Dogzdongliz
New Around Here
Hi everyone, my first post so a little nervous.
I'm after some advice on the way I've set up my home network.
A little background...
My current setup is a basic AC87U running Merlin, I use DDNS & VPN into my network when away.
The only port I every have open is 34200 for plex for remote access for friends, everything else
I access via the AC87U VPN server.
My home network consists of the usual stuff Xbox's, smartphones, wireless speakers etc. I run an unraid server, have the basic dockers, plex, sab, radarr, sonarr, transmission & pihole.
Transmission & Sab go through a VPN client configured on the AC87U.
This setup has served me well for years, but something has come along that's very tempting.
"Vodafone Unlimited data plans".
On my home broadband connection, my speeds are 27Mbps down & 8Mbps up, this is not to bad, but Vodafone gives me 180Mbps down & 40 up!
Now after some testing with a Vodafone sim & a 4G router in modem mode, I.ve come across a pitfall.
It seems that Vodafone uses carrier-grade nat & it's causing me havoc with my VPN server & plex remote access, due to the double natting.
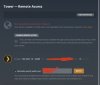
The first thing I concentrated on was Plex remote access & I now have a working but I'm not entirely sure if it's safe & what consequences this setup has.
I use Torguard for my VPN provider & they allow port forwarding, so I setup a port forward (33445) & made the vpn client on my AC87U connect to the same IP every time.
The setup is as follows;
Plex (192.168.1.15) routed via AU87u built-in VPN client to torguard.
iptables set on the AC87U are set as follows;
iptables -I FORWARD -i tun15 -p udp -d 192.168.1.15 --dport 33445 -j ACCEPT
iptables -t nat -I PREROUTING -i tun15 -p udp --dport 33445 -j DNAT --to-destination 192.168.1.15
Now, this is the bit that concerns me, for this to work, I need to change the "Inbound Firewall" to "allow" on the client VPN settings page.
I'm now sure what else this is allowing in from the VPN, I'm hoping someone will be able to educate me a little.
If the above is ok, my next plan is to run a OpenVPN server on the network and apply the same methodology as the plex server.
Look forward to some replies, & hopefully not "SHUT IT DOWN NOW" lol
Cheers
Dogz
I'm after some advice on the way I've set up my home network.
A little background...
My current setup is a basic AC87U running Merlin, I use DDNS & VPN into my network when away.
The only port I every have open is 34200 for plex for remote access for friends, everything else
I access via the AC87U VPN server.
My home network consists of the usual stuff Xbox's, smartphones, wireless speakers etc. I run an unraid server, have the basic dockers, plex, sab, radarr, sonarr, transmission & pihole.
Transmission & Sab go through a VPN client configured on the AC87U.
This setup has served me well for years, but something has come along that's very tempting.
"Vodafone Unlimited data plans".
On my home broadband connection, my speeds are 27Mbps down & 8Mbps up, this is not to bad, but Vodafone gives me 180Mbps down & 40 up!
Now after some testing with a Vodafone sim & a 4G router in modem mode, I.ve come across a pitfall.
It seems that Vodafone uses carrier-grade nat & it's causing me havoc with my VPN server & plex remote access, due to the double natting.
The first thing I concentrated on was Plex remote access & I now have a working but I'm not entirely sure if it's safe & what consequences this setup has.
I use Torguard for my VPN provider & they allow port forwarding, so I setup a port forward (33445) & made the vpn client on my AC87U connect to the same IP every time.
The setup is as follows;
Plex (192.168.1.15) routed via AU87u built-in VPN client to torguard.
iptables set on the AC87U are set as follows;
iptables -I FORWARD -i tun15 -p udp -d 192.168.1.15 --dport 33445 -j ACCEPT
iptables -t nat -I PREROUTING -i tun15 -p udp --dport 33445 -j DNAT --to-destination 192.168.1.15
Now, this is the bit that concerns me, for this to work, I need to change the "Inbound Firewall" to "allow" on the client VPN settings page.
I'm now sure what else this is allowing in from the VPN, I'm hoping someone will be able to educate me a little.
If the above is ok, my next plan is to run a OpenVPN server on the network and apply the same methodology as the plex server.
Look forward to some replies, & hopefully not "SHUT IT DOWN NOW" lol
Cheers
Dogz