In this new version 380.68 there are no new features for VPN server.
This guide will show you how to setup a VPN server with your Asus routers
This works with native ASUS firmware or Merlin Firmware
*** I suggest that every time you update to a new firmware do a Default on OpenVPN server then reboot the router and enter the data again. Also export a new .ovpn file and import to your device in order to have smooth results. Otherwise you may get into issues where you cannot see windows shared folders.
With the ASUS router you can have up to 2 separate VPN servers.
In this example I am using VPN server 1
simply enable OpenVPN server and by default the admin username and password is in the list. You can create up to 32 username and passwords in the appropriate fields.
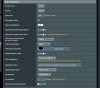
In VPN details click on the advanced menu.
Use the VPN advanced image below and setup the values accordingly.
View attachment 6788
View attachment 9498
***Important***
With the latest firmware 380.66.4 and up You need to enable Respond to DNS and Enable Advertise DNS to clients otherwise you will not be able to connect to your Local Network. This was not the case in the past.
Finally in order for file shares to work properly you need to Have the router DHCP do the static addresses so this way the Arp entries are stored properly and the router can access shares.
in LAN tab, DCHP server, Basic Config
IP Pool Starting Address 192.168.1.97
IP Pool Ending Address 192.168.1.254
and in LAN/DHCP tab enable "Enable Manual Assignment"
Look for a network PC MAC address that you want to manage as Static IP and assign static IP address that are from the static range pool of 192.168.1.99 next PC .98 and .97
For first PC assign .99 and so on.
if you need more PC set the IP pool to reserve all the PC's you want and do them one by one to make sure that the PC gets the address you want.
This way you let the router handle the static addresses and you will have any problems sharing files via the VPN. If you do not do this and assign IP address manually on the PC's it may happen that you cannot share files because the router ARP tables don't see that computer you are trying to access even though you can Ping that PC. Having the router do the static IP ensures a proper ARP table and making sure you get access to the PC's you want to.
Even if you have the PC have a dynamic IP from the router chances are you may still get into problems where you cannot see the shares because the IP address changed.
In the second part of the tutorial I show you how to setup firewall rules on windows PC in order to access shares properly.
Some features to explore;
Interface Type: TAP or TUN?
TUN is the preferred method because it supports windows, iOS, Android, Linux
You can file share SAMBA, remote desktop, print share etc.
You will have to configure windows firewall explained in the end of this article.
TAP supports windows but not iOS or Android.
by choosing TAP, you tell the VPN to make remote machines feel like they're on the LAN, with broadcast Ethernet packets and raw Ethernet protocols available for communicating with printers and file servers and for powering their Network Neighborhood display.
Great if you don't want to configure windows firewalls on each PC
Push LAN to clients: allows you to access your network via the tunnel,
such as remote desktop, file sharing and print sharing.
Direct clients to redirect internet traffic: If this feature is enabled all traffic will go via the router and depending on your bandwidth speeds it can be very slow on the clients receiving end.
Ideally the majority of users should keep the Redirect Internet Traffic option disabled. It means the remote client will still use his own WAN access for all Internet traffic, and only use the VPN tunnel when trying to access a resource in the home LAN network. This is what VPNs were originally designed to do.
Respond to DNS: enable this along with Advertise DNS to clients and when you connect you will be using the DNS of the VPN server.
Advertise DNS to clients: this needs to be enabled if you want to have access to file shares and remote computer access.
Manage Client-Specific Options: Using this option, you can have full bidirectional site-to-site TLS VPNs with no Custom Configuration or init scripts. I have never got this to work but here is how it's suppose to work;
Selecting this option displays a table where you fill in the Common Name (from when you generated the TLS certificates), subnet (optional), and netmask (optional). If you fill in the subnet and netmask of the client, your server LAN will be able to communicate with your client LAN whenever it's connected (be sure not to choose the NAT option on the client router). Without this, you're stuck with just client->server communication.
If you select the "Allow Client<->Client" option, another checkbox appears in the table that, when selected, allows other clients (or client LANs) to communicate with this client LAN. So, now you can have multiple sites all connected together with communication between any of them as desired.
An "allow only these clients" option is also present. With this selected, clients that aren't in the table are not allowed to connect. If you want to allow a client that doesn't have a LAN behind it (or you don't want to allow access to it), just put it in the table and leave the subnet/netmask blank.
With these options, this release removed the biggest limitation that's been present since the first release: having the VPN limited to client-initiated connections.
You can further customize the VPN server by changing its server port other than the default 1194 and change the auth digest and encryption cipher to whatever you want
AES-128-CBC and auth digest to SHA1 is sufficient encryption for maintaining a proper security when connecting to your Server. Howerver feel free to change to whatever encryption or cipher that suites your needs.
Now that the server is running you need to setup your devices to use the VPN server.
***it is very important that any device you use to connect to the VPN Server must have a different subnet then the router otherwise you will not be able to see the networks if you enable Push LAN to clients
Example:
Router A VPN Server IP 192.168.1.1
Router B VPN Client IP 192.168.2.1
Look for the Export button under the General menu and click on it.
it will create a .ovpn file which you will need to configure your devices.
This client1.ovpn file contains everything you need including certificates.
For Android:
Download the OpenVPN app and install it on your device.
Teather your Android device to a computer and copy the client1.ovpn file to your device. Preferably the download folder.
Start the OPENVPN app and then on the top right there are 3 vertical dots, click on the dots and choose import then import profile from SD card, use ES file manager, if you don't have that program download it from the playstore and navigate to the download folder and import that client1.ovpn to openvpn app.
Once you have done that, simply hit on connect and you should have connection established to the VPN server.
AUSUS routers with stock firmware:
You can also import the client1.ovpn into another ASUS router with stock or Merlin Firmware VPN client. It will automatically configure everything you need to connect to the VPN Server, including certificates.
Simply go to the VPN client on your ASUS router and look for "Import .ovpn file" use the browse button to find the client1.ovpn file then click on upload.
That's it. you should be ready to connect. Turn the service state button to ON
You can enable start to WAN option if you want the Client to automatically connect to the VPN server when router gets rebooted.
Make sure that the client router has a different IP then the Server Router or you will not be able to see shares or print.
AUSUS routers with Merlin firmware:
Follow the exact steps as with ASUS stock firmware. With Merlin you need to set Accept DNS Configuration to Exclusive.
MAC:
A popular OpenVPN client for MacOSX is
Tunnelblick. It can be obtained for free from
https://tunnelblick.net. Follow these basic steps to use Tunnelblick with OpenVPN Access Server:
- Download the Tunnelblick disk image file (a ".dmg" file) from https://tunnelblick.net
- Open the downloaded disk image file (which mounts the disk image).
- Double-click the Tunnelblick icon (it may be labelled "Tunnelblick.app") and you will be guided through the installation of the program.
- Once you have installed Tunnelblick, you can download and install the configuration file. After logging in to the Access Server's Client Web Server, download the client.ovpn file and double-click it. This will launch Tunnelblick if necessary, and Tunnelblick will install and secure the configuration.
- Run Tunnelblick by double-clicking its icon in the Applications folder. If left running when you logout or shut down your computer, Tunnelblick will be launched automatically when you next log in or start your computer.
The first time Tunnelblick is run on a given Mac, it will ask the user for the an system administrator's username and password. This is necessary because Tunnelblick must have root privileges to run, as it modifies network settings as part of connecting to the VPN.
For more information on using Tunnelblick, see the Using Tunnelblick at
https://tunnelblick.net/czUsing.html.
Please go to section B of the article for more.