postoronnim-v
Occasional Visitor
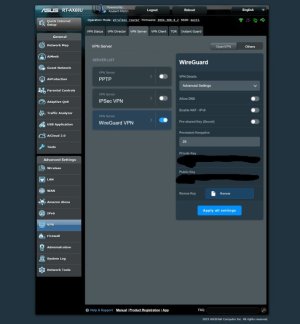
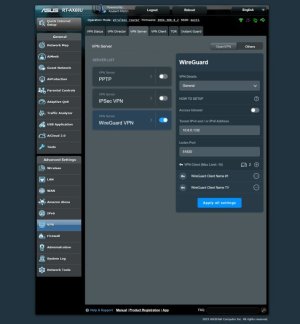
I have set up a WireGuard VPN server. Now the client has access to the LAN when connected to the server. How can I block access to the LAN, leaving only Internet access? Access Intranet is disabled in the server settings.