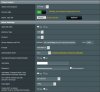
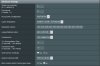
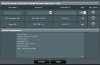
Recently moved from the stock ASUS firmware on my RT-AC68U to Merlin 380. goal is to exclude my Roku from my PIA VPN connection for NetFlix.
Anyway, can't get it working. Always ends w/ "Authenticate/Decrypt packet error: cipher final failed"
I'm using the following Certificat Authority (downloaded today)
-----BEGIN CERTIFICATE-----
MIIFqzCCBJOgAwIBAgIJAKZ7D5Yv87qDMA0GCSqGSIb3DQEBDQUAMIHoMQswCQYD
VQQGEwJVUzELMAkGA1UECBMCQ0ExEzARBgNVBAcTCkxvc0FuZ2VsZXMxIDAeBgNV
BAoTF1ByaXZhdGUgSW50ZXJuZXQgQWNjZXNzMSAwHgYDVQQLExdQcml2YXRlIElu
dGVybmV0IEFjY2VzczEgMB4GA1UEAxMXUHJpdmF0ZSBJbnRlcm5ldCBBY2Nlc3Mx
IDAeBgNVBCkTF1ByaXZhdGUgSW50ZXJuZXQgQWNjZXNzMS8wLQYJKoZIhvcNAQkB
FiBzZWN1cmVAcHJpdmF0ZWludGVybmV0YWNjZXNzLmNvbTAeFw0xNDA0MTcxNzM1
MThaFw0zNDA0MTIxNzM1MThaMIHoMQswCQYDVQQGEwJVUzELMAkGA1UECBMCQ0Ex
EzARBgNVBAcTCkxvc0FuZ2VsZXMxIDAeBgNVBAoTF1ByaXZhdGUgSW50ZXJuZXQg
QWNjZXNzMSAwHgYDVQQLExdQcml2YXRlIEludGVybmV0IEFjY2VzczEgMB4GA1UE
AxMXUHJpdmF0ZSBJbnRlcm5ldCBBY2Nlc3MxIDAeBgNVBCkTF1ByaXZhdGUgSW50
ZXJuZXQgQWNjZXNzMS8wLQYJKoZIhvcNAQkBFiBzZWN1cmVAcHJpdmF0ZWludGVy
bmV0YWNjZXNzLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAPXD
L1L9tX6DGf36liA7UBTy5I869z0UVo3lImfOs/GSiFKPtInlesP65577nd7UNzzX
lH/P/CnFPdBWlLp5ze3HRBCc/Avgr5CdMRkEsySL5GHBZsx6w2cayQ2EcRhVTwWp
cdldeNO+pPr9rIgPrtXqT4SWViTQRBeGM8CDxAyTopTsobjSiYZCF9Ta1gunl0G/
8Vfp+SXfYCC+ZzWvP+L1pFhPRqzQQ8k+wMZIovObK1s+nlwPaLyayzw9a8sUnvWB
/5rGPdIYnQWPgoNlLN9HpSmsAcw2z8DXI9pIxbr74cb3/HSfuYGOLkRqrOk6h4RC
OfuWoTrZup1uEOn+fw8CAwEAAaOCAVQwggFQMB0GA1UdDgQWBBQv63nQ/pJAt5tL
y8VJcbHe22ZOsjCCAR8GA1UdIwSCARYwggESgBQv63nQ/pJAt5tLy8VJcbHe22ZO
sqGB7qSB6zCB6DELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAkNBMRMwEQYDVQQHEwpM
b3NBbmdlbGVzMSAwHgYDVQQKExdQcml2YXRlIEludGVybmV0IEFjY2VzczEgMB4G
A1UECxMXUHJpdmF0ZSBJbnRlcm5ldCBBY2Nlc3MxIDAeBgNVBAMTF1ByaXZhdGUg
SW50ZXJuZXQgQWNjZXNzMSAwHgYDVQQpExdQcml2YXRlIEludGVybmV0IEFjY2Vz
czEvMC0GCSqGSIb3DQEJARYgc2VjdXJlQHByaXZhdGVpbnRlcm5ldGFjY2Vzcy5j
b22CCQCmew+WL/O6gzAMBgNVHRMEBTADAQH/MA0GCSqGSIb3DQEBDQUAA4IBAQAn
a5PgrtxfwTumD4+3/SYvwoD66cB8IcK//h1mCzAduU8KgUXocLx7QgJWo9lnZ8xU
ryXvWab2usg4fqk7FPi00bED4f4qVQFVfGfPZIH9QQ7/48bPM9RyfzImZWUCenK3
7pdw4Bvgoys2rHLHbGen7f28knT2j/cbMxd78tQc20TIObGjo8+ISTRclSTRBtyC
GohseKYpTS9himFERpUgNtefvYHbn70mIOzfOJFTVqfrptf9jXa9N8Mpy3ayfodz
1wiqdteqFXkTYoSDctgKMiZ6GdocK9nMroQipIQtpnwd4yBDWIyC6Bvlkrq5TQUt
YDQ8z9v+DMO6iwyIDRiU
-----END CERTIFICATE-----
LOG
Apr 20 21:28:57 rc_service: httpd 443:notify_rc start_vpnclient5
Apr 20 21:29:00 openvpn[4902]: OpenVPN 2.4.0 arm-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Mar 29 2017
Apr 20 21:29:00 openvpn[4902]: library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.08
Apr 20 21:29:00 openvpn[4903]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Apr 20 21:29:00 openvpn[4903]: TCP/UDP: Preserving recently used remote address: [AF_INET]107.182.231.37:1198
Apr 20 21:29:00 openvpn[4903]: UDP link local: (not bound)
Apr 20 21:29:00 openvpn[4903]: UDP link remote: [AF_INET]107.182.231.37:1198
Apr 20 21:29:01 openvpn[4903]: [84863bf223b3b6ebfc008dc8a2b4c49e] Peer Connection Initiated with [AF_INET]107.182.231.37:1198
Apr 20 21:29:02 openvpn[4903]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 20 21:29:02 openvpn[4903]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 20 21:29:02 openvpn[4903]: WARNING: cipher with small block size in use, reducing reneg-bytes to 64MB to mitigate SWEET32 attacks.
Apr 20 21:29:02 openvpn[4903]: TUN/TAP device tun15 opened
Apr 20 21:29:02 openvpn[4903]: do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Apr 20 21:29:02 openvpn[4903]: /usr/sbin/ip link set dev tun15 up mtu 1500
Apr 20 21:29:02 openvpn[4903]: /usr/sbin/ip addr add dev tun15 local 10.49.10.6 peer 10.49.10.5
Apr 20 21:29:02 openvpn[4903]: updown.sh tun15 1500 1545 10.49.10.6 10.49.10.5 init
Apr 20 21:29:03 rc_service: service 4962:notify_rc updateresolv
Apr 20 21:29:05 openvpn-routing: Skipping, client 5 not in routing policy mode
Apr 20 21:29:05 openvpn[4903]: Initialization Sequence Completed
Apr 20 21:29:12 openvpn[4903]: Authenticate/Decrypt packet error: cipher final failed