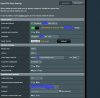
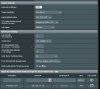
I am on 384.15 for now on my RT-AC86U. Perhaps I should upgrade to 384.17 then.
I see, the routing rules via iptables would then be reduntant.
But iptables doesn't route, it filters, both routing (to get packets to go where they should) and filters (eg. masquerade when needed etc.) do just that filter and perhaps modify packets as they pass through or drop, or reject etc.
I don't know for sure but 384.15 should have the client split-tunnel functionality already so what's needed should already be present. The challenge is understanding what scripts are executed and when so that you can inspect them to see if you can identify where incoming packets/connections are being blocked.
Well, I am certain that the policy section is set accordingly. Would you mind explaining what you mean by disable incoming firewall an internal ip-address? Perhaps I am missing something here...
As I say I don't have a Merlin install available atm. but there is an option (a radio button, that I saw when I last looked) on the client VPN setup page in one of the sections toward the top whose text include words like "incoming" and "block". I can't remember the wording but it should stand out if you look for it. It certainly looked like it should be what's needed to allow incoming connections. Working out why it doesn't is probably the key to solving this problem.
Ian