blitzkrieg
Occasional Visitor
Hi all
I've an RT-AC66U_B1 running Merlin's 380.67.
OpenVPN setup as follows:
TUN. Push LAN to clients. Direct clients to redirect Internet traffic. Respond to DNS. Advertise DNS to clients.
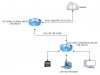
A DLink router is connected to the Asus through each other's LAN port and in the same 192.168.4.0/25 subnet. So it is essentially a switch.
I can connect to OpenVPN successfully and able to access a NAS server no problem. But I can't ping nor access the DLink router 192.168.4.2 while in OpenVPN. However, I can ping the PCs, Asus router and Android devices.
Any additional routing/iptables need to be added?
Here's the untouched iptables:
Here's the netstat routing table:
Simple network view:
OpenVPN setting: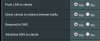
I've an RT-AC66U_B1 running Merlin's 380.67.
OpenVPN setup as follows:
TUN. Push LAN to clients. Direct clients to redirect Internet traffic. Respond to DNS. Advertise DNS to clients.
A DLink router is connected to the Asus through each other's LAN port and in the same 192.168.4.0/25 subnet. So it is essentially a switch.
I can connect to OpenVPN successfully and able to access a NAS server no problem. But I can't ping nor access the DLink router 192.168.4.2 while in OpenVPN. However, I can ping the PCs, Asus router and Android devices.
Any additional routing/iptables need to be added?
Here's the untouched iptables:
Code:
/root# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere
ACCEPT udp -- anywhere anywhere udp dpt:1194
DROP icmp -- anywhere anywhere icmp echo-request
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
DROP all -- anywhere anywhere state INVALID
PTCSRVWAN all -- anywhere anywhere
PTCSRVLAN all -- anywhere anywhere
ACCEPT all -- anywhere anywhere state NEW
ACCEPT all -- anywhere anywhere state NEW
ACCEPT udp -- anywhere anywhere udp spt:bootps dpt:bootpc
INPUT_ICMP icmp -- anywhere anywhere
DROP all -- anywhere anywhere
Chain FORWARD (policy DROP)
target prot opt source destination
ipttolan all -- anywhere anywhere
iptfromlan all -- anywhere anywhere
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT all -- anywhere anywhere
DROP all -- anywhere anywhere
DROP all -- anywhere anywhere state INVALID
ACCEPT all -- anywhere anywhere
SECURITY all -- anywhere anywhere
NSFW all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate DNAT
ACCEPT all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain ACCESS_RESTRICTION (0 references)
target prot opt source destination
Chain FUPNP (0 references)
target prot opt source destination
Chain INPUT_ICMP (1 references)
target prot opt source destination
RETURN icmp -- anywhere anywhere icmp echo-request
RETURN icmp -- anywhere anywhere icmp timestamp-request
ACCEPT icmp -- anywhere anywhere
Chain NSFW (1 references)
target prot opt source destination
Chain PControls (0 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere
Chain PTCSRVLAN (1 references)
target prot opt source destination
Chain PTCSRVWAN (1 references)
target prot opt source destination
Chain SECURITY (1 references)
target prot opt source destination
RETURN tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/SYN limit: avg 1/sec burst 5
DROP tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/SYN
RETURN tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/RST limit: avg 1/sec burst 5
DROP tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/RST
RETURN icmp -- anywhere anywhere icmp echo-request limit: avg 1/sec burst 5
DROP icmp -- anywhere anywhere icmp echo-request
RETURN all -- anywhere anywhere
Chain iptfromlan (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere account: network/netmask: 192.168.4.0/255.255.255.128 name: lan
RETURN all -- anywhere anywhere account: network/netmask: 192.168.4.0/255.255.255.128 name: lan
Chain ipttolan (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere account: network/netmask: 192.168.4.0/255.255.255.128 name: lan
RETURN all -- anywhere anywhere account: network/netmask: 192.168.4.0/255.255.255.128 name: lan
Chain logaccept (0 references)
target prot opt source destination
LOG all -- anywhere anywhere state NEW LOG level warning tcp-sequence tcp-options ip-options prefix "ACCEPT "
ACCEPT all -- anywhere anywhere
Chain logdrop (0 references)
target prot opt source destination
LOG all -- anywhere anywhere state NEW LOG level warning tcp-sequence tcp-options ip-options prefix "DROP "
DROP all -- anywhere anywhereHere's the netstat routing table:
Code:
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
44.125.x.1 0.0.0.0 255.255.255.255 UH 0 0 0 eth0
192.168.4.0 0.0.0.0 255.255.255.128 U 0 0 0 br0
10.8.0.0 0.0.0.0 255.255.255.128 U 0 0 0 tun21
44.125.x.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
127.0.0.0 0.0.0.0 255.0.0.0 U 0 0 0 lo
0.0.0.0 44.125.x.1 0.0.0.0 UG 0 0 0 eth0
OpenVPN setting: