[Client cycled --> OFF --> ON after each individual change]
[Client ONE and desktop clients both OFF during testing. Using client TWO in an attempt to troubleshoot TWO independently from client ONE via PIA tech support *not overly useful thus far; they just keep regurgitating Tier I response protocols. I don't want to be *that* guy applying two different sources that interfere with fixing the actual problem.]
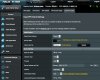
server set back to us-east...
Accept DNS Config set from Disabled --> Strict
TLS Renegotiation Time from 120 --> default of -1
Connection Retry from -1 --> 30
Encryption set to Blowfish-CBC
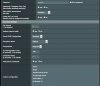
Replaced custom config with:
-------
auth SHA1
mute-replay-warnings
verb 3
inactive 0
keepalive 5 60
-------
CA.crt verified in the second position - no ego here; I'd even prefer someone to point out that I was doing something silly like having an ON/OFF problem!
Redirect Internet Traffic --> Yes
**Definitely appears to be an inbound read problem. VPN Status hangs at 70 bytes written, 0 read.
[------Most recent log-----]
Dec 4 23:39:40 rc_service: httpd 367:notify_rc start_vpnclient2
Dec 4 23:39:40 kernel: tun: Universal TUN/TAP device driver, 1.6
Dec 4 23:39:40 kernel: tun: (C) 1999-2004 Max Krasnyansky <maxk@qualcomm.com>
Dec 4 23:39:40 openvpn[5120]: OpenVPN 2.3.4 mipsel-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Nov 20 2014
Dec 4 23:39:40 openvpn[5120]: library versions: OpenSSL 1.0.0o 15 Oct 2014, LZO 2.08
Dec 4 23:39:40 openvpn[5120]: WARNING: No server certificate verification method has been enabled. See
http://openvpn.net/howto.html#mitm for more info.
Dec 4 23:39:40 openvpn[5120]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Dec 4 23:39:40 openvpn[5120]: Socket Buffers: R=[118784->131072] S=[118784->131072]
Dec 4 23:39:40 openvpn[5124]: UDPv4 link local: [undef]
Dec 4 23:39:40 openvpn[5124]: UDPv4 link remote: [AF_INET]209.222.18.43:1194
Dec 4 23:40:12 openvpn[5124]: event_wait : Interrupted system call (code=4)
Dec 4 23:40:12 openvpn[5124]: OpenVPN STATISTICS
Dec 4 23:40:12 openvpn[5124]: Updated,Thu Dec 4 23:40:12 2014
Dec 4 23:40:12 openvpn[5124]: TUN/TAP read bytes,0
Dec 4 23:40:12 openvpn[5124]: TUN/TAP write bytes,0
Dec 4 23:40:12 openvpn[5124]: TCP/UDP read bytes,0
Dec 4 23:40:12 openvpn[5124]: TCP/UDP write bytes,70
Dec 4 23:40:12 openvpn[5124]: Auth read bytes,0
Dec 4 23:40:12 openvpn[5124]: pre-compress bytes,0
Dec 4 23:40:12 openvpn[5124]: post-compress bytes,0
Dec 4 23:40:18 openvpn[5124]: event_wait : Interrupted system call (code=4)
Dec 4 23:40:18 openvpn[5124]: OpenVPN STATISTICS
Dec 4 23:40:18 openvpn[5124]: Updated,Thu Dec 4 23:40:18 2014
Dec 4 23:40:18 openvpn[5124]: TUN/TAP read bytes,0
Dec 4 23:40:18 openvpn[5124]: TUN/TAP write bytes,0
Dec 4 23:40:18 openvpn[5124]: TCP/UDP read bytes,0
Dec 4 23:40:18 openvpn[5124]: TCP/UDP write bytes,70
Dec 4 23:40:18 openvpn[5124]: Auth read bytes,0
Dec 4 23:40:18 openvpn[5124]: pre-compress bytes,0
Dec 4 23:40:18 openvpn[5124]: post-compress bytes,0
Dec 4 23:40:40 openvpn[5124]: [UNDEF] Inactivity timeout (--ping-restart), restarting
Dec 4 23:40:40 openvpn[5124]: SIGUSR1[soft,ping-restart] received, process restarting
Dec 4 23:40:40 openvpn[5124]: Restart pause, 2 second(s)
Dec 4 23:40:42 openvpn[5124]: WARNING: No server certificate verification method has been enabled. See
http://openvpn.net/howto.html#mitm for more info.
Dec 4 23:40:42 openvpn[5124]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Dec 4 23:40:42 openvpn[5124]: Socket Buffers: R=[118784->131072] S=[118784->131072]
Dec 4 23:40:43 openvpn[5124]: UDPv4 link local: [undef]
Dec 4 23:40:43 openvpn[5124]: UDPv4 link remote: [AF_INET]209.222.18.67:1194
Dec 4 23:41:06 openvpn[5124]: event_wait : Interrupted system call (code=4)
Dec 4 23:41:06 openvpn[5124]: OpenVPN STATISTICS
Dec 4 23:41:06 openvpn[5124]: Updated,Thu Dec 4 23:41:06 2014
Dec 4 23:41:06 openvpn[5124]: TUN/TAP read bytes,0
Dec 4 23:41:06 openvpn[5124]: TUN/TAP write bytes,0
Dec 4 23:41:06 openvpn[5124]: TCP/UDP read bytes,0
Dec 4 23:41:06 openvpn[5124]: TCP/UDP write bytes,56
Dec 4 23:41:06 openvpn[5124]: Auth read bytes,0
Dec 4 23:41:06 openvpn[5124]: pre-compress bytes,0
Dec 4 23:41:06 openvpn[5124]: post-compress bytes,0
Dec 4 23:41:37 openvpn[5124]: event_wait : Interrupted system call (code=4)
Dec 4 23:41:37 openvpn[5124]: OpenVPN STATISTICS
Dec 4 23:41:37 openvpn[5124]: Updated,Thu Dec 4 23:41:37 2014
Dec 4 23:41:37 openvpn[5124]: TUN/TAP read bytes,0
Dec 4 23:41:37 openvpn[5124]: TUN/TAP write bytes,0
Dec 4 23:41:37 openvpn[5124]: TCP/UDP read bytes,0
Dec 4 23:41:37 openvpn[5124]: TCP/UDP write bytes,70
Dec 4 23:41:37 openvpn[5124]: Auth read bytes,0
Dec 4 23:41:37 openvpn[5124]: pre-compress bytes,0
Dec 4 23:41:37 openvpn[5124]: post-compress bytes,0
Dec 4 23:41:43 openvpn[5124]: [UNDEF] Inactivity timeout (--ping-restart), restarting
Dec 4 23:41:43 openvpn[5124]: SIGUSR1[soft,ping-restart] received, process restarting
Dec 4 23:41:43 openvpn[5124]: Restart pause, 2 second(s)
Dec 4 23:41:45 openvpn[5124]: WARNING: No server certificate verification method has been enabled. See
http://openvpn.net/howto.html#mitm for more info.
Dec 4 23:41:45 openvpn[5124]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Dec 4 23:41:45 openvpn[5124]: Socket Buffers: R=[118784->131072] S=[118784->131072]
Dec 4 23:41:45 openvpn[5124]: UDPv4 link local: [undef]
Dec 4 23:41:45 openvpn[5124]: UDPv4 link remote: [AF_INET]108.61.55.77:1194