torstein
Senior Member
TLDR:
Like the title says, VPN Director on Merlin 386.3_2 configured with Mullvad VPN is forcing all computers on my network to use Mullvad DNS servers, and not just the one Mac I have tunneled through Mullvad VPN. I hope you can help
THIS IS WHAT I'M TRYING TO DO:
I want my Asus AX86U to only tunnel my Mac mini through Mullvad VPN. The rest of my computers I don't want to go through Mullvad VPN. I followed this guide https://mullvad.net/it/help/asus-merlin-and-mullvad-vpn/ and it works perfectly - that is, only my Mac mini is tunneled through Mullvad VPN. All my other devices are not going through Mullvad VPN, as I hoped for, but my other Macs are now using Mullvads DNS-servers
How can I make my Asus AX86U router with Mullvad VPN through VPN Director use Mullvads DNS servers only on the Mac mini, and leave the DNS alone on all my other computers on the network?
I tried adding this
to the end of the custom configuration text field under VPN --> VPN Client on the router, but it didn't work. It just caused DNS leaks as well, and I'm not really sure it actually did anything.
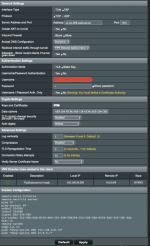
This is what the entire "Custom config" looks like:
Any other ideas?
Like the title says, VPN Director on Merlin 386.3_2 configured with Mullvad VPN is forcing all computers on my network to use Mullvad DNS servers, and not just the one Mac I have tunneled through Mullvad VPN. I hope you can help
THIS IS WHAT I'M TRYING TO DO:
I want my Asus AX86U to only tunnel my Mac mini through Mullvad VPN. The rest of my computers I don't want to go through Mullvad VPN. I followed this guide https://mullvad.net/it/help/asus-merlin-and-mullvad-vpn/ and it works perfectly - that is, only my Mac mini is tunneled through Mullvad VPN. All my other devices are not going through Mullvad VPN, as I hoped for, but my other Macs are now using Mullvads DNS-servers
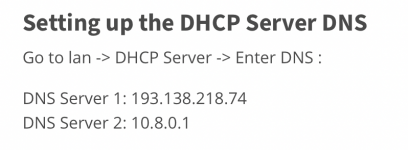
10.8.0.1 and 193.138.218.74. This is fair, because the guide did specify to add the Mullvad DNS-servers under DHCP-settings on the AX86U (I assume this is to prevent DNS leaks). However, I don't want my other computers on the home network to use Mullvads DNS servers, I want to use the default DNS-servers of the router, which in my case is NextDNS. If I remove the Mullvad DNS servers, then my real IP leaks, as one would expect.How can I make my Asus AX86U router with Mullvad VPN through VPN Director use Mullvads DNS servers only on the Mac mini, and leave the DNS alone on all my other computers on the network?
I tried adding this
Code:
push "dhcp-option DNS 193.138.218.74"
push "dhcp-option DNS 10.8.0.1"This is what the entire "Custom config" looks like:
Code:
resolv-retry infinite
remote-cert-tls server
ping 10
ping-restart 60
sndbuf 524288
rcvbuf 524288
cipher AES-256-CBC
tls-cipher TLS-DHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA
fast-io
remote-random
comp-lzo no
push "dhcp-option DNS 193.138.218.74"
push "dhcp-option DNS 10.8.0.1"Any other ideas?
Last edited: