Hello everybody
I'm trying to configure a very simple OpenVPN setup,
in order to access Internet and LAN from my mobile phone.
I underline that I already did this many times in the recent past so... really no clue why now isn't working.
I'm using latest Merlin 384.7 b2.
For some unknown reason, my setup isn't working.
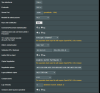
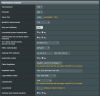
I attached it in the image below.
Logs aren't helping me, I don't find any error.
What happens:
VPN connection works.
If I disable "Inoltra DNS ai Client" (translated push DNS to clients),
I can browse the Internet (and, again for unknown reason, I expose to the internet my Mobile phone ISP IP, rather than the VPN one);
If I enable "Inoltra DNS ai Client", just nothing works.
Any hint?
Thanks everyone!
I'm trying to configure a very simple OpenVPN setup,
in order to access Internet and LAN from my mobile phone.
I underline that I already did this many times in the recent past so... really no clue why now isn't working.
I'm using latest Merlin 384.7 b2.
For some unknown reason, my setup isn't working.
I attached it in the image below.
Logs aren't helping me, I don't find any error.
What happens:
VPN connection works.
If I disable "Inoltra DNS ai Client" (translated push DNS to clients),
I can browse the Internet (and, again for unknown reason, I expose to the internet my Mobile phone ISP IP, rather than the VPN one);
If I enable "Inoltra DNS ai Client", just nothing works.
Any hint?
Thanks everyone!