ComputerSteve
Senior Member
So i'm using a vpn for my directv stream boxes, and I have them on client 1 with their specific IPs in VPN Director. This has been the way I have been setup for over a year. I use VPNMon-R3 to insure that the connection always stays active, & I use Domain Based VPN Routing to bypass the vpn for certain domains. I have also recently (About 3 months ago) installed Adguard home on the router. I am noticing a very weird problem that is happening randomly on the 4 OSPREY directv stream boxes... Every so often I will go to a box, and a message will be on the screen saying "no internet".. If I run an internet connection test on the box the internet is fine and passes the test. I can even reboot that specific box and it reboots with the same issue. I have found a fix which is to either remove it from the vpn then reconnect it meaning remove it from VPN director. Even toggling the VPN doesn't seem to fix it. If I don't put the box on a VPN then this problem doesn't happen. I have the IP's fixed based on the mac address. I don't think it's that the IP is changing. I can see that the ip isn't changing by verifying it inside the router / OSPREY DTV Box. I am wondering if Its adguard? the only changes I made with that are the upstream servers which I changed to:
tls://1dot1dot1dot1.cloudflare-dns.com
tls://one.one.one.one
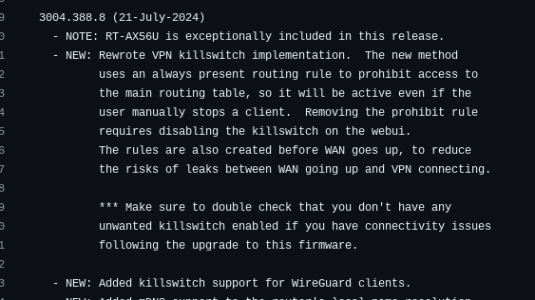
Why this problem is weird its because its random and then its only on 1 or 2 of the routed devices that are forced through the VPN. Meaning I can be watching TV on two of the boxes while the other two could be saying no internet. Also most of the time they all work without any problem.. So i'm at a loss. I am noticing this problem on firmware 3004.388.8_2.. I don't know if it's a routing problem because of domain based routing or an adguard problem but it's a weird problem.. maybe someone has some insight?
tls://1dot1dot1dot1.cloudflare-dns.com
tls://one.one.one.one
Why this problem is weird its because its random and then its only on 1 or 2 of the routed devices that are forced through the VPN. Meaning I can be watching TV on two of the boxes while the other two could be saying no internet. Also most of the time they all work without any problem.. So i'm at a loss. I am noticing this problem on firmware 3004.388.8_2.. I don't know if it's a routing problem because of domain based routing or an adguard problem but it's a weird problem.. maybe someone has some insight?