10 09:45:25 openvpn[14026]: VERIFY EKU OK
Jul 10 09:45:25 openvpn[14026]: VERIFY OK: depth=0, C=PA, ST=PA, L=Panama, O=NordVPN, OU=NordVPN, CN=us415.nordvpn.com, name=NordVPN, emailAddress=cert@nordvpn.com
Jul 10 09:45:28 openvpn[14026]: Data Channel Encrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
Jul 10 09:45:28 openvpn[14026]: Data Channel Decrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
Jul 10 09:45:28 openvpn[14026]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Jul 10 09:55:18 openvpn[14026]: [us415.nordvpn.com] Inactivity timeout (--ping-restart), restarting
Jul 10 09:55:18 openvpn[14026]: SIGUSR1[soft,ping-restart] received, process restarting
Jul 10 09:55:18 openvpn[14026]: Restart pause, 5 second(s)
Jul 10 09:55:23 openvpn[14026]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jul 10 09:55:23 openvpn[14026]: TCP/UDP: Preserving recently used remote address: [AF_INET]23.108.32.9:1194
Jul 10 09:55:23 openvpn[14026]: Socket Buffers: R=[122880->245760] S=[122880->245760]
Jul 10 09:55:23 openvpn[14026]: UDP link local: (not bound)
Jul 10 09:55:23 openvpn[14026]: UDP link remote: [AF_INET]23.108.32.9:1194
Jul 10 09:55:24 openvpn[14026]: TLS: Initial packet from [AF_INET]23.108.32.9:1194, sid=42a75906 c7db0840
Jul 10 09:55:24 openvpn[14026]: VERIFY OK: depth=1, C=PA, ST=PA, L=Panama, O=NordVPN, OU=NordVPN, CN=us415.nordvpn.com, name=NordVPN, emailAddress=cert@nordvpn.com
Jul 10 09:55:24 openvpn[14026]: VERIFY KU OK
Jul 10 09:55:24 openvpn[14026]: Validating certificate extended key usage
Jul 10 09:55:24 openvpn[14026]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Jul 10 09:55:24 openvpn[14026]: VERIFY EKU OK
Jul 10 09:55:24 openvpn[14026]: VERIFY OK: depth=0, C=PA, ST=PA, L=Panama, O=NordVPN, OU=NordVPN, CN=us415.nordvpn.com, name=NordVPN, emailAddress=cert@nordvpn.com
Jul 10 09:55:25 openvpn[14026]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Jul 10 09:55:25 openvpn[14026]: [us415.nordvpn.com] Peer Connection Initiated with [AF_INET]23.108.32.9:1194
Jul 10 09:55:26 openvpn[14026]: SENT CONTROL [us415.nordvpn.com]: 'PUSH_REQUEST' (status=1)
Jul 10 09:55:26 openvpn[14026]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,sndbuf 524288,rcvbuf 524288,dhcp-option DNS 78.46.223.24,dhcp-option DNS 162.242.211.137,route-gateway 10.8.8.1,topology subnet,ping 60,ping-restart 180,ifconfig 10.8.8.11 255.255.255.0,peer-id 3,cipher AES-256-GCM'
Jul 10 09:55:26 openvpn[14026]: OPTIONS IMPORT: timers and/or timeouts modified
Jul 10 09:55:26 openvpn[14026]: OPTIONS IMPORT: --sndbuf/--rcvbuf options modified
Jul 10 09:55:26 openvpn[14026]: Socket Buffers: R=[245760->245760] S=[245760->245760]
Jul 10 09:55:26 openvpn[14026]: OPTIONS IMPORT: --ifconfig/up options modified
Jul 10 09:55:26 openvpn[14026]: OPTIONS IMPORT: route options modified
Jul 10 09:55:26 openvpn[14026]: OPTIONS IMPORT: route-related options modified
Jul 10 09:55:26 openvpn[14026]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Jul 10 09:55:26 openvpn[14026]: OPTIONS IMPORT: peer-id set
Jul 10 09:55:26 openvpn[14026]: OPTIONS IMPORT: adjusting link_mtu to 1657
Jul 10 09:55:26 openvpn[14026]: OPTIONS IMPORT: data channel crypto options modified
Jul 10 09:55:26 openvpn[14026]: Data Channel Encrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
Jul 10 09:55:26 openvpn[14026]: Data Channel Decrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
Jul 10 09:55:26 openvpn[14026]: Preserving previous TUN/TAP instance: tun15
Jul 10 09:55:26 openvpn[14026]: Initialization Sequence Completedalso attaching images of the client config


Last edited:

