Xentrk
Part of the Furniture
These references should answer your questions:Sorry if this has been answered before but I have been researching for some time now without finding an answer that I can understand
I have an Asus RT-AC68U set up behind an Asus DSL-AC68U to use for VPN and I have the latest (384.6) Merlin firmware installed on it.
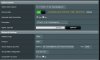
When I configure an OpenVPN client and get to the bottom of the config there is an option "redirect Internet traffic" which most setup guides advise to set to "No"
I do not understand this setting at all as I would have thought that this is the whole point of a VPN???
Don't I want all my devices (phone, iPad, Desktop PC) connecting to the Router to connect to the internet through the VPN tunnel that is created?
Other options are "All" and "Policy Rules (Strict)"
I've been variously setting it to either "All" or "Policy Rules Strict" and then defining the whole network to go through it (10.4.4.0/27 in my case)
Why would the guides be saying to set it to "No" ???
Thank-you for any advice given.
https://github.com/RMerl/asuswrt-merlin/wiki/Policy-based-routing
https://x3mtek.com/torguard-openvpn-2-4-client-setup-for-asuswrt-merlin-firmware/
If you still have questions after reading the links, let me know and I'll try to help.