Hoping someone can point out something I've mis-configured somehow to remove this security issue.
I connect an RT-AC68U in repeater mode to the Guest network of the primary RT-AX86U router. Access Intranet is disabled for the Guest network, however any devices connected to the repeater can see all devices connected to the primary router, bypassing the access intranet = disabled setting. Any devices connected directly to the guest network do not have intranet access as expected.
Network Devices:
RT-AX86U primary router running Merlin 386.1_2
RT-AC68U repeater running Merlin 386.1_2
This setup replaces a configuration I have had in place for 4+ years (until the RT-N56U recently died): RT-AC68U primary router on Merlin 384.19, RT-N56U repeater bridge on Padavan 3.X.3.9-099. What was the primary RT-AC68U has now become the repeater, and the primary router is now a RT-AX86U.
Configuration:
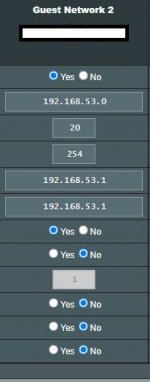
LAN Subnet 192.168.22.0/24 with primary router 192.168.22.1 and repeater configured to manual IP of 192.168.22.2 (Gateway and DNS on repeater set to 192.168.22.1).
DHCP range 192.168.22.20 - 192.168.22.254
SSID setup:
RT-AX86U SSIDs: PRIMARY and PRIMARY_5G, WPA2-Personal
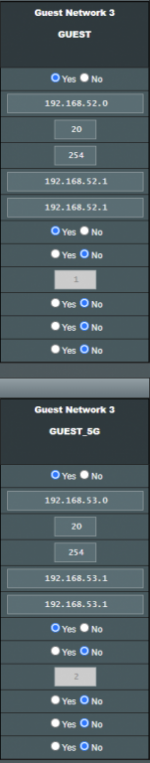
RT-AX86U Guest SSIDs: GUEST and GUEST_5G (configured in index 2), WPA2-Personal
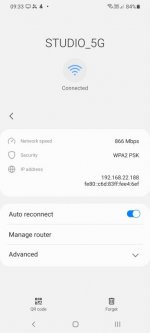
RT-AC68U SSIDs: STUDIO and STUDIO_5G, WPA2-Personal
(I had to disable the WPA2/WPA3-Personal option on the RT-AX86U because it stopped an old iPad and LG TV from connecting).
RT-AC68U joins the network as a repeater by connecting to the GUEST SSID of the RT-AX86U.
Scenario:
People connecting to the GUEST and STUDIO SSIDs only need to connect to the network for internet access.
GUEST and STUDIO SSIDs should be not be able to access devices on the primary network.
The repeater connecting to the GUEST SSID will then broadcast its own networks so they are completely isolated from the primary network.
By connecting the repeater to the GUEST network was how I had previously isolated the repeater network from the primary network as Access Intranet was set to disable on the GUEST networks.
Issue:
Any devices I connect to the STUDIO SSIDs on the repeater (via the GUEST SSID on the primary router) can see all devices on the Primary network. I do not want this, and they should be isolated because the GUEST network has Intranet access disabled.
Examples of this include:
- The Network Map client list on the Repeater Web UI shows all devices connected to the primary router.
- When opening a chromecast app (e.g. Foxtel, Prime Video, Netflix) I can see all chromecast devices connected to the primary network. This is actually how I discovered the problem. The STUDIO network doesn't have any chromecasts on it, yet the cast icon popped up in the apps, showing all chromecasts connected to the PRIMARY router. Guests connected to the STUDIO network should not be able to chromecast to devices on the primary network.
- When I do a network scan in a file explorer, I can see the PC on the primary network.
However when I connect a device directly to the GUEST SSID on the primary router, it is isolated from the main network as expected. The devices cannot see any other devices on the primary network.
This is only an issue for devices connected via the repeater.
It seems fairly easy to replicate. Setup a secondary router as a repeater for the GUEST network of the primary router with Access Intranet = Disable.
What I have tried:
1. AIMesh. I tried to achieve a similar setup by using "Sync to AIMesh Node" to get the GUEST network on index 1 to the second router. However I had a lot of issues with devices not staying connected (especially cameras connected to PRIMARY SSID) and general network latency from other devices. Disabling the Guest network in index 1 resolved this, but meant I couldn't get a guest network on the secondary router. Also AIMesh wouldn't allow me to segregate the LAN ports on the repeater off to the guest network.
2. Guest SSIDs in index 2 and 3. No difference.
3. Guest SSIDs in 2.4GHz and 5GHz. No difference.
What this now means is that if someone gives me access to the guest network of an Asus router, thinking I'll be isolated from their Intranet, they will actually be giving me full access to their network.
Surely this is a security issue?
I connect an RT-AC68U in repeater mode to the Guest network of the primary RT-AX86U router. Access Intranet is disabled for the Guest network, however any devices connected to the repeater can see all devices connected to the primary router, bypassing the access intranet = disabled setting. Any devices connected directly to the guest network do not have intranet access as expected.
Network Devices:
RT-AX86U primary router running Merlin 386.1_2
RT-AC68U repeater running Merlin 386.1_2
This setup replaces a configuration I have had in place for 4+ years (until the RT-N56U recently died): RT-AC68U primary router on Merlin 384.19, RT-N56U repeater bridge on Padavan 3.X.3.9-099. What was the primary RT-AC68U has now become the repeater, and the primary router is now a RT-AX86U.
Configuration:
LAN Subnet 192.168.22.0/24 with primary router 192.168.22.1 and repeater configured to manual IP of 192.168.22.2 (Gateway and DNS on repeater set to 192.168.22.1).
DHCP range 192.168.22.20 - 192.168.22.254
SSID setup:
RT-AX86U SSIDs: PRIMARY and PRIMARY_5G, WPA2-Personal
RT-AX86U Guest SSIDs: GUEST and GUEST_5G (configured in index 2), WPA2-Personal
RT-AC68U SSIDs: STUDIO and STUDIO_5G, WPA2-Personal
(I had to disable the WPA2/WPA3-Personal option on the RT-AX86U because it stopped an old iPad and LG TV from connecting).
RT-AC68U joins the network as a repeater by connecting to the GUEST SSID of the RT-AX86U.
Scenario:
People connecting to the GUEST and STUDIO SSIDs only need to connect to the network for internet access.
GUEST and STUDIO SSIDs should be not be able to access devices on the primary network.
The repeater connecting to the GUEST SSID will then broadcast its own networks so they are completely isolated from the primary network.
By connecting the repeater to the GUEST network was how I had previously isolated the repeater network from the primary network as Access Intranet was set to disable on the GUEST networks.
Issue:
Any devices I connect to the STUDIO SSIDs on the repeater (via the GUEST SSID on the primary router) can see all devices on the Primary network. I do not want this, and they should be isolated because the GUEST network has Intranet access disabled.
Examples of this include:
- The Network Map client list on the Repeater Web UI shows all devices connected to the primary router.
- When opening a chromecast app (e.g. Foxtel, Prime Video, Netflix) I can see all chromecast devices connected to the primary network. This is actually how I discovered the problem. The STUDIO network doesn't have any chromecasts on it, yet the cast icon popped up in the apps, showing all chromecasts connected to the PRIMARY router. Guests connected to the STUDIO network should not be able to chromecast to devices on the primary network.
- When I do a network scan in a file explorer, I can see the PC on the primary network.
However when I connect a device directly to the GUEST SSID on the primary router, it is isolated from the main network as expected. The devices cannot see any other devices on the primary network.
This is only an issue for devices connected via the repeater.
It seems fairly easy to replicate. Setup a secondary router as a repeater for the GUEST network of the primary router with Access Intranet = Disable.
What I have tried:
1. AIMesh. I tried to achieve a similar setup by using "Sync to AIMesh Node" to get the GUEST network on index 1 to the second router. However I had a lot of issues with devices not staying connected (especially cameras connected to PRIMARY SSID) and general network latency from other devices. Disabling the Guest network in index 1 resolved this, but meant I couldn't get a guest network on the secondary router. Also AIMesh wouldn't allow me to segregate the LAN ports on the repeater off to the guest network.
2. Guest SSIDs in index 2 and 3. No difference.
3. Guest SSIDs in 2.4GHz and 5GHz. No difference.
What this now means is that if someone gives me access to the guest network of an Asus router, thinking I'll be isolated from their Intranet, they will actually be giving me full access to their network.
Surely this is a security issue?