NightmareMan
New Around Here
Hi guys. I've read the manual https://github.com/RMerl/asuswrt-me...or-VPN-and-SSID-for-Regular-ISP-using-OpenVPN.
I did everything exactly like there was written. But still I get default IP (192.168.1.x) on wl1.1 interface and all traffic goes through my ISP, not through OpenVPN client I've set up. Maybe that manual is not actual already or maybe someone has an updated version?
My config:
And another thing: when I just try to execute the script manually I get this:
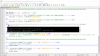
A screenshot from router to prove which interface I use:
 A screenshot from my phone:
A screenshot from my phone:
 It is clearly seen that the phone got default IP, not that which was in the IP range from the script.
It is clearly seen that the phone got default IP, not that which was in the IP range from the script.
I did everything exactly like there was written. But still I get default IP (192.168.1.x) on wl1.1 interface and all traffic goes through my ISP, not through OpenVPN client I've set up. Maybe that manual is not actual already or maybe someone has an updated version?
My config:
#!/bin/sh
####### Interface Specific Settings #######
WRLSS_IF=wl1.1 # Name of the wireless interface that will be used.
WRLSS_IF_NTWK_ADDR=192.168.2.0 # Network address that the wireless interface will be on.
WRLSS_IF_INET_ADDR=192.168.2.1 # IP address that will be assigned to the wireless interface.
WRLSS_IF_NETMASK=255.255.255.0 # Netmask of the wireless network to be added.
TUN_IF=tun11 # Name of tunnel interface.
########## DHCP Specific Settings ###########
DHCP_OPT1=3 # dnsmasq option to specify router.
LS_TIME=86400s # Duration of the dhcp leases.
LS_START=192.168.2.100 # Start address of leases. This needs to be within the same network as above.
LS_END=192.168.2.120 # End address of leases. This needs to be within the same network as above.
######## Hide SSID of Guest Network ########
HIDE_SSID=0 # This option is to hide the SSID of a guest network if a guest network is used. Input 1 to hide and 0 to make it visible.
############## Tunnel Module ##############
if [ `lsmod | grep -c tun` == 0 ]; then # This works with Openvpn using a tun interface.
insmod tun
sleep 1
fi
##########################################################################################################
##########################################################################################################
########################################## DHCP Server ###################################################
if [ `cat /etc/dnsmasq.conf | grep -c $WRLSS_IF` == 0 ]; then
killall dnsmasq
sleep 2
echo "interface=$WRLSS_IF" >> /etc/dnsmasq.conf
echo "dhcp-range=$WRLSS_IF,$LS_START,$LS_END,$WRLSS_IF_NETMASK,$LS_TIME" >> /etc/dnsmasq.conf
echo "dhcp-option=$WRLSS_IF,$DHCP_OPT1,$WRLSS_IF_INET_ADDR" >> /etc/dnsmasq.conf
dnsmasq --log-async
fi
sleep 2
### Check to see if tun interface is available ###
while [ ! -n "`ifconfig | grep $TUN_IF`" ]; do
sleep 1
done
############################################ IP ROUTING ##################################################
ifconfig $WRLSS_IF $WRLSS_IF_INET_ADDR netmask $WRLSS_IF_NETMASK
ip route show table main | grep -Ev ^default | while read ROUTE; do
ip route add table 10 $ROUTE;
done
ip route del 0.0.0.0/1 table main # Uncomment this line if you are not using the route-nopull option.
# Many VPN service providers push this route to redirect internet traffic over the tunnel.
ip route add default dev $TUN_IF table 10
ip rule add dev $WRLSS_IF table 10
ip route flush cache
####################################### ETHERNET BRIDGE TABLES RULES #####################################
EBT_BRULE1="-p ipv4 -i $WRLSS_IF -j DROP"
EBT_BRULE2="-p arp -i $WRLSS_IF -j DROP"
if [ -n "$EBT_BRULE1" ] && [ `ebtables -t broute -L | grep -ice "$EBT_BRULE1"` != 1 ]; then
ebtables -t broute -I BROUTING $EBT_BRULE1
fi
if [ -n "$EBT_BRULE2" ] && [ `ebtables -t broute -L | grep -ice "$EBT_BRULE2"` != 1 ]; then
ebtables -t broute -I BROUTING $EBT_BRULE2
fi
############################################ IP TABLES RULES #############################################
if [ `iptables -L -v | grep -c $WRLSS_IF` == 0 ]; then
iptables -I INPUT -i $WRLSS_IF -m state --state NEW -j ACCEPT
iptables -I FORWARD -i $WRLSS_IF -o $TUN_IF -j ACCEPT
fi
if [ `iptables -t nat -L -v | grep -c $TUN_IF` == 0 ]; then
iptables -t nat -I POSTROUTING -s $WRLSS_IF_NTWK_ADDR/24 -o $TUN_IF -j MASQUERADE # Change /24 to the subnet that you will be using.
fi
############################################### HIDE SSID ################################################
if [ `nvram get "$WRLSS_IF"_closed` != 1 ] && [ $HIDE_SSID == 1 ]; then
nvram set "$WRLSS_IF"_closed=1
nvram commit
fi
if [ `nvram get "$WRLSS_IF"_closed` != 0 ] && [ $HIDE_SSID == 0 ]; then
nvram set "$WRLSS_IF"_closed=0
nvram commit
fi
####### Interface Specific Settings #######
WRLSS_IF=wl1.1 # Name of the wireless interface that will be used.
WRLSS_IF_NTWK_ADDR=192.168.2.0 # Network address that the wireless interface will be on.
WRLSS_IF_INET_ADDR=192.168.2.1 # IP address that will be assigned to the wireless interface.
WRLSS_IF_NETMASK=255.255.255.0 # Netmask of the wireless network to be added.
TUN_IF=tun11 # Name of tunnel interface.
########## DHCP Specific Settings ###########
DHCP_OPT1=3 # dnsmasq option to specify router.
LS_TIME=86400s # Duration of the dhcp leases.
LS_START=192.168.2.100 # Start address of leases. This needs to be within the same network as above.
LS_END=192.168.2.120 # End address of leases. This needs to be within the same network as above.
######## Hide SSID of Guest Network ########
HIDE_SSID=0 # This option is to hide the SSID of a guest network if a guest network is used. Input 1 to hide and 0 to make it visible.
############## Tunnel Module ##############
if [ `lsmod | grep -c tun` == 0 ]; then # This works with Openvpn using a tun interface.
insmod tun
sleep 1
fi
##########################################################################################################
##########################################################################################################
########################################## DHCP Server ###################################################
if [ `cat /etc/dnsmasq.conf | grep -c $WRLSS_IF` == 0 ]; then
killall dnsmasq
sleep 2
echo "interface=$WRLSS_IF" >> /etc/dnsmasq.conf
echo "dhcp-range=$WRLSS_IF,$LS_START,$LS_END,$WRLSS_IF_NETMASK,$LS_TIME" >> /etc/dnsmasq.conf
echo "dhcp-option=$WRLSS_IF,$DHCP_OPT1,$WRLSS_IF_INET_ADDR" >> /etc/dnsmasq.conf
dnsmasq --log-async
fi
sleep 2
### Check to see if tun interface is available ###
while [ ! -n "`ifconfig | grep $TUN_IF`" ]; do
sleep 1
done
############################################ IP ROUTING ##################################################
ifconfig $WRLSS_IF $WRLSS_IF_INET_ADDR netmask $WRLSS_IF_NETMASK
ip route show table main | grep -Ev ^default | while read ROUTE; do
ip route add table 10 $ROUTE;
done
ip route del 0.0.0.0/1 table main # Uncomment this line if you are not using the route-nopull option.
# Many VPN service providers push this route to redirect internet traffic over the tunnel.
ip route add default dev $TUN_IF table 10
ip rule add dev $WRLSS_IF table 10
ip route flush cache
####################################### ETHERNET BRIDGE TABLES RULES #####################################
EBT_BRULE1="-p ipv4 -i $WRLSS_IF -j DROP"
EBT_BRULE2="-p arp -i $WRLSS_IF -j DROP"
if [ -n "$EBT_BRULE1" ] && [ `ebtables -t broute -L | grep -ice "$EBT_BRULE1"` != 1 ]; then
ebtables -t broute -I BROUTING $EBT_BRULE1
fi
if [ -n "$EBT_BRULE2" ] && [ `ebtables -t broute -L | grep -ice "$EBT_BRULE2"` != 1 ]; then
ebtables -t broute -I BROUTING $EBT_BRULE2
fi
############################################ IP TABLES RULES #############################################
if [ `iptables -L -v | grep -c $WRLSS_IF` == 0 ]; then
iptables -I INPUT -i $WRLSS_IF -m state --state NEW -j ACCEPT
iptables -I FORWARD -i $WRLSS_IF -o $TUN_IF -j ACCEPT
fi
if [ `iptables -t nat -L -v | grep -c $TUN_IF` == 0 ]; then
iptables -t nat -I POSTROUTING -s $WRLSS_IF_NTWK_ADDR/24 -o $TUN_IF -j MASQUERADE # Change /24 to the subnet that you will be using.
fi
############################################### HIDE SSID ################################################
if [ `nvram get "$WRLSS_IF"_closed` != 1 ] && [ $HIDE_SSID == 1 ]; then
nvram set "$WRLSS_IF"_closed=1
nvram commit
fi
if [ `nvram get "$WRLSS_IF"_closed` != 0 ] && [ $HIDE_SSID == 0 ]; then
nvram set "$WRLSS_IF"_closed=0
nvram commit
fi

A screenshot from router to prove which interface I use:
Last edited:

