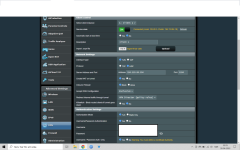
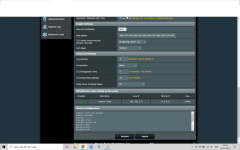
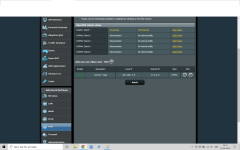
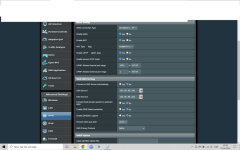
According to technical guys from NordVPN you should put 'cipher AES-256-CBC' in the custom field when using Merlin. If they give wrong info please tell them.
Out of the box by default, mine seems to settle on AES-256-GCM... Based on what I'm reading below, it's better to use GCM than CBC.
Code:
Jan 6 15:52:37 ovpn-client5[7114]: VERIFY OK: depth=0, CN=us2951.nordvpn.com
Jan 6 15:52:37 ovpn-client5[7114]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Jan 6 15:52:37 ovpn-client5[7114]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Jan 6 15:52:37 ovpn-client5[7114]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 4096 bit RSA, signature: RSA-SHA512
AES-CBC vs AES-GCM
Until fairly recently, AES was usually used in cipher block chaining (CBC) mode, where each block of plaintext is XORed with the previous ciphertext block before being encrypted. When used in CBC mode, a
HMAC hashing algorithm such as HMAC-SHA256 is required to verify the data.
It is increasingly common, however, to see AES used in Galois/counter (GCM) mode, which uses the
counter mode of encryption. The main advantage of this is that it uses the
Galois field to verify data without the need for an outside algorithm. It is therefore more efficient than using a separate authentication algorithm that can have a high computational overhead.
Although AES-CBC with HMAC authentication is generally considered secure, CBC is potentially vulnerable to
padding attacks, such as
POODLE. GCM is not. Proton VPN uses AES-GCM in our OpenVPN encryption suite.
Even NordVPN Support recommends AES-256-GCM:
1. OpenVPN
OpenVPN is a mature and robust piece of open-source software that enables us to provide a reliable and secure VPN service. It is a versatile VPN protocol that can be used on both TCP and UDP ports. OpenVPN supports a great number of strong encryption algorithms and ciphers:
to ensure the protection of your data, we use AES-256-GCM with a 4096-bit DH key. If you are conscious about your security and are wondering what the most stable NordVPN protocol is, we recommend OpenVPN.
NordVPN supports a number of security encryption protocols to provide a VPN service. The security levels and purposes of these VPN protocols are different, but so are our customers’ needs. We encou...

support.nordvpn.com