Thank you for all of your replies. I won't be addressing all of you individually, but I hope what I do say reaches out to each of you as an answered question.
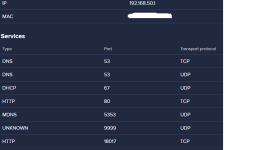
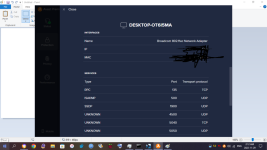
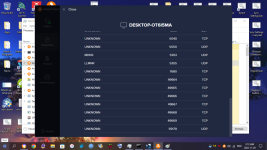
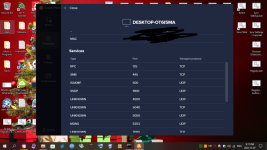
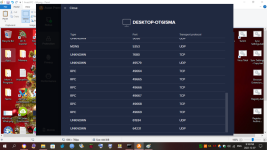
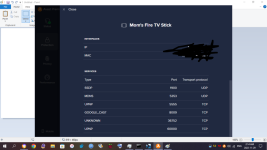
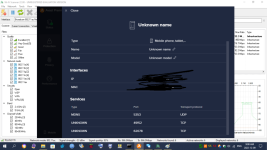
In January of this year, I found out I was hacked. My PC's, gaming devices, TV's, Cell Phones, anything that connected to the internet was hacked, essentially. Since then, I have analyzed the hackers methods to mitigate his attacks, but he is relentless and keeps getting in. Early on in the year, I detected he was using the Intel Management Engine to gain full access to my computer. I used a Raspberry Pi and 'flashrom' to remove the Management Engine from the BIOS chip with 'me_cleaner'. After that, I tried to work on the browser hijacks so I was going through the registry and modifying everywhere I could find that he had added his strings/extensions. While trying to clean the browser hijacks I was led to my System Certificates in the 'Microsoft Management Console" (MMC). In there, I saw he added rogue certificates and was using many of them to deploy malware on my system alongside browser hijacking certificates. I found I scanner that told me a bunch of certificates were questionable and I ended up deleting all of them. This step had stopped the attacker....for a few. I ended up creating a batch script, full of registry keys, that delete the certificates on a loop. I've been using that for a few months now, and I also bought a TPM 1.2 from China recently, but I don't exactly trust it will do as it is supposed to do with how hacked my system is. The attacker uses Microsoft Signed programs so he doesn't get detected by virus/malware scanners. In the last few days I started to look at my ports. Avast Network Inspector has given me some information on what ports are open for which device is connected. Some of the services have proper names like HTTP, DNS, DHCP, MDNS, etc etc, but some show up as "unknown". I have seen "unknown' show up over the months and it's usually an indicator of something is fracky. My PC showed 10-15 open ports in the 5x,xxx-6x,xxx ranges and the name was "unknown". I started to block them manually through Windows Firewall, but another one opened up immediately. After blocking about 30 of them, I drank another beer, and closed ports 49,152 - 65,535 individually (Excel spread sheet code. I don't trust the 'range' option). This shut down ports and uncovered names of the ports that were previously showing as 'unknown". The attacker compromised my RDC ports, which isn't good from what I read. I already knew he controllled Windows Update and I assume this was how. So, my RDC ports are still open, and I need them to run my system properly, and there are 7 of them open on ports 135, 49664-49669. I also see 'unknown' as a name of a port when an iPhone has been connected, as well as my Firestick shows one or two sometimes. The attacker can see and control any device that is connected to my network that he has hacked. I watched my iPhone tap buttons when I wasn't using it. My Firestick was clicking things that I wasn't doing. He is broadcasting my online device usage over the internet to select people, but could be more. He uses Microsoft Teams, which he hides in the background under disguised processes so I don't find them. I found one recently, "taskhostw.exe" was being used as the disguised app. He was just on my system before my last reboot (I reboot to kick him out and I hope it does til he can port frack me again). I have an indicator of when he's running the program, so I watch for it. Not sure what he uses on Firestick, but he's also streaming what is watched to the people who are attacking me. I am trying to work on closing all these ports to see if it kicks him out. Right now, the closed ports are technically closed, but the Network Inspector still shows them open when I run a scan. However, they change when I do a new scan, but not each time for the Firestick. Most of the time for the PC. Now the router...The router shows DNS, DNS, DHCP, HTTP, MDNS, UNKNOWN, and HTTP as the services open with the ports next to them. The one that alarms me is the "UNKNOWN" name and that is the one that has port 9999 UDP open. I went to the link that was posted above, and I do recognize that the finding could be a false positive......but in my current situation, I can't accept a false positive considering the evidence of other ports and me closing the ports to find changes that were made. A post above said it could be because I connected it through ethernet, which I did. I reset the modem and changed the firmware, but I had it plugged in to my infected PC. I did not try it through WiFi set up. My ISP's router gets hacked in seconds and I'm on my 3rd one. I need to get another one sent. There's a lot more to my story that I will leave out but I've been tracked, followed, baited and set up all through this year. I found two hidden cameras on me and I suspect I have hidden cameras inside and outside my house that I now live in (I moved far away). I built a RF Field Strength Meter, which does work, but it's not the right one to detect the cameras. I ordered new parts to build a new one using a different type of circuit. This is my life right now. I am looking for any help possible, please. I have pictures of the Network Scans which shows the 'Unknown" service with the ports next to it. I will attach pictures after I post this.
(I have contacted ASUS about my motherboard and router. I have only heard back about my motherboard and I assume it wont' be good news for the router either.)