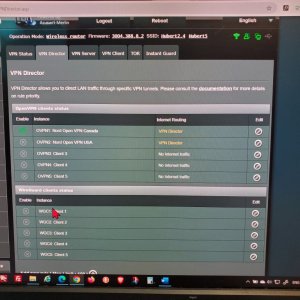
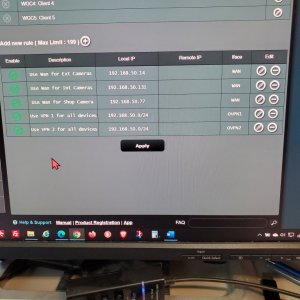
I had migrated from asuswrt to asuswrt-merling a few days ago to gain access to the Killswitch feature for my VPN's. After updating I built my two VPN's in VPN Client and then applied VPN Director policy rules on the Director page, first directing a couple devices straight to the WAN and the rest of my devices (From the assigned DHCP range of 192.168.50.2 t0 192.168.50.254) I assigned to use VPN client 1 OR 2 based on which is active. In the policy rules for VPN client 1 (CAN) & 2 (USA), I assigned the devices in the range 192.168.50.0/24 to use the OVPN client 1 or 2 respectively.
Unfortunately, I also turned on Killswitch so when I disabled my VPN's today to test I was immediatley logged out and locked out of the router interface as well as losing my internet access on all devices but those assigned to use the WAN. I was not able to ping the router at 192.168.50.1 so (as discussed in several other threads) I was forced to a reset and upload my last backup from yesterday which fortunately worked, only losing the rules.
For now, I can disable both VPN's and there are no failures. However, in an effort to get back to using Killswitch are there any best practices (such as redefining my LAN DHCP range and ensuring the router interface address is somehow protected in the rules) and are my rules correct as seen in image 1 and 2? I understand the purpose of Killswitch is to lock down access to the WAN when VPNs are down but I want to ensure I can protect access to the router interface at 192.168.50.1.
TIA
D.
Unfortunately, I also turned on Killswitch so when I disabled my VPN's today to test I was immediatley logged out and locked out of the router interface as well as losing my internet access on all devices but those assigned to use the WAN. I was not able to ping the router at 192.168.50.1 so (as discussed in several other threads) I was forced to a reset and upload my last backup from yesterday which fortunately worked, only losing the rules.
For now, I can disable both VPN's and there are no failures. However, in an effort to get back to using Killswitch are there any best practices (such as redefining my LAN DHCP range and ensuring the router interface address is somehow protected in the rules) and are my rules correct as seen in image 1 and 2? I understand the purpose of Killswitch is to lock down access to the WAN when VPNs are down but I want to ensure I can protect access to the router interface at 192.168.50.1.
TIA
D.