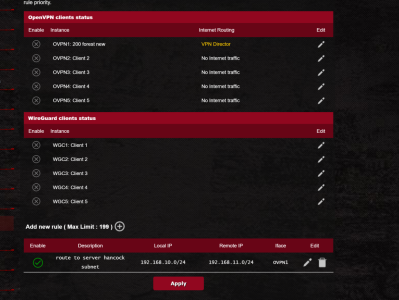
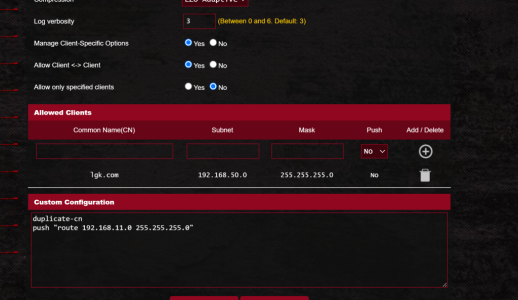
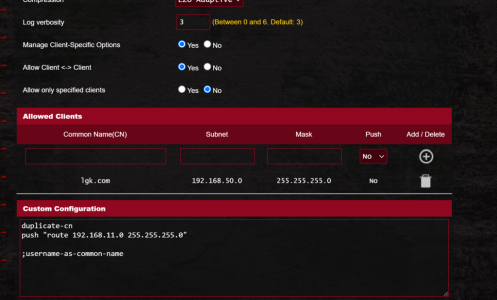
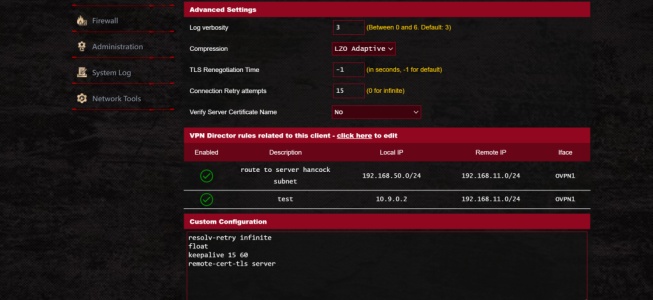
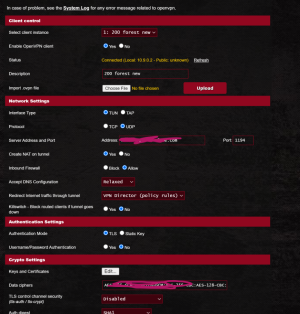
i was using vpn fusion for my system behind cg-nat.
once i setup the vpn it worked as i wanted all clients went out the vpn but only to access the specific remote subnet 192.168.11.0/24
any other destination packet went out to the normal wan..
on the flip side all clients on the remote/server side of the openvpn tunnel could ping and connect to the server on its 10.9.0.2 address..
what would be the rule in vpn director to get the same functionality.. ie only packets destined for the single remote subnet going out the vpn and the rest of the internet packets going out the wan and the 10.9.0.2 ip reacheable from clients on the server 192.168.11.0 subnet?
thanks in advance.
once i setup the vpn it worked as i wanted all clients went out the vpn but only to access the specific remote subnet 192.168.11.0/24
any other destination packet went out to the normal wan..
on the flip side all clients on the remote/server side of the openvpn tunnel could ping and connect to the server on its 10.9.0.2 address..
what would be the rule in vpn director to get the same functionality.. ie only packets destined for the single remote subnet going out the vpn and the rest of the internet packets going out the wan and the 10.9.0.2 ip reacheable from clients on the server 192.168.11.0 subnet?
thanks in advance.