Looking for some help / suggestions
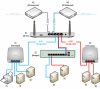
ISP Modem/Router1 >> Switch1>Device 1
>Device 2
>Network Printer
ISP Modem/Router2 >>> Router (dd-wrt)>>Switch2>Device 3
>Device 4
>>Device 5
>>Device 6
The dual ISP Modem/Routers are a bit over kill but it is a result of signing a deal with the ISP for lower rates that they are giving us 2 modem/routers.
I need to subnet off devices 4,5 and 6 from the ISP router hence the router (dd-wrt) use.
The devices 3 & 4 are at location in the building where running a second cable is difficult so they are both using the same wired cable for all their traffic. I want to bridge/route all traffic for device 3 over to ISP modem/Router1 and have that router do DHCP for devices 1 -3 and the network printer.
Do I do this bridging via MACID of device 3?
Any help regarding this would be greatly appreciated as I am banging head against desk here
ISP Modem/Router1 >> Switch1>Device 1
>Device 2
>Network Printer
ISP Modem/Router2 >>> Router (dd-wrt)>>Switch2>Device 3
>Device 4
>>Device 5
>>Device 6
The dual ISP Modem/Routers are a bit over kill but it is a result of signing a deal with the ISP for lower rates that they are giving us 2 modem/routers.
I need to subnet off devices 4,5 and 6 from the ISP router hence the router (dd-wrt) use.
The devices 3 & 4 are at location in the building where running a second cable is difficult so they are both using the same wired cable for all their traffic. I want to bridge/route all traffic for device 3 over to ISP modem/Router1 and have that router do DHCP for devices 1 -3 and the network printer.
Do I do this bridging via MACID of device 3?
Any help regarding this would be greatly appreciated as I am banging head against desk here