Hi,
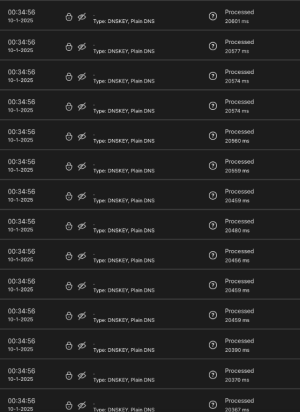
Sometimes, out of nowhere as I really cannot put a clock or any preceding event to it, the router suddenly starts sending out thousands of queries for "." (without quotes, so literally just a dot).
The type is "DNSKEY, plain DNS" and, probably due to the sheer volume of them (we're talking tens of thousands of requests suddenly), they take about 20 seconds to complete - each! The CPU load on the router skyrockets and DNS resolution comes to a halt (as well as services ceasing to respond).
... But why is it doing that? Digging deeeeep in my memory, I believe the . DNSKEY is to find root servers. But why on earth does it send tens of thousands of requests for it and all at once? It supposed to request it and then cache it for a while. Not try to resolve it thousands and thousands of time. To be clear: the requests come from the router itself, not from a client on the network.
Anyone got any idea? Google is not being overly helpful.
Google is not being overly helpful.
I'm running Merlin on an AX3000-V2 with AdGuard Home running as the DNS service. Attached some screenshots.
Thanks!
Sometimes, out of nowhere as I really cannot put a clock or any preceding event to it, the router suddenly starts sending out thousands of queries for "." (without quotes, so literally just a dot).
The type is "DNSKEY, plain DNS" and, probably due to the sheer volume of them (we're talking tens of thousands of requests suddenly), they take about 20 seconds to complete - each! The CPU load on the router skyrockets and DNS resolution comes to a halt (as well as services ceasing to respond).
... But why is it doing that? Digging deeeeep in my memory, I believe the . DNSKEY is to find root servers. But why on earth does it send tens of thousands of requests for it and all at once? It supposed to request it and then cache it for a while. Not try to resolve it thousands and thousands of time. To be clear: the requests come from the router itself, not from a client on the network.
Anyone got any idea?
I'm running Merlin on an AX3000-V2 with AdGuard Home running as the DNS service. Attached some screenshots.
Thanks!