Dear
ZebMcKayhan,
Unfortunately, I have to ask for your help again. After updating to the latest version (uf dev), the access of wg21 clients to wg11 rules stopped working
wg21 users from internet can connect to router, can access to lan and internet, but can't access to sites that in IPSet unblockip and wg11 rules (like 1 wg11 VPN Any 185.41.185.73)
From native LAN all is ok.
Router firmware - 386.7_2
WireGuard Mgr - v4.19b3
AdGuardHome - v1.5.7
wg_manager start/stop - no error
Code:
iptables -nvL POSTROUTING -t nat
Chain POSTROUTING (policy ACCEPT 6157 packets, 719K bytes)
pkts bytes target prot opt in out source destination
9 492 MASQUERADE all -- * wg11 192.168.0.0/24 0.0.0.0/0 /* WireGuard 'client' */
0 0 MASQUERADE all -- * wg11 10.50.1.0/24 0.0.0.0/0 /* WireGuard 'client wg21 to wg11' */
1 60 MASQUERADE all -- * br0 10.50.1.0/24 0.0.0.0/0 /* WireGuard 'server clients to LAN' */
26731 3911K PUPNP all -- * eth0 0.0.0.0/0 0.0.0.0/0
25608 3831K MASQUERADE all -- * eth0 !176.37.222.84 0.0.0.0/0
514 155K MASQUERADE all -- * br0 192.168.0.0/24 192.168.0.0/24
Code:
iptables -nvL FORWARD -t filter
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- eth0 * 0.0.0.0/0 224.0.0.0/4
233K 73M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2981 414K WGM_ACL_F all -- wg+ * 0.0.0.0/0 0.0.0.0/0 /* Wireguard ACL */
0 0 ACCEPT all -- br0 wg21 0.0.0.0/0 0.0.0.0/0 /* LAN to WireGuard 'server clients' */
282 71673 ACCEPT all -- wg21 * 0.0.0.0/0 0.0.0.0/0 /* WireGuard 'server' */
80500 9833K OVPNSF all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 other2wan all -- !br0 eth0 0.0.0.0/0 0.0.0.0/0
57 3468 ACCEPT all -- br0 br0 0.0.0.0/0 0.0.0.0/0
260 10946 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 state INVALID
80183 9818K NSFW all -- * * 0.0.0.0/0 0.0.0.0/0
32446 4146K ACCEPT all -- br0 * 0.0.0.0/0 0.0.0.0/0
47737 5672K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate DNAT
0 0 DNSFILTER_DOT tcp -- br+ * 0.0.0.0/0 0.0.0.0/0 tcp dpt:853
0 0 OVPNCF all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Code:
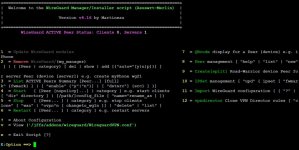
E:Option ==> peer wg11
Client Auto IP Endpoint DNS MTU Annotate
wg11 P 10.66.66.2/24,fd42:42:42::2/64 XXX:63665 8.8.8.8,8.8.4.4 1460 # N/A
Selective Routing RPDB rules
ID Peer Interface Source Destination Description
2 wg11 WAN 10.50.1.0/24 Any wg21UseWan
1 wg11 VPN Any 185.41.185.73
IPSet Enable Peer FWMark DST/SRC
unblockip Y wg11 0x1000 dst
WireGuard® ACTIVE Peer Status: Clients 1, Servers 1
Code:
E:Option ==> peer wg21
Server Auto Subnet Port Annotate
wg21 Y 10.50.1.1/24 51830 # RT-AC86U Server #1
Configuration rules for Peer wg21
PresharedKey = XXX
PresharedKey = XXX
PresharedKey = XXX
PresharedKey = XXX
PresharedKey = XXX
WireGuard® ACTIVE Peer Status: Clients 1, Servers 1