Andorul
Occasional Visitor
I bought a brand new RT-AX88U to be connected to a ISP ONT+Modem/Router to be VPN router thus serving a TV.
Problem: RT-AX88U gets a diferent IP from ISP router and with VPN Client activated and TV conected to Asus get the ISP Public IP
I have a ISP FiberGATEWAY
Bridge Mode ON,
DHCP ON,
Local IP 192.168.1.254,
Sub-Net 192.168.1.2 to 254
Firewall ON
IPv6 ON
RT-AX88U ethernet cable from WLAN to LAN4 in ISP FiberGateway
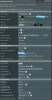
Operation Mode:Wireless router Firmware Version:3.0.0.4.384_7968
DHCP On
Local IP: 192.168.50.1
Sub-net 192.168.2 2 to 254
WAN Connection Type
Enable WAN Yes
Enable NAT Yes
NordVPN profile added and connected
Router 1 have a diferent Public IP from Router 2 (rt-ax88u)
LOG After VPN Client Connection
Both router ISP andAsus have diferent public ip
Jan 13 10:43:00 rc_service: httpd 6026:notify_rc restart_vpncall
Jan 13 10:43:00 vpnclient5[20657]: OpenVPN 2.4.7 arm-buildroot-linux-gnueabi [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Dec 17 2019
Jan 13 10:43:00 vpnclient5[20657]: library versions: OpenSSL 1.0.2t 10 Sep 2019, LZO 2.03
Jan 13 10:43:00 vpnclient5[20658]: WARNING: --ping should normally be used with --ping-restart or --ping-exit
Jan 13 10:43:00 vpnclient5[20658]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jan 13 10:43:00 vpnclient5[20658]: NOTE: --fast-io is disabled since we are not using UDP
Jan 13 10:43:00 vpnclient5[20658]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Jan 13 10:43:00 vpnclient5[20658]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Jan 13 10:43:00 vpnclient5[20658]: TCP/UDP: Preserving recently used remote address: [AF_INET]45.152.180.11:443
Jan 13 10:43:00 vpnclient5[20658]: Socket Buffers: R=[87380->87380] S=[16384->16384]
Jan 13 10:43:00 vpnclient5[20658]: Attempting to establish TCP connection with [AF_INET]45.152.180.11:443 [nonblock]
Jan 13 10:43:01 vpnclient5[20658]: TCP connection established with [AF_INET]45.152.180.11:443
Jan 13 10:43:01 vpnclient5[20658]: TCP_CLIENT link local: (not bound)
Jan 13 10:43:01 vpnclient5[20658]: TCP_CLIENT link remote: [AF_INET]45.152.180.11:443
Jan 13 10:43:01 vpnclient5[20658]: TLS: Initial packet from [AF_INET]45.152.180.11:443, sid=bf52862e 4b4aecf4
Jan 13 10:43:01 vpnclient5[20658]: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Jan 13 10:43:02 vpnclient5[20658]: VERIFY OK: depth=2, C=PA, O=NordVPN, CN=NordVPN Root CA
Jan 13 10:43:02 vpnclient5[20658]: VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA4
Jan 13 10:43:02 vpnclient5[20658]: VERIFY KU OK
Jan 13 10:43:02 vpnclient5[20658]: Validating certificate extended key usage
Jan 13 10:43:02 vpnclient5[20658]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Jan 13 10:43:02 vpnclient5[20658]: VERIFY EKU OK
Jan 13 10:43:02 vpnclient5[20658]: VERIFY OK: depth=0, CN=us4549.nordvpn.com
Jan 13 10:43:02 vpnclient5[20658]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
Jan 13 10:43:02 vpnclient5[20658]: [us4549.nordvpn.com] Peer Connection Initiated with [AF_INET]45.152.180.11:443
Jan 13 10:43:03 vpnclient5[20658]: SENT CONTROL [us4549.nordvpn.com]: 'PUSH_REQUEST' (status=1)
Jan 13 10:43:04 vpnclient5[20658]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 103.86.96.100,dhcp-option DNS 103.86.99.100,sndbuf 524288,rcvbuf 524288,explicit-exit-notify,comp-lzo no,route-gateway 10.7.1.1,topology subnet,ping 60,ping-restart 180,ifconfig 10.7.1.3 255.255.255.0,peer-id 0,cipher AES-256-GCM'
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: timers and/or timeouts modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: --explicit-exit-notify can only be used with --proto udp
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: compression parms modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: --sndbuf/--rcvbuf options modified
Jan 13 10:43:04 vpnclient5[20658]: Socket Buffers: R=[408320->1048576] S=[92160->1048576]
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: --ifconfig/up options modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: route options modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: route-related options modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: peer-id set
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: adjusting link_mtu to 1659
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: data channel crypto options modified
Jan 13 10:43:04 vpnclient5[20658]: Data Channel: using negotiated cipher 'AES-256-GCM'
Jan 13 10:43:04 vpnclient5[20658]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Jan 13 10:43:04 vpnclient5[20658]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Jan 13 10:43:04 vpnclient5[20658]: TUN/TAP device tun15 opened
Jan 13 10:43:04 vpnclient5[20658]: TUN/TAP TX queue length set to 100
Jan 13 10:43:04 vpnclient5[20658]: /sbin/ifconfig tun15 10.7.1.3 netmask 255.255.255.0 mtu 1500 broadcast 10.7.1.255
Jan 13 10:43:04 vpnclient5[20658]: /etc/openvpn/ovpn-up tun15 1500 1587 10.7.1.3 255.255.255.0 init
Jan 13 10:43:04 vpnclient5[20658]: Initialization Sequence Completed
Problem: RT-AX88U gets a diferent IP from ISP router and with VPN Client activated and TV conected to Asus get the ISP Public IP
I have a ISP FiberGATEWAY
Bridge Mode ON,
DHCP ON,
Local IP 192.168.1.254,
Sub-Net 192.168.1.2 to 254
Firewall ON
IPv6 ON
RT-AX88U ethernet cable from WLAN to LAN4 in ISP FiberGateway
Operation Mode:Wireless router Firmware Version:3.0.0.4.384_7968
DHCP On
Local IP: 192.168.50.1
Sub-net 192.168.2 2 to 254
WAN Connection Type
Enable WAN Yes
Enable NAT Yes
NordVPN profile added and connected
Router 1 have a diferent Public IP from Router 2 (rt-ax88u)
LOG After VPN Client Connection
Both router ISP andAsus have diferent public ip
Jan 13 10:43:00 rc_service: httpd 6026:notify_rc restart_vpncall
Jan 13 10:43:00 vpnclient5[20657]: OpenVPN 2.4.7 arm-buildroot-linux-gnueabi [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Dec 17 2019
Jan 13 10:43:00 vpnclient5[20657]: library versions: OpenSSL 1.0.2t 10 Sep 2019, LZO 2.03
Jan 13 10:43:00 vpnclient5[20658]: WARNING: --ping should normally be used with --ping-restart or --ping-exit
Jan 13 10:43:00 vpnclient5[20658]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jan 13 10:43:00 vpnclient5[20658]: NOTE: --fast-io is disabled since we are not using UDP
Jan 13 10:43:00 vpnclient5[20658]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Jan 13 10:43:00 vpnclient5[20658]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Jan 13 10:43:00 vpnclient5[20658]: TCP/UDP: Preserving recently used remote address: [AF_INET]45.152.180.11:443
Jan 13 10:43:00 vpnclient5[20658]: Socket Buffers: R=[87380->87380] S=[16384->16384]
Jan 13 10:43:00 vpnclient5[20658]: Attempting to establish TCP connection with [AF_INET]45.152.180.11:443 [nonblock]
Jan 13 10:43:01 vpnclient5[20658]: TCP connection established with [AF_INET]45.152.180.11:443
Jan 13 10:43:01 vpnclient5[20658]: TCP_CLIENT link local: (not bound)
Jan 13 10:43:01 vpnclient5[20658]: TCP_CLIENT link remote: [AF_INET]45.152.180.11:443
Jan 13 10:43:01 vpnclient5[20658]: TLS: Initial packet from [AF_INET]45.152.180.11:443, sid=bf52862e 4b4aecf4
Jan 13 10:43:01 vpnclient5[20658]: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Jan 13 10:43:02 vpnclient5[20658]: VERIFY OK: depth=2, C=PA, O=NordVPN, CN=NordVPN Root CA
Jan 13 10:43:02 vpnclient5[20658]: VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA4
Jan 13 10:43:02 vpnclient5[20658]: VERIFY KU OK
Jan 13 10:43:02 vpnclient5[20658]: Validating certificate extended key usage
Jan 13 10:43:02 vpnclient5[20658]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Jan 13 10:43:02 vpnclient5[20658]: VERIFY EKU OK
Jan 13 10:43:02 vpnclient5[20658]: VERIFY OK: depth=0, CN=us4549.nordvpn.com
Jan 13 10:43:02 vpnclient5[20658]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
Jan 13 10:43:02 vpnclient5[20658]: [us4549.nordvpn.com] Peer Connection Initiated with [AF_INET]45.152.180.11:443
Jan 13 10:43:03 vpnclient5[20658]: SENT CONTROL [us4549.nordvpn.com]: 'PUSH_REQUEST' (status=1)
Jan 13 10:43:04 vpnclient5[20658]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 103.86.96.100,dhcp-option DNS 103.86.99.100,sndbuf 524288,rcvbuf 524288,explicit-exit-notify,comp-lzo no,route-gateway 10.7.1.1,topology subnet,ping 60,ping-restart 180,ifconfig 10.7.1.3 255.255.255.0,peer-id 0,cipher AES-256-GCM'
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: timers and/or timeouts modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: --explicit-exit-notify can only be used with --proto udp
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: compression parms modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: --sndbuf/--rcvbuf options modified
Jan 13 10:43:04 vpnclient5[20658]: Socket Buffers: R=[408320->1048576] S=[92160->1048576]
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: --ifconfig/up options modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: route options modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: route-related options modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: peer-id set
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: adjusting link_mtu to 1659
Jan 13 10:43:04 vpnclient5[20658]: OPTIONS IMPORT: data channel crypto options modified
Jan 13 10:43:04 vpnclient5[20658]: Data Channel: using negotiated cipher 'AES-256-GCM'
Jan 13 10:43:04 vpnclient5[20658]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Jan 13 10:43:04 vpnclient5[20658]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Jan 13 10:43:04 vpnclient5[20658]: TUN/TAP device tun15 opened
Jan 13 10:43:04 vpnclient5[20658]: TUN/TAP TX queue length set to 100
Jan 13 10:43:04 vpnclient5[20658]: /sbin/ifconfig tun15 10.7.1.3 netmask 255.255.255.0 mtu 1500 broadcast 10.7.1.255
Jan 13 10:43:04 vpnclient5[20658]: /etc/openvpn/ovpn-up tun15 1500 1587 10.7.1.3 255.255.255.0 init
Jan 13 10:43:04 vpnclient5[20658]: Initialization Sequence Completed