EnF70
Occasional Visitor
Your existing rule does seem to do the trick.
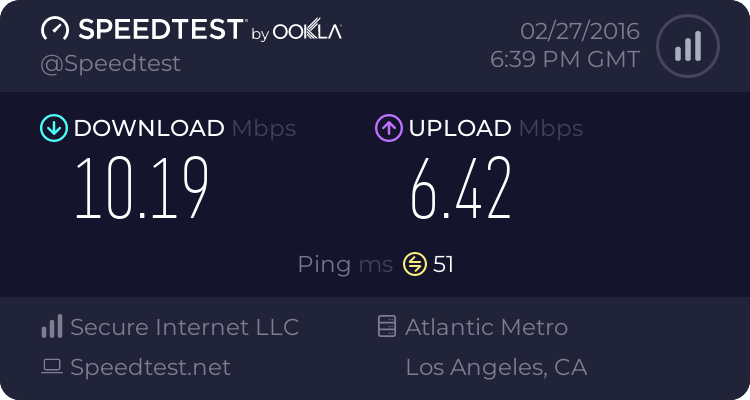
Also, I've tested with normal VPN traffic (outside VPN client <-> internal server) and I don't see any improvements in terms of speed or CPU usage when marking packets.
The only case I see improvements is when testing with Speedtest (which means routing all internet traffic through the VPN server and accessing outside servers)
I will test some more.
Also, I've tested with normal VPN traffic (outside VPN client <-> internal server) and I don't see any improvements in terms of speed or CPU usage when marking packets.
The only case I see improvements is when testing with Speedtest (which means routing all internet traffic through the VPN server and accessing outside servers)
I will test some more.