@TheLyppardMan
SSL traffic inspection by any "antivirus/security" software like ESET works like a middle man between your browser and real destination servers. Generally what you install into browsers/client OS is the self-signed CA certificate of the software i.e. ESET's. I'm sure you've done this step since you have ESET up and running (I assume. If not, then double check with ESET doc or support).
Without digressing into how ESET and alike work, to solve your issue you have two options.
You could have imported Pixelserv CA certificate into Windows trusted root CA certificate store. On Mac platform, the equivalent will be "System Roots" keychain. The right store or keychain is essential for ESET to pick it up I believe. I'm not sure if you've done it correctly.
Let's not spend more time on above option. though you may look into it further on another day if you're interested.
The second option and IMO the optimal solution is to ask ESET to skip SSL check on traffic designated to "pixelserv ip". There is overhead in ESET's inspection. Also, inspecting traffic between browsers and pixelserv-tls is unnecessary because pixelserv-tls only sits on your LAN and by design it does not do any harmful/malicious act.
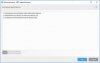
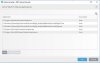
ESET has a feature known as "Protocol filtering / excluded by IP addresses" that does such selective SSL filtering. So add "pixelserv ip" to ESET's "excluded by IP addresses" list. I believe then you won't see any more warning/errors.
Here is a graphical guide from ESET:
https://support.eset.com/kb5833/?locale=en_US&viewlocale=en_US
Let me know if it works. If not, pls show a screenshot of warning/errors related to SSL/certificates that you may see...
SSL traffic inspection by any "antivirus/security" software like ESET works like a middle man between your browser and real destination servers. Generally what you install into browsers/client OS is the self-signed CA certificate of the software i.e. ESET's. I'm sure you've done this step since you have ESET up and running (I assume. If not, then double check with ESET doc or support).
Without digressing into how ESET and alike work, to solve your issue you have two options.
You could have imported Pixelserv CA certificate into Windows trusted root CA certificate store. On Mac platform, the equivalent will be "System Roots" keychain. The right store or keychain is essential for ESET to pick it up I believe. I'm not sure if you've done it correctly.
Let's not spend more time on above option. though you may look into it further on another day if you're interested.
The second option and IMO the optimal solution is to ask ESET to skip SSL check on traffic designated to "pixelserv ip". There is overhead in ESET's inspection. Also, inspecting traffic between browsers and pixelserv-tls is unnecessary because pixelserv-tls only sits on your LAN and by design it does not do any harmful/malicious act.
ESET has a feature known as "Protocol filtering / excluded by IP addresses" that does such selective SSL filtering. So add "pixelserv ip" to ESET's "excluded by IP addresses" list. I believe then you won't see any more warning/errors.
Here is a graphical guide from ESET:
https://support.eset.com/kb5833/?locale=en_US&viewlocale=en_US
Let me know if it works. If not, pls show a screenshot of warning/errors related to SSL/certificates that you may see...