Hi
Anyone else having issues with the Route setting in the latest fw?
I run OpenVPN on my NAS and after upgrading the Merlin fw I can´t access the other PC:s on the LAN anymore (when connecting via VPN).
I can reach the NAS but that's it.
It all worked before and the only thing that changed is that I've upgraded the routers fw.
Sadly I don´t remember which version I had before.
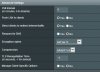
Route is like this (.126 is the ip of my NAS):
10.8.0.0 255.255.255.0 192.168.1.126 LAN
Anyone got any suggestions what the problem might be?
Thanks
EDIT: The router is a RT-N66U
Anyone else having issues with the Route setting in the latest fw?
I run OpenVPN on my NAS and after upgrading the Merlin fw I can´t access the other PC:s on the LAN anymore (when connecting via VPN).
I can reach the NAS but that's it.
It all worked before and the only thing that changed is that I've upgraded the routers fw.
Sadly I don´t remember which version I had before.
Route is like this (.126 is the ip of my NAS):
10.8.0.0 255.255.255.0 192.168.1.126 LAN
Anyone got any suggestions what the problem might be?
Thanks
EDIT: The router is a RT-N66U
Last edited: