Builder71
Very Senior Member
OpenVPN supports different authentication schemes. The one you describe implies username/password or static key authentication, which isn't as secure as the TLS key/cert authentication method. That one requires you to manually generate and provides certs that are signed by your CA key to your users.
Nope, I don't use username/password or static key.
I use TLS key/cert authentication.
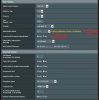
If you click on the "Content modification of Keys & Certificates" link, you will find the router populates all this automagically.
I just put in my own keys and after that the "Export" button doesn't work properly anymore.
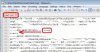
The logging shows it's still looking for some router generated certificate. (C=TW, ST=TW, L=Taipei, O=ASUS,)
Code:
Nov 26 20:19:10 openvpn[473]: TCP connection established with [AF_INET]10.0.0.236:51711
Nov 26 20:19:10 openvpn[473]: 10.0.0.236:51711 TLS: Initial packet from [AF_INET]10.0.0.236:51711, sid=4916638f 05c0bc38
Nov 26 20:19:10 openvpn[473]: 10.0.0.236:51711 VERIFY ERROR: depth=0, error=unable to get local issuer certificate: C=TW, ST=TW, L=Taipei, O=ASUS, CN=client, emailAddress=me@myhost.mydomain
Nov 26 20:19:10 openvpn[473]: 10.0.0.236:51711 TLS_ERROR: BIO read tls_read_plaintext error: error:140890B2:SSL routines:SSL3_GET_CLIENT_CERTIFICATE:no certificate returned
Nov 26 20:19:10 openvpn[473]: 10.0.0.236:51711 TLS Error: TLS object -> incoming plaintext read error
Nov 26 20:19:10 openvpn[473]: 10.0.0.236:51711 TLS Error: TLS handshake failed
Nov 26 20:19:10 openvpn[473]: 10.0.0.236:51711 Fatal TLS error (check_tls_errors_co), restarting
Nov 26 20:19:10 openvpn[473]: 10.0.0.236:51711 SIGUSR1[soft,tls-error] received, client-instance restartingSo it seems TLS authentication works out of the box with the "Export" button.
How cool is that!
However if there are more users connecting to the VPN server, it seems better to me, to make your own (client) certificates.
Please correct me if I'm wrong.
Attachments
Last edited: