The forum software reports "The requested attachment could not be found."
One difference between yours and mine is that there are two extra lines in mine "Removing rule 1001 from routing policy" and "Removing rule 1201 from routing policy". I've attached my full system log file.
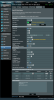
Yes, I deleted the openvpn-event script (immediately as soon as you mentioned the script as a possible party pooper). I changed from Exclusive to Relaxed but that didn't seem to make any difference. The 3 entries in custom config are created by loading the .ovpn file (which in turn is generated by AirVPN). See the attached snapshot of my screen.
(I can't get the forum software to display a readable image, so I shared it on tinypic):
http://i59.tinypic.com/akkis1.png
The default rules to be deleted can be seen to be added for VPN1, and correctly immediately deleted by RMerlin's script but the default rules appear to be added for VPN2...but NOT deleted?
Jul 19 22:16:32 openvpn[1028]: /usr/sbin/ip route add 0.0.0.0/1 via 10.4.0.1
Jul 19 22:16:32 openvpn[1028]: /usr/sbin/ip route add 128.0.0.0/1 via 10.4.0.1
Jul 19 22:16:32 openvpn-routing: Configuring policy rules for client 1
Jul 19 22:16:32 openvpn-routing: Creating VPN routing table
Jul 19 22:16:32 openvpn-routing: Removing route for 0.0.0.0/1 to tun11 from routing tables
Jul 19 22:16:32 openvpn-routing: Removing route for 128.0.0.0/1 to tun11 from routing tables
Jul 19 22:16:32 openvpn-routing: Removing rule 1001 from routing policy
Jul 19 22:16:32 openvpn-routing: Removing rule 1201 from routing policy
Jul 19 22:16:33 openvpn-routing: Added 172.16.0.1 to 0.0.0.0 through VPN to routing policy
Jul 19 22:16:33 openvpn-routing: Added 172.16.0.11 to 0.0.0.0 through WAN to routing policy
Jul 19 22:16:33 openvpn-routing: Tunnel re-established, restoring WAN access to clients
Jul 19 22:16:33 openvpn-routing: Completed routing policy configuration
Jul 19 22:16:33 openvpn[1028]: Initialization Sequence Completed
Jul 19 22:16:33 openvpn[1039]: /usr/sbin/ip route add 199.241.146.178/32 via 192.168.178.1
Jul 19 22:16:33 openvpn[1039]: /usr/sbin/ip route add 0.0.0.0/1 via 10.4.0.1
Jul 19 22:16:33 openvpn[1039]: /usr/sbin/ip route add 128.0.0.0/1 via 10.4.0.1
Jul 19 22:16:33 openvpn-routing: Configuring policy rules for client 2
Jul 19 22:16:33 openvpn-routing: Creating VPN routing table
Jul 19 22:16:33 openvpn-routing: Removing rule 1401 from routing policy
Jul 19 22:16:33 openvpn-routing: Removing rule 1601 from routing policy
Jul 19 22:16:33 openvpn-routing: Added 172.16.0.2 to 0.0.0.0 through VPN to routing policy
Jul 19 22:16:33 openvpn-routing: Added 172.16.0.21 to 0.0.0.0 through WAN to routing policy
Jul 19 22:16:33 openvpn-routing: Tunnel re-established, restoring WAN access to clients
Jul 19 22:16:33 openvpn-routing: Completed routing policy configuration
All I can suggest is that you disable the auto-start of the VPN Clients.
Reboot
On restart check the status of the RPDB rules and the route tables.
Then start VPN1 manually, and check the status of the RPDB tables and the route tables.
Nothing should be sent via VPN1.
Then start VPN2 manually, and check the status of the RPDB tables and the route tables.
Nothing should be sent via VPN1/VPN2.
If table 112 (contains tun11 entries) then I've no idea.