Hi,
Unnecessarily complicated explanation alert, all pretty new to me ...
I am in the process of planning future upgrades of my ISP at a remote site (to above 1GB) and with a few planned 2.5GB WAN/LAN routers/nodes I am in the market for a 2.5GB Switch. The question I have (I will explain the Topology below) is whether or not it needs to be a managed switch? In this note I am using Asus-Merlin on various ASUS Routers/Nodes; and plan a TP Link Switch.
Background:
At my local site, I have experimented setting up two VLANs Guest (52) and IoT (53), plus the Primary Network, but only configured one of them to an Ethernet Port, in "Access Mode" for the SDN IoT VLAN (53). My local Mesh node is connected via Wifi Backhaul, hence no other Ethernet Port setting is needed for that one wireless VLAN Guest (52) for either main or node.
LAN Port 2 then goes to an unmanaged 8 Port Switch, which (only) feeds a number of wired IoT devices, all on VLAN (53). My understanding is that Access ports are also known as “untagged” ports, since an access port will "strip the VLAN tag from the packet" i.e. for my case it doesn't really matter (or care) about the Tag identifier as there is only one VLAN (this begs the question whether I really even need to define a mode or SDN for that LAN Port 2 for my local setup, as I am not sending DIFFERENT Tags down one line (nor do I have different LAN cables feeding that 8 port switch)?
Planned Topology at Remote Site:
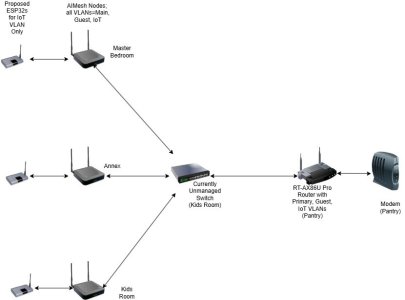
In any case the Topology at the Remote site is a bit different, essentially ISP -> WAN of Router, then out via ONE LAN Cable to an 8 Port Switch. The switch then has 5 Ethernet lines, one to each of 5 rooms, each with an AIMESH Node at the end (say).
Note that I do not need a different VLAN for different rooms; they all get all 3 VLANs. I would like to set up a Guest and IoT VLAN on the Router and also have the Primary Network (so 3 VLANs), all feeding all the nodes. In this case, let's say the LAN Cable goes from Port 2 of the Router to the switch, what do I choose for Mode and SDN Profile?
Clearly I cannot select "Access" as this is only for ONE VLAN Profile (although it is stripped anyway??), so this leaves either (a) "All (Default)/"Default" OR (b) "Trunk/Allow all Tagging".
Would it be correct that for (b) I would need a MANAGED SWITCH so the Tags are retained?
However if I want all VLANs to go to all Nodes, is it correct to say I do not need actually need any tagging so "All (Default)/"Default" is the correct setting?
And presumably I would not even need a managed switch?
Bonus scenario:
If at some stage I wanted to send separate VLANs to separate rooms, e.g. VLAN 52 to two rooms and VLAN 53 to two rooms (and Main to all 5 rooms), would it be correct that I would need a managed switch to do this and then would I select "Trunk/Allow all Tagging" and in the switch, assign the VLAN IDs for the rooms I wanted to send the respective VLANs to?
Thank you .
.
Unnecessarily complicated explanation alert, all pretty new to me ...
I am in the process of planning future upgrades of my ISP at a remote site (to above 1GB) and with a few planned 2.5GB WAN/LAN routers/nodes I am in the market for a 2.5GB Switch. The question I have (I will explain the Topology below) is whether or not it needs to be a managed switch? In this note I am using Asus-Merlin on various ASUS Routers/Nodes; and plan a TP Link Switch.
Background:
At my local site, I have experimented setting up two VLANs Guest (52) and IoT (53), plus the Primary Network, but only configured one of them to an Ethernet Port, in "Access Mode" for the SDN IoT VLAN (53). My local Mesh node is connected via Wifi Backhaul, hence no other Ethernet Port setting is needed for that one wireless VLAN Guest (52) for either main or node.
LAN Port 2 then goes to an unmanaged 8 Port Switch, which (only) feeds a number of wired IoT devices, all on VLAN (53). My understanding is that Access ports are also known as “untagged” ports, since an access port will "strip the VLAN tag from the packet" i.e. for my case it doesn't really matter (or care) about the Tag identifier as there is only one VLAN (this begs the question whether I really even need to define a mode or SDN for that LAN Port 2 for my local setup, as I am not sending DIFFERENT Tags down one line (nor do I have different LAN cables feeding that 8 port switch)?
Planned Topology at Remote Site:
In any case the Topology at the Remote site is a bit different, essentially ISP -> WAN of Router, then out via ONE LAN Cable to an 8 Port Switch. The switch then has 5 Ethernet lines, one to each of 5 rooms, each with an AIMESH Node at the end (say).
Note that I do not need a different VLAN for different rooms; they all get all 3 VLANs. I would like to set up a Guest and IoT VLAN on the Router and also have the Primary Network (so 3 VLANs), all feeding all the nodes. In this case, let's say the LAN Cable goes from Port 2 of the Router to the switch, what do I choose for Mode and SDN Profile?
Clearly I cannot select "Access" as this is only for ONE VLAN Profile (although it is stripped anyway??), so this leaves either (a) "All (Default)/"Default" OR (b) "Trunk/Allow all Tagging".
Would it be correct that for (b) I would need a MANAGED SWITCH so the Tags are retained?
However if I want all VLANs to go to all Nodes, is it correct to say I do not need actually need any tagging so "All (Default)/"Default" is the correct setting?
And presumably I would not even need a managed switch?
Bonus scenario:
If at some stage I wanted to send separate VLANs to separate rooms, e.g. VLAN 52 to two rooms and VLAN 53 to two rooms (and Main to all 5 rooms), would it be correct that I would need a managed switch to do this and then would I select "Trunk/Allow all Tagging" and in the switch, assign the VLAN IDs for the rooms I wanted to send the respective VLANs to?
Thank you