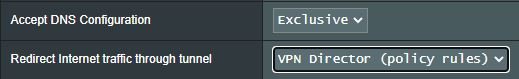
What I recommend is that you *ignore* the VPN provider's advice, and either use your normal ISP DNS servers on the WAN, or perhaps something else (e.g., 1.1.1.1 and 1.0.0.1), or even DoT (but specify Disabled for "Accept DNS configuration" in that case).
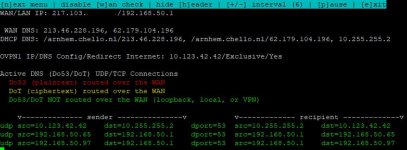
That's why all this is so tricky. There are lot of low level details regarding various settings and how they all relate and behave that make it a complex subject. That's why I created the DNS monitor, to help visualize what's actually happening.

Tutorial - How to monitor DNS traffic in real-time
The following script allows for real-time monitoring of DNS on the router for the purposes of knowing what DNS servers are in use, and which network interfaces are being used. https://pastebin.com/AGNF8cC8 Overview One of the most difficult aspects of the router for users is managing DNS. DNS...www.snbforums.com
I have previously used 1.1.1.1 before getting a VPN, so would happily use that again. I only enter the manual servers when I am ready to use the VPN director though right?
Leaving it as is, I am in theory bound to my VPN ones, or I am really bound to my ISP ones and therefore leaking, even though the test sites say I am not? Or I am misunderstanding what you have said?
I did read about your DNS monitor in another thread, but again because I have no SSH experience, shied away from it...
You need to use an SSH client to access the router's SSH server, and thus its command line. IIRC, Windows 10/11 does provide an SSH client via its own command line (CMD). There's also one available via PowerShell, or even the PuTTY app.
Ok, thanks, in order to do that I will need to amend the Service - Enable SSH on the system tab right? And then click LAN only?
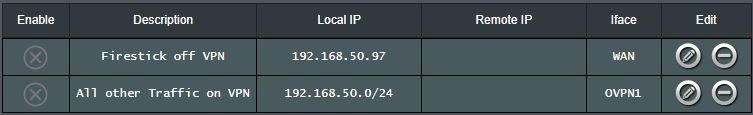
The whole reason I am doing this is to have my OpenVPN home server on the Firestick or as another VPN client on the router at another property and access Plex away from home or at the other property. Instead of fussing around with the VPN director, could I just use the OpenVPN on the firestick on top of the retail VPN client on the router? I think in a previous thread you said this wouldn't be possible, as my home server wouldn't see the Firestick, just my retail VPN client?
My thinking is that if I just carved out the Firestick via the VPN Director and then accessed any VPN/OpenVPN home server via the Firestick itself?
Last edited: