madfusker
Regular Contributor
version 380.65_4
OpenVPN looks to be restarting over and over every 5 minutes or so and I cannot seem to fix it. I have found many thread with many attempts to fix it, but no solutions. I do have Policy Rules enabled. I run PIA with AES-256CBC however somewhere along the way it starting doing this and falling back to 64bit. Does anyone have any solutions to this problem?
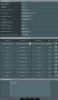
Apr 25 20:40:05 openvpn[1046]: WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1558', remote='link-mtu 1542'
Apr 25 20:40:05 openvpn[1046]: WARNING: 'cipher' is used inconsistently, local='cipher AES-128-CBC', remote='cipher BF-CBC'
Apr 25 20:43:07 openvpn[1024]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 25 20:43:07 openvpn[1024]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 25 20:43:07 openvpn[1024]: TUN/TAP device tun21 opened
Apr 25 20:43:07 openvpn[1024]: do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Apr 25 20:43:07 openvpn[1024]: /usr/sbin/ip link set dev tun21 up mtu 1500
Apr 25 20:43:07 openvpn[1024]: /usr/sbin/ip addr add dev tun21 local 10.8.0.1 peer 10.8.0.2
Apr 25 20:43:07 openvpn[1024]: Could not determine IPv4/IPv6 protocol. Using AF_INET6
Apr 25 20:43:07 openvpn[1024]: setsockopt(IPV6_V6ONLY=0)
Apr 25 20:43:07 openvpn[1024]: UDPv6 link local (bound): [AF_INET6][undef]:1194
Apr 25 20:43:07 openvpn[1024]: UDPv6 link remote: [AF_UNSPEC]
Apr 25 20:44:07 openvpn[1024]: Inactivity timeout (--ping-restart), restarting
Apr 25 20:44:07 openvpn[1024]: /usr/sbin/ip addr del dev tun21 local 10.8.0.1 peer 10.8.0.2
Apr 25 20:44:07 openvpn[1024]: SIGUSR1[soft,ping-restart] received, process restarting
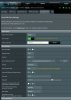
TUN
UDP
us-chicago.privateinternetaccess.com port 1198
TLS Disabled
Auth digest Default
Accept DNS Strict
LZO Adaptive
persist-key
persist-tun
tls-client
remote-cert-tls server
dhcp-option DNS 209.222.18.222
dhcp-option DNS 209.222.18.218
OpenVPN looks to be restarting over and over every 5 minutes or so and I cannot seem to fix it. I have found many thread with many attempts to fix it, but no solutions. I do have Policy Rules enabled. I run PIA with AES-256CBC however somewhere along the way it starting doing this and falling back to 64bit. Does anyone have any solutions to this problem?
Apr 25 20:40:05 openvpn[1046]: WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1558', remote='link-mtu 1542'
Apr 25 20:40:05 openvpn[1046]: WARNING: 'cipher' is used inconsistently, local='cipher AES-128-CBC', remote='cipher BF-CBC'
Apr 25 20:43:07 openvpn[1024]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 25 20:43:07 openvpn[1024]: WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Apr 25 20:43:07 openvpn[1024]: TUN/TAP device tun21 opened
Apr 25 20:43:07 openvpn[1024]: do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Apr 25 20:43:07 openvpn[1024]: /usr/sbin/ip link set dev tun21 up mtu 1500
Apr 25 20:43:07 openvpn[1024]: /usr/sbin/ip addr add dev tun21 local 10.8.0.1 peer 10.8.0.2
Apr 25 20:43:07 openvpn[1024]: Could not determine IPv4/IPv6 protocol. Using AF_INET6
Apr 25 20:43:07 openvpn[1024]: setsockopt(IPV6_V6ONLY=0)
Apr 25 20:43:07 openvpn[1024]: UDPv6 link local (bound): [AF_INET6][undef]:1194
Apr 25 20:43:07 openvpn[1024]: UDPv6 link remote: [AF_UNSPEC]
Apr 25 20:44:07 openvpn[1024]: Inactivity timeout (--ping-restart), restarting
Apr 25 20:44:07 openvpn[1024]: /usr/sbin/ip addr del dev tun21 local 10.8.0.1 peer 10.8.0.2
Apr 25 20:44:07 openvpn[1024]: SIGUSR1[soft,ping-restart] received, process restarting
TUN
UDP
us-chicago.privateinternetaccess.com port 1198
TLS Disabled
Auth digest Default
Accept DNS Strict
LZO Adaptive
persist-key
persist-tun
tls-client
remote-cert-tls server
dhcp-option DNS 209.222.18.222
dhcp-option DNS 209.222.18.218