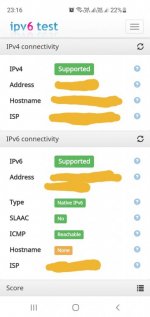
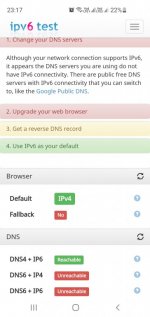
Martineau
Part of the Furniture
I highly recommend/use Xshell 7 (FREE for Personal use) with these key mappingsahh should have mentioned that. Sorry bout that. I have used Windows Terminal and have tried Bitvise SSH client. Both have the same problem. Up and down arrows work but anything with backspace/del does not work which is weird.
However, I have pushed
wireguard_manager Beta v4.14b6 which allows DISABLING the command buffer 'Pg-Up' feature, if the key mappings can't be altered.To upgrade use
Code:
e = Exit Script [?]
E:Option ==> uf dev
Code:
e = Exit Script [?]
E:Option ==> createconfigthen you may toggle the feature
Code:
e = Exit Script [?]
E:Option ==> pgupkey off
[✖] Use of 'PG-Up' key for command retrieval DISABLED