mkaand
Occasional Visitor
Hello,
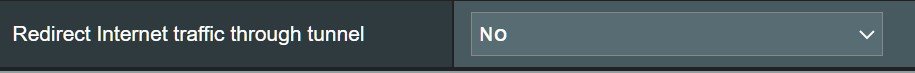
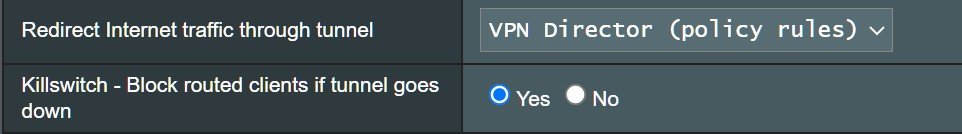
I just newly explored VPN Director feature. First I couldn't start VPN Director because I should choose VPN Director on VPN Client settings page. Now I can redirect my internet traffics to VPN connection for specific IPs. But I cannot make this route with FQDN (domain name). I used to use following config file for OpenVPN client:
route-gateway 10.10.3.1
keepalive 10 60
ping-timer-rem
allow-pull-fqdn
route snbforums.com 255.255.255.255 vpn_gateway
route smallnetbuilder.com 255.255.255.255 vpn_gateway
route pastebin.com 255.255.255.255 vpn_gateway
route tunein.com 255.255.255.255 vpn_gateway
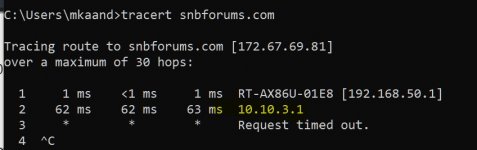
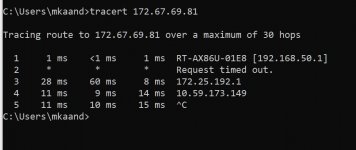
You can see allow-pull-fqdn let me indicate routes via domain name instead of IPs. Currently If I try to visit pastebin.com chrome shows not found. But If I refresh page I can access to pastebin.com. VPN Director is good for fixed ip<>domain routes. But if domain is behind Cloudflare or has more than one ip (load balancing on name server) VPN Director is not working properly. Maybe they can FQDN feature into VPN Director. Is should be great.
I just newly explored VPN Director feature. First I couldn't start VPN Director because I should choose VPN Director on VPN Client settings page. Now I can redirect my internet traffics to VPN connection for specific IPs. But I cannot make this route with FQDN (domain name). I used to use following config file for OpenVPN client:
route-gateway 10.10.3.1
keepalive 10 60
ping-timer-rem
allow-pull-fqdn
route snbforums.com 255.255.255.255 vpn_gateway
route smallnetbuilder.com 255.255.255.255 vpn_gateway
route pastebin.com 255.255.255.255 vpn_gateway
route tunein.com 255.255.255.255 vpn_gateway
You can see allow-pull-fqdn let me indicate routes via domain name instead of IPs. Currently If I try to visit pastebin.com chrome shows not found. But If I refresh page I can access to pastebin.com. VPN Director is good for fixed ip<>domain routes. But if domain is behind Cloudflare or has more than one ip (load balancing on name server) VPN Director is not working properly. Maybe they can FQDN feature into VPN Director. Is should be great.