Thanks to everyone for helping me take a deep dive into the inner workings of Unbound and getting this working as advertised over a VPN tunnel! I truly appreciate your knowledge and expertise on this complex subject!
@dave14305 @SomeWhereOverTheRainBow @chongnt @Twiglets and others!
v2.55b4 - (Revisions as of May 6, 2023)
- MAJOR: Added major functionality to integrate more closely with Unbound! Unbound allows you to become your own DNS resolver, so you don't have to rely on other DNS providers (like from your ISP, Google, Quad9, etc.), and helps somewhat with privacy - because who knows what they log on their end, right?

The downside with Unbound is that the traffic you generate for your own DNS lookups to root servers or other authoritative servers is not encrypted... which would allow your ISP (or others) to still snoop on your plaintext port 53 DNS queries. So here's the good news -- this Unbound modification (thanks to
@Martineau/Swinson) forces all plaintext port 53 traffic that Unbound generates for DNS lookups over your VPN tunnel instead! This means your internet activity is even more secure from your ISP (or others) prying eyes. Please note, this is not an end-all-be-all fix to keep all DNS lookups private, but it certainly helps get you closer. This update will now require that Unbound is installed and running, and will download and/or apply other scripts to the following files:
- /jffs/scripts/nat-start
- /jffs/scripts/openvpn-event
- /jffs/scripts/post-mount
- /jffs/addons/unbound/unbound_DNS_via_OVPN.sh
-NOTE: VPNMON-R2 does not play any role in manipulating Unbound or the associated scripts in any way... it continues to function as it normally does. Except now, as openvpn events fire off as VPN tunnels are disconnected or established, this will allow these scripts to work in harmony with each other to force Unbound traffic over the VPN tunnel. Playing with these scripts and modifications isn't for the feint of heart, and may take some serious troubleshooting skills to get it configured right if something doesn't work straight out of the gate.
Beta Download:
Code:
curl --retry 3 "https://raw.githubusercontent.com/ViktorJp/VPNMON-R2/master/vpnmon-r2-2.55b4.sh" -o "/jffs/scripts/vpnmon-r2.sh" && chmod 755 "/jffs/scripts/vpnmon-r2.sh"
Significant Screenshot!
On the second config page, you'll find the ability to enable the Unbound/VPN integration functionality.
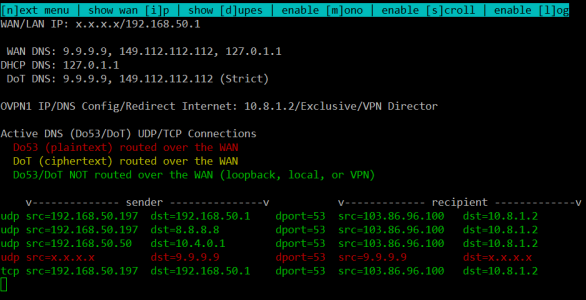
How do you know if it's working?
First... using the DNSMON tool (linked in the [
OP]... if you see that the sender SRC and recipient DST match your VPN IP (in my case, 10.8.3.4), then you are sending/receiving over your active VPN connection. Remember... green is good!

Second, taking at look at the
https://dnscheck.tools/ site... if you see your public VPN IP/exit and DNS resolvers are the same IP, then your VPN IP is effectively acting as your DNS resolver:
You can get even more detail running tcpdumps... but these 2 indicators above are a good sign things are working!