Could someone share a guide how to port forward / getting connectable using WireGuard? I opened port on VPN provider with OpenVPN and it worked (using iptables) but with WireGuard i never got it working (despite opening a dedicated WireGuard port). Anyone have a guide? Been searching internet without any luck. If i install vpn providers WireGuard client it works, but i want to run it on Asus merlin firmware. Thanks in advance
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Guide Wireguard-portforwarding
- Thread starter Sweden
- Start date
It doesn't work AFAIK, and I've tried everything. If you are running your entire network through the WireGuard tunnel, you can still install VPN providers client and open a port on a device where it is needed and it will work... And yes, this will mean that traffic will go through two WireGuard tunnels, one set up on your router and second one, connected via VPN provider client on a selected device. I haven't noticed any issues whatsoever and no slowdowns with that configuration so far. The best way would be of course to open a port directly on the router side, without the need of installing the VPN providers client, but I don't think this is currently possible...
It doesn't work AFAIK, and I've tried everything. If you are running your entire network through the WireGuard tunnel, you can still install VPN providers client and open a port on a device where it is needed and it will work... And yes, this will mean that traffic will go through two WireGuard tunnels, one set up on your router and second one, connected via VPN provider client on a selected device. I haven't noticed any issues whatsoever and no slowdowns with that configuration so far. The best way would be of course to open a port directly on the router side, without the need of installing the VPN providers client, but I don't think this is currently possible...
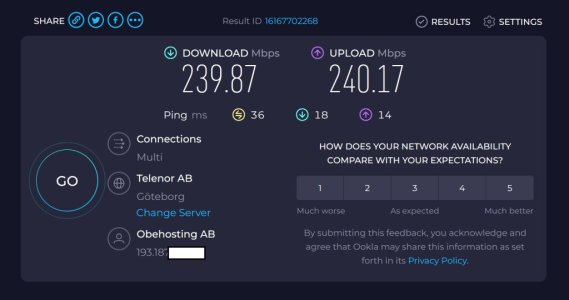
OK. Thank you for getting back on this topic. I lost my hair yesterday. With regular VPN on ASUS AX88U i can achive speeds of 100/50 Mbps when doing speedtests while i can easily do 250/250 Mbps when using the built-in wireguard client in router. I hope someone finds out a fix for this, until then i need to run a client.
juanantonio
Regular Contributor
Hi.
You don't provide any info about your clients or software you are using to connect to your Wireguard provider.
I'm using Wireguard Session Manager, which runs under Entware in a USB stick, with zero issues, including those of opening/forwarding ports.
Here are some hints, if you are interested:
https://github.com/ZebMcKayhan/WireguardManager
https://github.com/MartineauUK/wireguard
Regards.
You don't provide any info about your clients or software you are using to connect to your Wireguard provider.
I'm using Wireguard Session Manager, which runs under Entware in a USB stick, with zero issues, including those of opening/forwarding ports.
Here are some hints, if you are interested:
https://github.com/ZebMcKayhan/WireguardManager
https://github.com/MartineauUK/wireguard
Regards.
ZebMcKayhan
Very Senior Member
Port forwarding from Wireguard is not supported by firmware. You will need to add the rules manually, via ssh.Could someone share a guide how to port forward / getting connectable using WireGuard? I opened port on VPN provider with OpenVPN and it worked (using iptables) but with WireGuard i never got it working (despite opening a dedicated WireGuard port). Anyone have a guide? Been searching internet without any luck. If i install vpn providers WireGuard client it works, but i want to run it on Asus merlin firmware. Thanks in advance
However, this is not going to be easy unless your target computer/server is not using said vpn connection for internet. So, set this up in VpnDirector first.
A firewall rule to perform port redirect, port 8080 from wgc1 to 192.168.1.100 would be:
Code:
iptables -t nat -I PREROUTING -i wgc1 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:8080Another rule is needed to let our forwarded port create new inbound connections through the firewall:
Code:
iptables -I FORWARD -i wgc1 -p tcp -d 192.168.1.100 --dport 8080 -m state --state NEW -j ACCEPTNaturally these rules won't persist through reboots unless added to firewall-start script.
Port forwarding from Wireguard is not supported by firmware. You will need to add the rules manually, via ssh.
However, this is not going to be easy unless your target computer/server is not using said vpn connection for internet. So, set this up in VpnDirector first.
A firewall rule to perform port redirect, port 8080 from wgc1 to 192.168.1.100 would be:
Note that this rule is only valid for tcp, another rule is needed for udp.Code:iptables -t nat -I PREROUTING -i wgc1 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:8080
Another rule is needed to let our forwarded port create new inbound connections through the firewall:
Code:iptables -I FORWARD -i wgc1 -p tcp -d 192.168.1.100 --dport 8080 -m state --state NEW -j ACCEPT
Naturally these rules won't persist through reboots unless added to firewall-start script.
I will test this and see if its working, i think i only did the prerouting and not forward rule. If thats the case your the best!
Running the pc version of wireguard client gives around 240Mbps (on a 250Mbps connection). Lets see if RT-AX88 can give the same speeds, the CPU seemed pretty busy, but i think 500 Mbps on router should be possible (my guess). Maybe time to upgrade connection while i am playing around... thx again
Attachments
Last edited:
ZebMcKayhan
Very Senior Member
Technically the nat PREROUTING rule should go into nat-start and the FORWARD filter rule should go into firewall-start.I will test this and see if its working, i think i only did the prerouting and not forward rule. If thats the case your the best!
Running the pc version of wireguard client gives around 240Mbps (on a 250Mbps connection). Lets see if RT-AX88 can give the same speeds, the CPU seemed pretty busy, but i think 500 Mbps on router should be possible (my guess). Maybe time to upgrade connection while i am playing around... thx again
Some day when I have the time and energy I'll write something that would automate custom wireguard firewall rules... I'll have a post here somewhere I'll need to find. I'll post it here when I find it.
Edit: here it is: https://www.snbforums.com/threads/w...t-rules-after-router-reboot.87768/post-878099 But it's "not official" as pointed out, but it works... for now... altough example is only for nat rules.
It would be nice to do the same as fw does it but with custom files instead, possibly in /tmp/ ram so it would fw future proof...
Perhaps more convenient for you to just use firewall-start and nat-start to put your rules in and delete any duplicate rules before to prevent duplicates.
Like:
firewall-start:
Code:
#!/bin/sh
iptables -D FORWARD -i wgc1 -p tcp -d 192.168.1.100 --dport 8080 -m state --state NEW -j ACCEPT 2>/dev/null
iptables -I FORWARD -i wgc1 -p tcp -d 192.168.1.100 --dport 8080 -m state --state NEW -j ACCEPTnat-start:
Code:
#!/bin/sh
iptables -t nat -D PREROUTING -i wgc1 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:8080 2>/dev/null
iptables -t nat -I PREROUTING -i wgc1 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:8080-p udp instead of -p tcp if you need udp packets to be forwarded as well.
Last edited:
Port forwarding from Wireguard is not supported by firmware. You will need to add the rules manually, via ssh.
However, this is not going to be easy unless your target computer/server is not using said vpn connection for internet. So, set this up in VpnDirector first.
A firewall rule to perform port redirect, port 8080 from wgc1 to 192.168.1.100 would be:
Note that this rule is only valid for tcp, another rule is needed for udp.Code:iptables -t nat -I PREROUTING -i wgc1 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:8080
Another rule is needed to let our forwarded port create new inbound connections through the firewall:
Code:iptables -I FORWARD -i wgc1 -p tcp -d 192.168.1.100 --dport 8080 -m state --state NEW -j ACCEPT
Naturally these rules won't persist through reboots unless added to firewall-start script.
This is not working.... I tried:
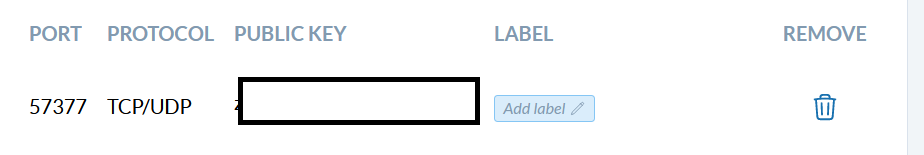
iptables -t nat -I PREROUTING -i wgc1 -p tcp --dport 57377 -j DNAT --to-destination 192.168.0.2:57377
iptables -I FORWARD -i wgc1 -p tcp -d 192.168.0.2 --dport 57377 -m state --state NEW -j ACCEPT
iptables -t nat -I PREROUTING -i wgc1 -p udp --dport 57377 -j DNAT --to-destination 192.168.0.2:57377
iptables -I FORWARD -i wgc1 -p udp -d 192.168.0.2 --dport 57377 -m state --state NEW -j ACCEPT
Port forwarding from Wireguard is not supported by firmware. You will need to add the rules manually, via ssh.
However, this is not going to be easy unless your target computer/server is not using said vpn connection for internet. So, set this up in VpnDirector first.
A firewall rule to perform port redirect, port 8080 from wgc1 to 192.168.1.100 would be:
Note that this rule is only valid for tcp, another rule is needed for udp.Code:iptables -t nat -I PREROUTING -i wgc1 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:8080
Another rule is needed to let our forwarded port create new inbound connections through the firewall:
Code:iptables -I FORWARD -i wgc1 -p tcp -d 192.168.1.100 --dport 8080 -m state --state NEW -j ACCEPT
Naturally these rules won't persist through reboots unless added to firewall-start script.
I tried the following below also in SSH. Port is still closed when i am trying to get connectable.
iptables -t nat -I PREROUTING -i wgc1 -p tcp --dport 57377 -j DNAT --to-destination 192.168.0.2:57377
iptables -I FORWARD -i wgc1 -p tcp -d 192.168.0.2 --dport 57377 -m state --state NEW -j ACCEPT
Also tried:Technically the nat PREROUTING rule should go into nat-start and the FORWARD filter rule should go into firewall-start.
Some day when I have the time and energy I'll write something that would automate custom wireguard firewall rules... I'll have a post here somewhere I'll need to find. I'll post it here when I find it.
Edit: here it is: https://www.snbforums.com/threads/w...t-rules-after-router-reboot.87768/post-878099 But it's "not official" as pointed out, but it works... for now... altough example is only for nat rules.
It would be nice to do the same as fw does it but with custom files instead, possibly in /tmp/ ram so it would fw future proof...
Perhaps more convenient for you to just use firewall-start and nat-start to put your rules in and delete any duplicate rules before to prevent duplicates.
Like:
firewall-start:
Code:#!/bin/sh iptables -D FORWARD -i wgc1 -p tcp -d 192.168.1.100 --dport 8080 -m state --state NEW -j ACCEPT 2>/dev/null iptables -I FORWARD -i wgc1 -p tcp -d 192.168.1.100 --dport 8080 -m state --state NEW -j ACCEPT
nat-start:
duplicate the rules and change toCode:#!/bin/sh iptables -t nat -D PREROUTING -i wgc1 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:8080 2>/dev/null iptables -t nat -I PREROUTING -i wgc1 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:8080-p udpinstead of-p tcpif you need udp packets to be forwarded as well.
iptables -D FORWARD -i wgc1 -p tcp -d 192.168.0.2 --dport 57377 -m state --state NEW -j ACCEPT 2>/dev/null
iptables -I FORWARD -i wgc1 -p tcp -d 192.168.0.2 --dport 57377 -m state --state NEW -j ACCEPT
iptables -t nat -D PREROUTING -i wgc1 -p tcp --dport 57377 -j DNAT --to-destination 192.168.0.2:57377 2>/dev/null
iptables -t nat -I PREROUTING -i wgc1 -p tcp --dport 57377 -j DNAT --to-destination 192.168.0.2:57377
iptables -D FORWARD -i wgc1 -p udp -d 192.168.0.2 --dport 57377 -m state --state NEW -j ACCEPT 2>/dev/null
iptables -I FORWARD -i wgc1 -p udp -d 192.168.0.2 --dport 57377 -m state --state NEW -j ACCEPT
iptables -t nat -D PREROUTING -i wgc1 -p udp --dport 57377 -j DNAT --to-destination 192.168.0.2:57377 2>/dev/null
iptables -t nat -I PREROUTING -i wgc1 -p udp --dport 57377 -j DNAT --to-destination 192.168.0.2:57377
No luck whatever to get connectable. I have open port at VPN provider / restarted connection and wireguard is running.
Still not connectable via torrent for example (works fine with OVPN wireguard client, but not on asus router
Attachments
ZebMcKayhan
Very Senior Member
Did you setup 192.168.0.2 to use wgc1 in VpnDirector?This is not working....
ZebMcKayhan
Very Senior Member
If its still not working altough VPNDirector is set correct, there is the off chance you have this issue: https://www.snbforums.com/threads/port-forwarding-over-wireguard-connection.87498/post-873447I tried the following below also in SSH. Port is still closed when i am trying to get connectable.
I did a 192.168.0.1/24 (all lan traffic in vpn director), as i want all traffic to go through vpn/router. That dident help, i could see traffic was flowing through vpn, but never got connectable. When i switched to client, to use same port it worked direcly almost.Did you setup 192.168.0.2 to use wgc1 in VpnDirector?
ZebMcKayhan
Very Senior Member
What if you try this, after you started your wgc1 client with your vpndirector route, try to execute this at the ssh prompt:I did a 192.168.0.1/24 (all lan traffic in vpn director), as i want all traffic to go through vpn/router. That dident help, i could see traffic was flowing through vpn, but never got connectable. When i switched to client, to use same port it worked direcly almost.
Code:
ip route del $(ip route show table wgc1 | grep $(wg show wgc1 endpoints | sed -n 's/.*\t\(.*\):.*/\1/p')) table wgc1Then try to add iptables rules for port forward.
Note that 192.168.0.2 should not be using any local vpn client when testing this.
Hey guys, I'm trying to achieve something similar (I think) so I guess I can piggyback on this thread?
I'm running a RT-AX56U with 3004.388.8_2
I have an individual wireguard connection which is used solely for tunneling a Transmission client running on the router (installed via Entware). It's mapped up in the VPN director area and it works. Traffic is sent and received.
The only problem is that Transmission can't see it's listening port as being open ("port is CLOSED"), and as I result I get some errors and I assume it's not working as well as it otherwise should be as a result.
I saw Merlin said here that you need to configure it manually and that the VPN also needs to support it. My VPN (proton) does support it however it assigns a random port for forwarding on each connection and AFAIK you can only retreive it by using their application on a computer. Perhaps there is some crazy way to scan the ports on that connection, I don't know.
Anyway, is there not some way to achieve this otherwise? Don't I just want a simple routing rule that says, any traffic that comes down this VPN connection, force it to Transmission on the port that it's listening on - and it would work?
If someone can help me with the command to run that would be much appreciated.
thing - interface - ip
Transmission - br0:0 - 192.168.1.10 (client is listening on 51413)
Wireguard - wgc5 - 10.2.0.2
Note - firewall-start script already has port 51413 allowed
iptables -I INPUT -p tcp --destination-port 51413 -j ACCEPT
iptables -I INPUT -p udp --destination-port 51413 -j ACCEPT
I'm running a RT-AX56U with 3004.388.8_2
I have an individual wireguard connection which is used solely for tunneling a Transmission client running on the router (installed via Entware). It's mapped up in the VPN director area and it works. Traffic is sent and received.
The only problem is that Transmission can't see it's listening port as being open ("port is CLOSED"), and as I result I get some errors and I assume it's not working as well as it otherwise should be as a result.
I saw Merlin said here that you need to configure it manually and that the VPN also needs to support it. My VPN (proton) does support it however it assigns a random port for forwarding on each connection and AFAIK you can only retreive it by using their application on a computer. Perhaps there is some crazy way to scan the ports on that connection, I don't know.
Anyway, is there not some way to achieve this otherwise? Don't I just want a simple routing rule that says, any traffic that comes down this VPN connection, force it to Transmission on the port that it's listening on - and it would work?
If someone can help me with the command to run that would be much appreciated.
thing - interface - ip
Transmission - br0:0 - 192.168.1.10 (client is listening on 51413)
Wireguard - wgc5 - 10.2.0.2
Note - firewall-start script already has port 51413 allowed
iptables -I INPUT -p tcp --destination-port 51413 -j ACCEPT
iptables -I INPUT -p udp --destination-port 51413 -j ACCEPT
ZebMcKayhan
Very Senior Member
one issue (and there could be many more) is that whatever port-forwarded from VPN is TO your WG interface address. This is indeed an address local to the router, but it is not the address you set the transmission to use. as the initial request is TO one address and the reply will be FROM a different address you will run into issues (typically with rp_filter that will block it).Anyway, is there not some way to achieve this otherwise? Don't I just want a simple routing rule that says, any traffic that comes down this VPN connection, force it to Transmission on the port that it's listening on - and it would work?
either you DNAT in PREROUTING to your alias 192.168.1.10, i.e
Code:
iptables -t nat -I PREROUTING -i wgc5 -p tcp --dport 51413 -j DNAT --to-destination 192.168.1.10
iptables -t nat -I PREROUTING -i wgc5 -p udp --dport 51413 -j DNAT --to-destination 192.168.1.10or you bind transmission to wg interface ip 10.2.0.2 and setup a rule in vpn director: Local IP: 10.2.0.2 to wgc5.
regarding automatically retrieving the port to use, I have a vague memory of seeing someone do this, perhaps even for proton VPN, it should be in a post here somewhere.
Similar threads
- Replies
- 4
- Views
- 3K
- Replies
- 18
- Views
- 2K
- Replies
- 2
- Views
- 373
- Replies
- 14
- Views
- 1K
Similar threads
Similar threads
-
Is there a guide to setting up multiple DDNS records?
- Started by GuardYaGrill
- Replies: 3
-
-
Solved guide me on which merlin 3006.102.4 router should i buy - if...
- Started by consorts
- Replies: 37
-
-
-
Setting up a Wireguard Server to access Plex away from home
- Started by Bitrudeuk
- Replies: 0
-
Cannot access lan on AX-86U through Hub and Spoke wireguard
- Started by Asus79
- Replies: 18
-
WireGuard no longer auto reconnects upon server IP address change
- Started by melodies-2
- Replies: 0
-
ProtonVPN Wireguard connecting but no change to external IP
- Started by lcalamar
- Replies: 28
-
Latest threads
-
-
-
-
-
what is currently broken on asus BE routers?
- Started by conflictednetworks
- Replies: 13
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!