You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
DoT
- Thread starter umrico
- Start date
ColinTaylor
Part of the Furniture
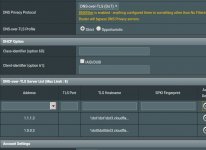
Too small to read.
Attachments
Diamond67
Senior Member
No, imho.Is this any better?
dave14305
Part of the Furniture
That’s not a good idea, and I don’t think the UI lets you do that. Why do you suggest that?leave the DNS server1 and DNS server2 fields blank
RAH-66
Senior Member
for only use DoT - TLS port 853, those fields use port 53That’s not a good idea, and I don’t think the UI lets you do that. Why do you suggest that?
Mutzli
Very Senior Member
With above settings you'll have devices that will ignore the routers DNS settings, but you can force them to use the routers DNS.
Use these setting:

Next set your DNSFilter in the LAN settings to router:

Now all of your traffic should go through 1.0.0.2. You can check this by tracking the outgoing traffic. Connect to the router by SSH console and enter the following command:
When you follow the log, you'll see the DNS request which all should now go through 1.0.0.2 or 1.1.1.2. You can also track the connection to see if they are secure on port 853 or unsecure on port 53.
Use these setting:
Next set your DNSFilter in the LAN settings to router:
Now all of your traffic should go through 1.0.0.2. You can check this by tracking the outgoing traffic. Connect to the router by SSH console and enter the following command:
Code:
tcpdump -ni eth0 -p port 53 or port 853When you follow the log, you'll see the DNS request which all should now go through 1.0.0.2 or 1.1.1.2. You can also track the connection to see if they are secure on port 853 or unsecure on port 53.
Thank you so much!!!!!!With above settings you'll have devices that will ignore the routers DNS settings, but you can force them to use the routers DNS.
Use these setting:
View attachment 30808
Next set your DNSFilter in the LAN settings to router:
View attachment 30809
Now all of you traffic should go through 1.0.0.2. You can check this by tracking the outgoing traffic. Connect to the router by SSH console and enter the following command:
Code:tcpdump -ni eth0 -p port 53 or port 853
When you follow the log, you'll see the DNS request which all should now go through 1.0.0.2 or 1.1.1.2. You can also track the connection to see if they are secure on port 853 or unsecure on port 53.
RAH-66
Senior Member
check it yourself and see the differenceWhen you follow the log, you'll see the DNS request which all should now go through 1.0.0.2 or 1.1.1.2. You can also track the connection to see if they are secure on port 853 or unsecure on port 53.
Mutzli
Very Senior Member
Those DNS servers on port 53 are only in use at boot up, when the router doesn't yet start the DNSSEC service. So instead of using your ISP's DNS service it would use the DNS servers defined here.for only use DoT - TLS port 853, those fields use port 53
I checked my connection and it does what it supposed to do and route everything through port 853. 0 requests on port 53.
JJohnson1988
Regular Contributor
The Cloudflare team never announced it, but I believe they have DoT over 1.1.1.2 as well as 1.1.1.3. However, it was my understanding that the TLS hostname is now security.cloudflare-dns.com due to the standard hostname being cumbersome (e.g. 1dot1dot1dot1.cloudflare-dns.com). Maybe someone can confirm?
Mutzli
Very Senior Member
They are DoT ready, at least for the last 3-4 months.The Cloudflare team never announced it, but I believe they have DoT over 1.1.1.2 as well as 1.1.1.3. However, it was my understanding that the TLS hostname is now security.cloudflare-dns.com due to the standard hostname being cumbersome (e.g. 1dot1dot1dot1.cloudflare-dns.com). Maybe someone can confirm?
dave14305
Part of the Furniture
Using DNS Rebind Protection with a filtering service like Cloudflare for Families changes the response you receive. Instead of 0.0.0.0, you get an empty response due to the rebind protection, and you get a syslog message about the potential rebind attack.
Ultimately, the domain is still prevented from being resolved, but not in the way the service intended.
Code:
Feb 15 22:47:02 dnsmasq[7522]: possible DNS-rebind attack detected: playboy.comMutzli
Very Senior Member
What's the use case for rebind protection if it's not necessary when using a filtering service?Using DNS Rebind Protection with a filtering service like Cloudflare for Families changes the response you receive. Instead of 0.0.0.0, you get an empty response due to the rebind protection, and you get a syslog message about the potential rebind attack.
Ultimately, the domain is still prevented from being resolved, but not in the way the service intended.Code:Feb 15 22:47:02 dnsmasq[7522]: possible DNS-rebind attack detected: playboy.com
RAH-66
Senior Member
a logical question - why fill in these fields if they are ignored?Those DNS servers on port 53 are only in use at boot up, when the router doesn't yet start the DNSSEC service. So instead of using your ISP's DNS service it would use the DNS servers defined here.
I checked my connection and it does what it supposed to do and route everything through port 853. 0 requests on port 53.
szl
New Around Here
The Cloudflare team never announced it, but I believe they have DoT over 1.1.1.2 as well as 1.1.1.3. However, it was my understanding that the TLS hostname is now security.cloudflare-dns.com due to the standard hostname being cumbersome (e.g. 1dot1dot1dot1.cloudflare-dns.com). Maybe someone can confirm?
security.cloudflare-dns.com -> 1.1.1.2, 1.0.0.2, 2606:4700:4700::1112, 2606:4700:4700::1002
family.cloudflare-dns.com -> 1.1.1.3, 1.0.0.3, 2606:4700:4700::1113, 2606:4700:4700::1003
source here
Mutzli
Very Senior Member
In case DNSSec fails.a logical question - why fill in these fields if they are ignored?
And if you want routing to fail if DNSSec and DoT fails? Leave them blank? That is my intent. Or does it simply just send the DNS to my ISP if it fails? I don't want that to happen.In case DNSSec fails.
I am entirely trying to resolve DNS through DoT and do not want my ISP to ever see my queries.
Your router needs to talk to an NTP server to set its clock before encryption can be used. So, no DoT without a working regular DNS to set that clock first.for only use DoT - TLS port 853, those fields use port 53
Similar threads
- Replies
- 7
- Views
- 553
- Replies
- 3
- Views
- 479
- Replies
- 18
- Views
- 1K
Similar threads
| Thread starter | Title | Forum | Replies | Date |
|---|---|---|---|---|
|
|
DNS Director / DoT over TLS | Asuswrt-Merlin | 18 | |
| C | DOT & IoT Devices | Asuswrt-Merlin | 3 | |
| L | Suggestion: DNS Director, add optional compatibility with DOT | Asuswrt-Merlin | 2 |
Similar threads
-
-
-
Suggestion: DNS Director, add optional compatibility with DOT
- Started by Linuxer
- Replies: 2
Latest threads
-
-
Release RT-BE92U Firmware version 3.0.0.6_102_37548
- Started by Spartan
- Replies: 1
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!