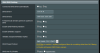
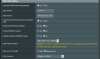
Thought I had this figured out in 384.11 but the changes I see in the change log for .12 and 13 and the discussion board have my head spinning.
Could someone be so kind as to please itemize the changes needed to the settings in 384.13 so that DNS-over-TLS is enabled properly in 384.13. Assume we are starting from scratch with the router just having been freshly factory reset. I was going to use cloudflare preset.
Many thanks.
Edward
Could someone be so kind as to please itemize the changes needed to the settings in 384.13 so that DNS-over-TLS is enabled properly in 384.13. Assume we are starting from scratch with the router just having been freshly factory reset. I was going to use cloudflare preset.
Many thanks.
Edward