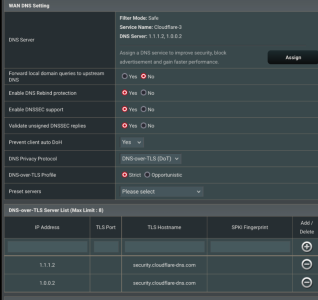
I've been using Merlin builds for several years on my simple home network, with great satisfaction. Just got an RT-BE86U and I'm trying to stop my ISP being able to see my DNS queries. This is the first time that I've attempted to use DoH, so please bear with me if I've made some simple mistakes. Here are my WAN DNS settings (FW 3006.102.3):

In addition, in the Privacy and Security settings of all my browsers (Chrome, Brave, Firefox) on Ubuntu 24.04.1 LTS and Android 14 I've set DoH to Quad9. When I test with https://on.quad9.net/ I get the response "Yes, you are using Quad9" in all cases. BUT when I do an extended test at dnsleaktest.com it always shows just a single server belonging to my ISP, which implies to me that my ISP can still inspect my DNS queries. (A little wrinkle is if I select Cloudflare in the DoH section of the browser settings, then the leaktest shows Cloudflare as the server.) I have a USB stick plugged into the router with Entware and Diversion plus swap file installed.
UPDATE: Previously DNS Director was off. Now I've set it to Global Redirection, Quad9, no exceptions, no user defined servers set on that page. Saved and rebooted. Flushed the Ubuntu DNS cache. Dnsleaktest still shows my ISP's server.
What am I doing wrong, or have I simply misunderstood the result of the leaktest?
In addition, in the Privacy and Security settings of all my browsers (Chrome, Brave, Firefox) on Ubuntu 24.04.1 LTS and Android 14 I've set DoH to Quad9. When I test with https://on.quad9.net/ I get the response "Yes, you are using Quad9" in all cases. BUT when I do an extended test at dnsleaktest.com it always shows just a single server belonging to my ISP, which implies to me that my ISP can still inspect my DNS queries. (A little wrinkle is if I select Cloudflare in the DoH section of the browser settings, then the leaktest shows Cloudflare as the server.) I have a USB stick plugged into the router with Entware and Diversion plus swap file installed.
UPDATE: Previously DNS Director was off. Now I've set it to Global Redirection, Quad9, no exceptions, no user defined servers set on that page. Saved and rebooted. Flushed the Ubuntu DNS cache. Dnsleaktest still shows my ISP's server.
What am I doing wrong, or have I simply misunderstood the result of the leaktest?
Last edited: