v1.5.5-beta11 Release:
***Disclaimer: This is a beta release and has been untested***
***This is an additional beta release due to unresolved issues in v1.5.5-beta10***
Manually upgrade to this beta by running the following command" ***Allow for cronjob to relaunch the script***
Code:
/usr/sbin/curl -s "https://raw.githubusercontent.com/Ranger802004/asusmerlin/main/wan-failover_v1.5.5-beta11.sh" -o "/jffs/scripts/wan-failover.sh" && chmod 755 /jffs/scripts/wan-failover.sh && sh /jffs/scripts/wan-failover.sh restart
To revert back to Production Release:
Code:
/jffs/scripts/wan-failover.sh update
***Highlight: While in Load Balancing Mode, OpenVPN Split Tunneling can be Disabled defaulting to WAN0 and failover to WAN1 if WAN0 fails***
***Highlight: Email Notifications will be sent for Load Balancing Mode if a WAN failure occurs.***
***Highlight: YazFi will be triggered to update if installed and running during Failover.***
***Highlight: Debug Logs can be generated to help diagnose issues. To enable set System Log > Log only messages more urgent than: debug***
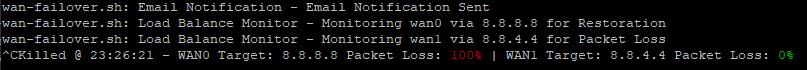
***Highlight: When running script in console, Packet Loss is actively displayed. 0% will be displayed in Green, 100% will be displayed in Red, and 1% - 99% will be displayed in Yellow.***
Example: Load Balance Mode actively monitoring both WAN0 and WAN.
View attachment 42645
***WARNING: Kill Mode will now delete cron job, use restart mode to schedule script to restart***
Release Notes:
v1.5.5-beta11
- General optimization of script logic
- If AdGuard is running or AdGuard Local is enabled, Switch WAN function will not update the resolv.conf file. (Collaboration with SomeWhereOverTheRainbow)
- Optimized the way script loads configuration variables.
- Service restarts will dynamically check which services need to be restarted.
- Optimized Boot Delay Timer functionality and changed logging messages to clarify how the Boot Delay Timer effects the script startup.
- WAN Status will now check if a cable is unplugged.
- Resolved issues with Load Balancing Mode introduced in v1.5.4
- Enhancements to Load Balancing Mode
- When in Load Balancing Mode, OpenVPN Split Tunneling can be disabled where remote addresses will default to WAN0 and failover to WAN1 if WAN0 fails and back to WAN0 when it is restored. This can be changed in Configuration file using the Setting: OVPNSPLITTUNNEL (1 = Enabled / 0 = Disabled).
- Corrected issue with Cron Job creation.
- Corrected issues with IP Rules creation for Target IP Addresses.
- When in Load Balance Mode, script will create IPTables Mangle rules for marking packets if they are missing. This is to correct an issue with the firmware.
- Increased email skip default delay to 180 seconds additional to Boot Delay Timer. Adjustable in configuration file using Setting: SKIPEMAILSYSTEMUPTIME (Value is in seconds).
- Script will check for supported ASUS Merlin Firmware Versions
- Script will verify System Binaries are used over Optional Binaries
- Added email functionality for Load Balancing Mode. If a WAN Interface fails, an email notification will be sent if enabled.
- Corrected issue where temporary file for mail would not have correct write permissions to create email for notification.
- Script will now create NAT Rules for services that are enabled.
- Load Balancing Rule Priority, WAN0/WAN1 Route Tables, FW Marks/Masks, IP Rule Priorities, and OpenVPN WAN Priority (Split Tunneling Disabled) are now all customizable using the configuration file. Recommended to leave default unless necessary to change.
- WAN Interface restarts during WAN Status checks will only wait 30 seconds maximum to check status again.
- Corrected issue where Monitor mode would stay running in background, now will exit background process when escaped with Ctrl + C.
- Added a restart mode to reload WAN Failover, use argument "restart". Config, Update, and Restart Mode will wait before cronjob cycle to kill script and allow cron job to reload script.
- Kill Mode will now delete the cron job to prevent WAN Failover from relaunching.
- If YazFi is installed and has a scheduled Cron Job, WAN Failover will trigger YazFi to update if installed in default location (/jffs/scripts/YazFi).
- Configured debug logging, to enable debug logging, set System Log > Log only messages more urgent than: debug
- Load Balancer will now work with Guest Networks created.
- Fixed issue where email would fail to send if --insecure flag was removed from amtm configuration.
- When running WAN Failover from the Console, the script will actively display the current Packet Loss. 0% will be displayed in Green, 100% will be displayed in Red, and 1% - 99% will be displayed in Yellow.
- Added email timeout option, adjusted in configuration using EMAILTIMEOUT setting.
- Moved ping process into seperate function and called by the failover monitors.