Thanks again @eibgard. TBH I am amazed at your ability to switch between multiple threads at the same time and still maintain continuity of the context. And I am also extremely grateful for that.
Just to confirm - based on your previous advice I did not opt for the username-as-common-name approach and stayed with the individual certificates. For the client router I generated a certificate and key with a common name of cn_itnc by following the instructions in the post by
@jsshapiro.
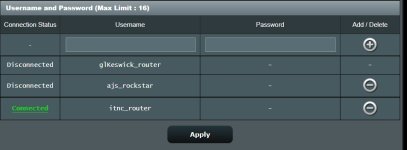
Now here are the user names configured on the server
View attachment 39877
And here is the list of Allowed Clients:
View attachment 39874
and with the client ovpn connection activated on the server I see a file called /tmp/etc/openvpn/server1/ccd/cn_itnc that contains an iroute of 192.168.50.0 255.255.255.0
On the client router here is what I configured for the OVPN client:
View attachment 39876
In the client OPVN config dialog I uploaded a .ovpn file called itnc.ovpn created by editing the .ovpn file exported from the server to replace the certificate and key for 'client' with the certificate and key I generated for cn_itnc (as described in the posting by
@jsshapiro).
You'll see in my client definition I included username and password. Seeing that these are optional I wondered whether by including username and password this was in some way overriding or conflicting with what is in the cn_itnc.ovpn configuration file. I created another profile without the optional username and password and uploaded cn_itnc.ovpn but when I try to activate that new profile it does not activate and the timer just ticks around until I click to deactivate.
I then updated the new profile to manually edit the certificates and keys to clear the client security certificates and keys and paste in those I had generated for cn_itnc just in case the keys embedded in the cn_itnc.ovpn configuration file had somehow got corrupted. But again this profile would not activate without the optional username and password.
So if I'm understanding you correctly it looks like everything is set up as expected but something is still blocking. I'm wondering if switching to Merlin might be a next step, the problem being I think I could only do that on the client router because I would need to VPN into the server router and I guess when I loaded Merlin all my stock ASUS-WRT config would disappear and I'd be dead in the water at that point.
Any idea what I can try next? Is there a way to capture the traffic between the routers to see where the route gets broken?
Thanks again for sharing your expertise and your patience and understanding for a novice.
Andy