i am reading this thread with great interest as i just happened up it and the problems you guys are seeing might actually be a benefit for my usage. i'm currently still on 384.19 Merlin for a router (1900P) and access point (68u). with that older firmware, the guest network on the AP cannot be isolate from the intranet which is not the way i would want it to operate. i'd like to keep my IoT devices on the guest network so they can't touch my main network or my other devices.
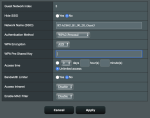
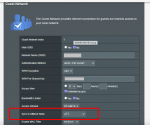
can anyone show me the guest network "setting screen" for 386? is there a check box that allows me to disable intranet access for guest network devices? (that doesn't exist in 384 in AP mode, but it does exist as an option for the guest network on my main router)
thanks for sharing your experiences. if its a workable option (i was waiting for Merlin 386 to hit final release), i may upgrade my AP to the standard Asus firmware (386) and leave my router operating with 384.19 Merlin.
can anyone show me the guest network "setting screen" for 386? is there a check box that allows me to disable intranet access for guest network devices? (that doesn't exist in 384 in AP mode, but it does exist as an option for the guest network on my main router)
thanks for sharing your experiences. if its a workable option (i was waiting for Merlin 386 to hit final release), i may upgrade my AP to the standard Asus firmware (386) and leave my router operating with 384.19 Merlin.