pusb87
Regular Contributor
Hi everyone.
This is my first post and I have looked around the forum for similar situations I am experiencing myself.
I have recently purchased the RT-AC68U and installed the Asuswrt-Merlin firmware 380.64.
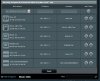
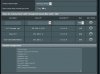
My VPN provider is Private Internet Access (PIA) and I have carefully followed the excellent guide from @yorgi on How to Setup a VPN Client including Policy Rules for PIA.
All seems to work very well using the PIA openvpn config files for UDP 1198 except when using Policy Rules and selecting the option to Block Routed Clients if the Tunnel goes down.
If I have the openvpn client running then all is well and I have good internet access.....however when i stop the client from running then i have to reboot the router to regain internet access.
Is this the expected behavior or is something not quite right ?
I am happy to post any additional information about my setup should it be required.
many thanks in anticipation of some help or advice
This is my first post and I have looked around the forum for similar situations I am experiencing myself.
I have recently purchased the RT-AC68U and installed the Asuswrt-Merlin firmware 380.64.
My VPN provider is Private Internet Access (PIA) and I have carefully followed the excellent guide from @yorgi on How to Setup a VPN Client including Policy Rules for PIA.
All seems to work very well using the PIA openvpn config files for UDP 1198 except when using Policy Rules and selecting the option to Block Routed Clients if the Tunnel goes down.
If I have the openvpn client running then all is well and I have good internet access.....however when i stop the client from running then i have to reboot the router to regain internet access.
Is this the expected behavior or is something not quite right ?
I am happy to post any additional information about my setup should it be required.
many thanks in anticipation of some help or advice