bayern1975
Very Senior Member
hello, i would like to know what setup is best secure for runing OpenVPN? here is my setup and would like to know if it ok....


If you lost a device, the exported config file on the device is going to contain the key/cert, won't it, and not the username/password, so wouldn't you want to regenerate the key/cert rather than revoke the username/password?What I then do, in the table on the General OpenVPN settings page, is give each client device a unique username and password so that if, say, I lost that device, I'd merely revoke the username/password pair for that device rather than having to set up OpenVPN from new again to generate fresh keys and certs followed by then have to reconfigure every client device. More importantly, with this Yes-No pairing, you have the added layer of username and passwords on top of PKI.
Feb 5 14:10:11 openvpn[1394]: Initialization Sequence Completed
Feb 5 14:14:42 openvpn[1394]: tls-crypt unwrap error: packet too short
Feb 5 14:14:42 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:48578
Feb 5 14:14:51 openvpn[1394]: tls-crypt unwrap error: packet too short
Feb 5 14:14:51 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:36664
Feb 5 14:15:17 openvpn[1394]: tls-crypt unwrap error: packet too short
Feb 5 14:15:17 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:59078
Feb 5 14:15:24 openvpn[1394]: tls-crypt unwrap error: packet too short
Feb 5 14:15:24 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:34055
Feb 5 14:15:28 openvpn[1394]: tls-crypt unwrap error: packet too short
Feb 5 14:15:28 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:34055
Feb 5 14:15:35 openvpn[1394]: tls-crypt unwrap error: packet too short
Feb 5 14:15:35 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:53631
Feb 5 14:15:36 openvpn[1394]: tls-crypt unwrap error: packet too short
Feb 5 14:15:36 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:53631
Feb 5 14:15:49 openvpn[1394]: tls-crypt unwrap error: packet too short
Feb 5 14:15:49 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:40312
Feb 5 14:15:53 openvpn[1394]: tls-crypt unwrap error: packet too short
Feb 5 14:15:53 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:40312
Feb 5 14:17:26 openvpn[1394]: 188.198.101.213 TLS: Initial packet from [AF_INET6]::ffff:188.198.101.213:56549, sid=5f54cea7 34e8a8f7
Feb 5 14:18:26 openvpn[1394]: 188.198.101.213 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Feb 5 14:18:26 openvpn[1394]: 188.198.101.213 TLS Error: TLS handshake failed
Feb 5 14:18:26 openvpn[1394]: 188.198.101.213 SIGUSR1[soft,tls-error] received, client-instance restarting
Feb 5 14:18:52 openvpn[1394]: 188.198.101.213 TLS: Initial packet from [AF_INET6]::ffff:188.198.101.213:50121, sid=c03e4883 3110ce1a
Feb 5 14:19:52 openvpn[1394]: 188.198.101.213 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Feb 5 14:19:52 openvpn[1394]: 188.198.101.213 TLS Error: TLS handshake failed
Feb 5 14:19:52 openvpn[1394]: 188.198.101.213 SIGUSR1[soft,tls-error] received, client-instance restartingIf you lost a device, the exported config file on the device is going to contain the key/cert, won't it, and not the username/password, so wouldn't you want to regenerate the key/cert rather than revoke the username/password?
I didn't realize you could have both. Does that improve the security of the tunnel, or just get around a key logger?
i change my configuration and now i can` t connect to my openvpn?

i get TLS errors when i try to connect?
Code:Feb 5 14:10:11 openvpn[1394]: Initialization Sequence Completed Feb 5 14:14:42 openvpn[1394]: tls-crypt unwrap error: packet too short Feb 5 14:14:42 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:48578 Feb 5 14:14:51 openvpn[1394]: tls-crypt unwrap error: packet too short Feb 5 14:14:51 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:36664 Feb 5 14:15:17 openvpn[1394]: tls-crypt unwrap error: packet too short Feb 5 14:15:17 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:59078 Feb 5 14:15:24 openvpn[1394]: tls-crypt unwrap error: packet too short Feb 5 14:15:24 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:34055 Feb 5 14:15:28 openvpn[1394]: tls-crypt unwrap error: packet too short Feb 5 14:15:28 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:34055 Feb 5 14:15:35 openvpn[1394]: tls-crypt unwrap error: packet too short Feb 5 14:15:35 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:53631 Feb 5 14:15:36 openvpn[1394]: tls-crypt unwrap error: packet too short Feb 5 14:15:36 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:53631 Feb 5 14:15:49 openvpn[1394]: tls-crypt unwrap error: packet too short Feb 5 14:15:49 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:40312 Feb 5 14:15:53 openvpn[1394]: tls-crypt unwrap error: packet too short Feb 5 14:15:53 openvpn[1394]: TLS Error: tls-crypt unwrapping failed from [AF_INET6]::ffff:188.198.101.213:40312 Feb 5 14:17:26 openvpn[1394]: 188.198.101.213 TLS: Initial packet from [AF_INET6]::ffff:188.198.101.213:56549, sid=5f54cea7 34e8a8f7 Feb 5 14:18:26 openvpn[1394]: 188.198.101.213 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Feb 5 14:18:26 openvpn[1394]: 188.198.101.213 TLS Error: TLS handshake failed Feb 5 14:18:26 openvpn[1394]: 188.198.101.213 SIGUSR1[soft,tls-error] received, client-instance restarting Feb 5 14:18:52 openvpn[1394]: 188.198.101.213 TLS: Initial packet from [AF_INET6]::ffff:188.198.101.213:50121, sid=c03e4883 3110ce1a Feb 5 14:19:52 openvpn[1394]: 188.198.101.213 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Feb 5 14:19:52 openvpn[1394]: 188.198.101.213 TLS Error: TLS handshake failed Feb 5 14:19:52 openvpn[1394]: 188.198.101.213 SIGUSR1[soft,tls-error] received, client-instance restarting
Are you connecting from Android, Windows or iOS? iOS default app has yet to be updated to support TLS-Crypt, while I am not sure about Android, but there is a good alternative app that supports TLS-Crypt. For Windows, if you update client to 2.4.0, you should be able to connect with TLS-Crypt on.i change my configuration and now i can` t connect to my openvpn?
i get TLS errors when i try to connect?
I'm confident that, by deleting your current client-device OpenVPN setup and importing the new .ovpn config file, you should be up and running provided you have entered the username/password pair on the router's General OpenVPN settings page.yes, i use openvpn over android phone. Didn't test with windows...
If you ever do use OpenVPN with Windows, you must open OpenVPN with administrator rights otherwise it won't work. (That's another one of Merlin's warnings; credit where it's due.)yes, i use openvpn over android phone. Didn't test with windows...
yes, I deleted and create new ovpn file....it working now with disabled TLS control channel security settings...I think we need new update of openvpn app for android?
It probably takes sometimes for both iOS and Android apps to get support for TLS-Crypt. An alternative app I was talking about is "OpenVPN for Android" which you can use for now while waiting for updates.yes, I deleted and create new ovpn file....it working now with disabled TLS control channel security settings...I think we need new update of openvpn app for android?
If you ever do use OpenVPN with Windows, you must open OpenVPN with administrator rights otherwise it won't work. (That's another one of Merlin's warnings; credit where it's due.)
OpenVPN 2.4.0 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Dec 27 2016
Windows version 6.2 (Windows 8 or greater) 64bit#!/bin/sh
CONFIG="$1"
source /usr/sbin/helper.sh
pc_append "tls-version-min 1.2" "$CONFIG"Many thanks, Martineau. That's good to know: the fewer things with admin rights the better. Much appreciated.If using Openvpn 2.4 Client this no longer true
Code:OpenVPN 2.4.0 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Dec 27 2016 Windows version 6.2 (Windows 8 or greater) 64bit
https://openvpn.net/index.php/open-source/downloads.html
View attachment 8463
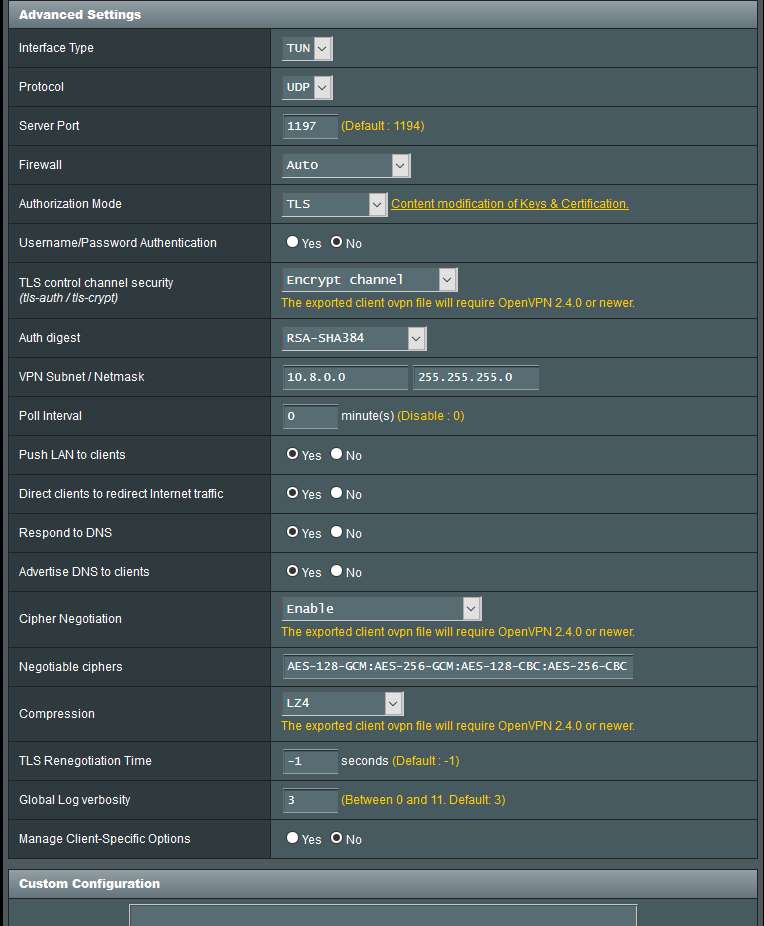
Negotiable ciphers AES-128-GCM:AES-256-GCM:AES-128-CBC:AES-256-CBCI hope this is not much of a threadjack but it is about trying to keep secure... While running 2.4.0 on the router as a server and there are clients who are not yet at 2.4.0, does the following line allow the 2.3.x clients to select AES-128-CBC or AES-256-CBC while allowing 2.4.0 clients use -GCM?

Welcome To SNBForums
SNBForums is a community for anyone who wants to learn about or discuss the latest in wireless routers, network storage and the ins and outs of building and maintaining a small network.
If you'd like to post a question, simply register and have at it!
While you're at it, please check out SmallNetBuilder for product reviews and our famous Router Charts, Ranker and plenty more!
