Tommy_Tom_123
New Around Here
Hi all,
I am currently using a RT-AX86u router running the latest Merlin 3004.388.8_2 firmware. I am using the Wireguard VPN client feature to have two devices tunning all their traffic over this VPN connection, which works great. The only issue I am facing is that these clients somehow use a mix of the local DNS as well as the DNS from the VPN server.
Configuration: Wireguard Profile that has a DNS configured in it (which is correctly read by AsusWRT Merlin, as it automatically fills the 'DNS server (optional)' field when loading in the Wireguard Profile). No further VPN profiles active, no DNS Director. The clients in question are a Chromecast with Google tv, and a Samsung TV.
Expected behaviour: the clients that are directed to use the VPN-Client feature should (only!) use the DNS server from the VPN profile.
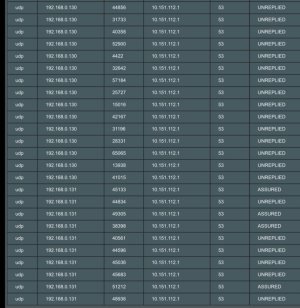
Actual behaviour: The clients use both the local, and the VPN DNS according to DNS leak websites
What I have tried to fix it so far:
- Use this VPN profile on a different device --> Iphone with Wireguard app. I tried this exact VPN profile and here it forces the device to use the DNS server from the VPN tunnel.
- Remove and reload VPN profile and Client in the router
- Use DNS Director to try to force the VPN DNS server on these clients
- Use VPN director to force this profile on my laptop to see if perhaps my clients are stubborn (but DNS leak also happens on this laptop)
- Disabling AIProtection
- reboot router
- Reinstall router from scratch
I saw similar posts on this forum where disabling DNS Director was the solution, but I am not using that feature in the first place.
Am I doing something wrong here, could this be a bug or is this working as designed?
Any help is much appreciated!
I am currently using a RT-AX86u router running the latest Merlin 3004.388.8_2 firmware. I am using the Wireguard VPN client feature to have two devices tunning all their traffic over this VPN connection, which works great. The only issue I am facing is that these clients somehow use a mix of the local DNS as well as the DNS from the VPN server.
Configuration: Wireguard Profile that has a DNS configured in it (which is correctly read by AsusWRT Merlin, as it automatically fills the 'DNS server (optional)' field when loading in the Wireguard Profile). No further VPN profiles active, no DNS Director. The clients in question are a Chromecast with Google tv, and a Samsung TV.
Expected behaviour: the clients that are directed to use the VPN-Client feature should (only!) use the DNS server from the VPN profile.
Actual behaviour: The clients use both the local, and the VPN DNS according to DNS leak websites
What I have tried to fix it so far:
- Use this VPN profile on a different device --> Iphone with Wireguard app. I tried this exact VPN profile and here it forces the device to use the DNS server from the VPN tunnel.
- Remove and reload VPN profile and Client in the router
- Use DNS Director to try to force the VPN DNS server on these clients
- Use VPN director to force this profile on my laptop to see if perhaps my clients are stubborn (but DNS leak also happens on this laptop)
- Disabling AIProtection
- reboot router
- Reinstall router from scratch
I saw similar posts on this forum where disabling DNS Director was the solution, but I am not using that feature in the first place.
Am I doing something wrong here, could this be a bug or is this working as designed?
Any help is much appreciated!