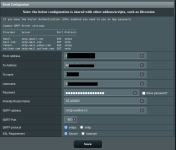
Do you have more logs to work with for this? I’m not sure what is going on here, I need more data.
wan-failover.sh - Monitor Mode
Jul 1 17:33:00 router wan-failover.sh: WAN Status - Adding default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:33:00 router wan-failover.sh: WAN Status - Added default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:33:00 router wan-failover.sh: WAN Status - Adding IP Rule for 119.29.29.29
Jul 1 17:33:00 router wan-failover.sh: WAN Status - Added IP Rule for 119.29.29.29
Jul 1 17:33:04 router wan-failover.sh: WAN Status - wan0 has 0% packet loss
Jul 1 17:33:04 router wan-failover.sh: WAN Status - wan1 enabled
Jul 1 17:33:04 router wan-failover.sh: WAN Status - Adding default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:33:04 router wan-failover.sh: WAN Status - Added default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:33:04 router wan-failover.sh: WAN Status - Adding IP Rule for 119.28.28.28
Jul 1 17:33:04 router wan-failover.sh: WAN Status - Added IP Rule for 119.28.28.28
Jul 1 17:33:08 router wan-failover.sh: WAN Status - wan1 has 0% packet loss
Jul 1 17:33:08 router wan-failover.sh: WAN0 Active - Verifying WAN0
Jul 1 17:33:08 router wan-failover.sh: WAN0 Failover Monitor - Monitoring wan0 via 119.29.29.29 for Failure
Jul 1 17:35:03 router wan-failover.sh: WAN0 Failover Monitor - Packet Loss Detected - WAN0 Packet Loss: 20%
Jul 1 17:35:08 router wan-failover.sh: WAN0 Failover Monitor - Failure Detected - WAN0 Packet Loss: 100%
Jul 1 17:35:08 router wan-failover.sh: WAN Switch - Switching wan1 to Primary WAN
Jul 1 17:35:09 router wan-failover.sh: WAN Switch - WAN IP Address: 192.168.199.100
Jul 1 17:35:09 router wan-failover.sh: WAN Switch - WAN Gateway: 192.168.199.1
Jul 1 17:35:09 router wan-failover.sh: WAN Switch - WAN Interface: eth2
Jul 1 17:35:09 router wan-failover.sh: WAN Switch - WAN Interface: eth2
Jul 1 17:35:09 router wan-failover.sh: WAN Switch - DNS1 Server: 8.8.8.8
Jul 1 17:36:00 router wan-failover.sh: WAN Status - wan0 enabled
Jul 1 17:36:00 router wan-failover.sh: WAN Status - Restarting WAN0: eth0
Jul 1 17:37:36 router wan-failover.sh: WAN Status - Restarted WAN0: eth0
Jul 1 17:38:00 router wan-failover.sh: WAN Status - wan0 enabled
Jul 1 17:38:00 router wan-failover.sh: WAN Status - Adding default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:38:00 router wan-failover.sh: WAN Status - Added default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:38:00 router wan-failover.sh: WAN Status - Adding IP Rule for 119.29.29.29
Jul 1 17:38:00 router wan-failover.sh: WAN Status - Added IP Rule for 119.29.29.29
Jul 1 17:38:04 router wan-failover.sh: WAN Status - wan0 has 0% packet loss
Jul 1 17:38:04 router wan-failover.sh: WAN Status - wan1 enabled
Jul 1 17:38:04 router wan-failover.sh: WAN Status - Adding default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:38:04 router wan-failover.sh: WAN Status - Added default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:38:04 router wan-failover.sh: WAN Status - Adding IP Rule for 119.28.28.28
Jul 1 17:38:04 router wan-failover.sh: WAN Status - Added IP Rule for 119.28.28.28
Jul 1 17:38:08 router wan-failover.sh: WAN Status - wan1 has 0% packet loss
Jul 1 17:38:08 router wan-failover.sh: WAN0 Active - Verifying WAN0
Jul 1 17:38:08 router wan-failover.sh: WAN Switch - Switching wan0 to Primary WAN
Jul 1 17:38:08 router wan-failover.sh: WAN Switch - WAN IP Address: 178.249.55.33
Jul 1 17:38:08 router wan-failover.sh: WAN Switch - WAN Gateway: 178.249.55.254
Jul 1 17:38:08 router wan-failover.sh: WAN Switch - WAN Interface: eth0
Jul 1 17:38:08 router wan-failover.sh: WAN Switch - WAN Interface: eth0
Jul 1 17:38:08 router wan-failover.sh: WAN Switch - DNS1 Server: 8.8.8.8
Jul 1 17:39:00 router wan-failover.sh: WAN Status - wan0 enabled
Jul 1 17:39:00 router wan-failover.sh: WAN Status - Adding default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:39:00 router wan-failover.sh: WAN Status - Added default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:39:00 router wan-failover.sh: WAN Status - Adding IP Rule for 119.29.29.29
Jul 1 17:39:00 router wan-failover.sh: WAN Status - Added IP Rule for 119.29.29.29
Jul 1 17:39:04 router wan-failover.sh: WAN Status - wan0 has 0% packet loss
Jul 1 17:39:04 router wan-failover.sh: WAN Status - wan1 enabled
Jul 1 17:39:04 router wan-failover.sh: WAN Status - Adding default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:39:04 router wan-failover.sh: WAN Status - Added default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:39:04 router wan-failover.sh: WAN Status - Adding IP Rule for 119.28.28.28
Jul 1 17:39:04 router wan-failover.sh: WAN Status - Added IP Rule for 119.28.28.28
Jul 1 17:39:09 router wan-failover.sh: WAN Status - wan1 has 20% packet loss
Jul 1 17:39:09 router wan-failover.sh: WAN0 Active - Verifying WAN0
Jul 1 17:39:09 router wan-failover.sh: WAN Switch - Switching wan0 to Primary WAN
Jul 1 17:39:09 router wan-failover.sh: WAN Switch - DNS1 Server: 8.8.8.8
Jul 1 17:40:00 router wan-failover.sh: WAN Status - wan0 enabled
Jul 1 17:40:00 router wan-failover.sh: WAN Status - Adding default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:40:00 router wan-failover.sh: WAN Status - Added default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:40:00 router wan-failover.sh: WAN Status - Adding IP Rule for 119.29.29.29
Jul 1 17:40:00 router wan-failover.sh: WAN Status - Added IP Rule for 119.29.29.29
Jul 1 17:40:04 router wan-failover.sh: WAN Status - wan0 has 0% packet loss
Jul 1 17:40:04 router wan-failover.sh: WAN Status - wan1 enabled
Jul 1 17:40:04 router wan-failover.sh: WAN Status - Adding default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:40:04 router wan-failover.sh: WAN Status - Added default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:40:04 router wan-failover.sh: WAN Status - Adding IP Rule for 119.28.28.28
Jul 1 17:40:04 router wan-failover.sh: WAN Status - Added IP Rule for 119.28.28.28
Jul 1 17:40:08 router wan-failover.sh: WAN Status - wan1 has 0% packet loss
Jul 1 17:40:09 router wan-failover.sh: WAN0 Active - Verifying WAN0
Jul 1 17:40:09 router wan-failover.sh: WAN Switch - Switching wan0 to Primary WAN
Jul 1 17:40:09 router wan-failover.sh: WAN Switch - DNS1 Server: 8.8.8.8
Jul 1 17:41:00 router wan-failover.sh: WAN Status - wan0 enabled
Jul 1 17:41:00 router wan-failover.sh: WAN Status - Adding default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:41:00 router wan-failover.sh: WAN Status - Added default route for wan0 Routing Table via 178.249.55.254 dev eth0
Jul 1 17:41:00 router wan-failover.sh: WAN Status - Adding IP Rule for 119.29.29.29
Jul 1 17:41:00 router wan-failover.sh: WAN Status - Added IP Rule for 119.29.29.29
Jul 1 17:41:04 router wan-failover.sh: WAN Status - wan0 has 0% packet loss
Jul 1 17:41:04 router wan-failover.sh: WAN Status - wan1 enabled
Jul 1 17:41:04 router wan-failover.sh: WAN Status - Adding default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:41:04 router wan-failover.sh: WAN Status - Added default route for wan1 Routing Table via 192.168.199.1 dev eth2
Jul 1 17:41:04 router wan-failover.sh: WAN Status - Adding IP Rule for 119.28.28.28
Jul 1 17:41:04 router wan-failover.sh: WAN Status - Added IP Rule for 119.28.28.28
Jul 1 17:41:08 router wan-failover.sh: WAN Status - wan1 has 0% packet loss
Jul 1 17:41:08 router wan-failover.sh: WAN0 Active - Verifying WAN0
Jul 1 17:41:08 router wan-failover.sh: WAN Switch - Switching wan0 to Primary WAN
Jul 1 17:41:09 router wan-failover.sh: WAN Switch - DNS1 Server: 8.8.8.8